A flaw with the Sudo command used in macOS Terminal let non-privileged users and programs run commands as Root. It was patched in version 1.8.31 which was released with macOS High Sierra 10.13.6, macOS Mojave 10.14.6, and macOS Catalina 10.15.2 (via The Hacker News).
CVE-2019-18634
Tracked as CVE-2019-18364, the flaw opened a way for low-privileged users and malicious apps run commands as Sudo. Sudo is a powerful utility in Unix-based operating systems like macOS. It lets users run commands with the system privileges of a “superuser” or Root.
The flaw could only be exploited if a person has pwfeedback enabled in the sudoers configuration file. This option shows asterisks when you type your password in the terminal and isn’t enabled by default, at least on macOS. A user could trigger a stack-based buffer overflow, even by users without Sudo permissions.
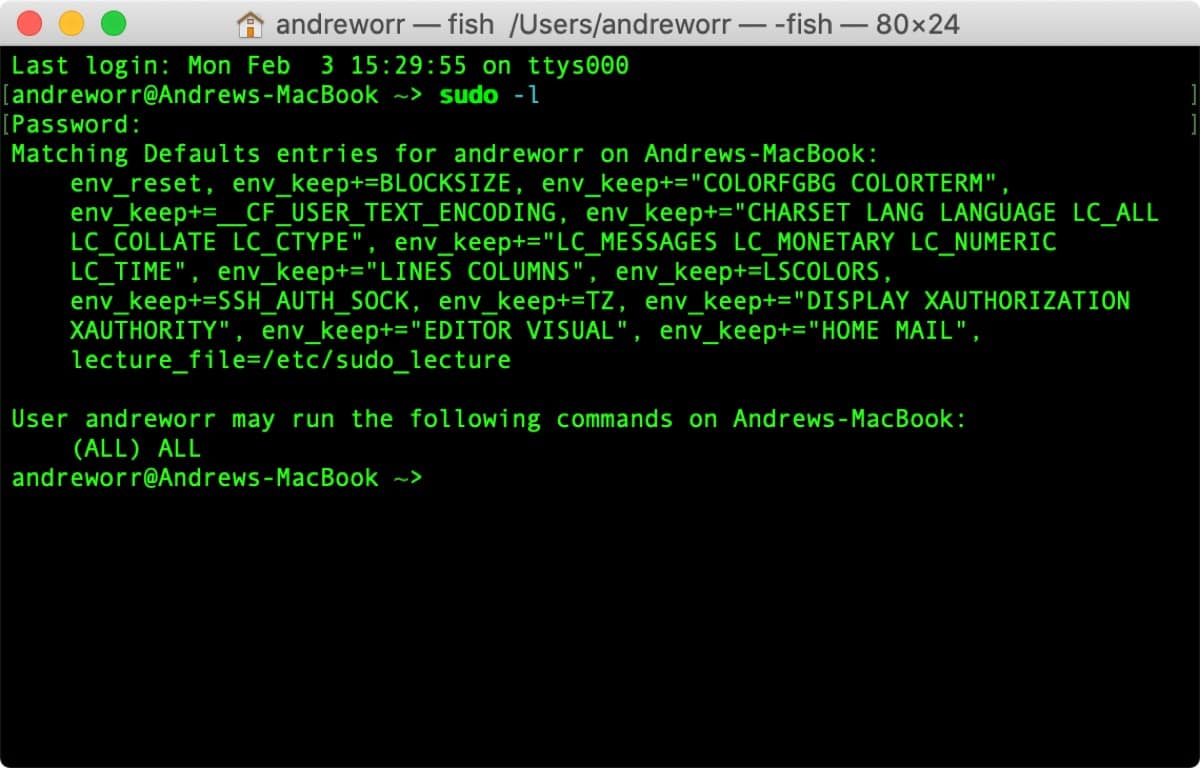
If you’ve updated to the latest version of macOS, you have the patch for this flaw. If not, just check to see if you have pwfeedback enabled:
sudo -l
Then, look for pwfeedback is listed under Matching Defaults entries. If it is, go to the sudoers configuration file and change Defaults pwfeedback to Defaults !pwfeedback.
Further Reading
[macOS: How to Access iCloud Drive in Terminal]
[The 5 Best Terminal Commands for Your Mac]
The sudo -l command seems to be case sensitive. sudo -L, as you have in the article, doesn’t work. sudo -l does work.
Aha, thanks for letting me know.