In this guide, we will help you fix unread message badge that won’t go away even when there aren’t any unread messages.
iMessage
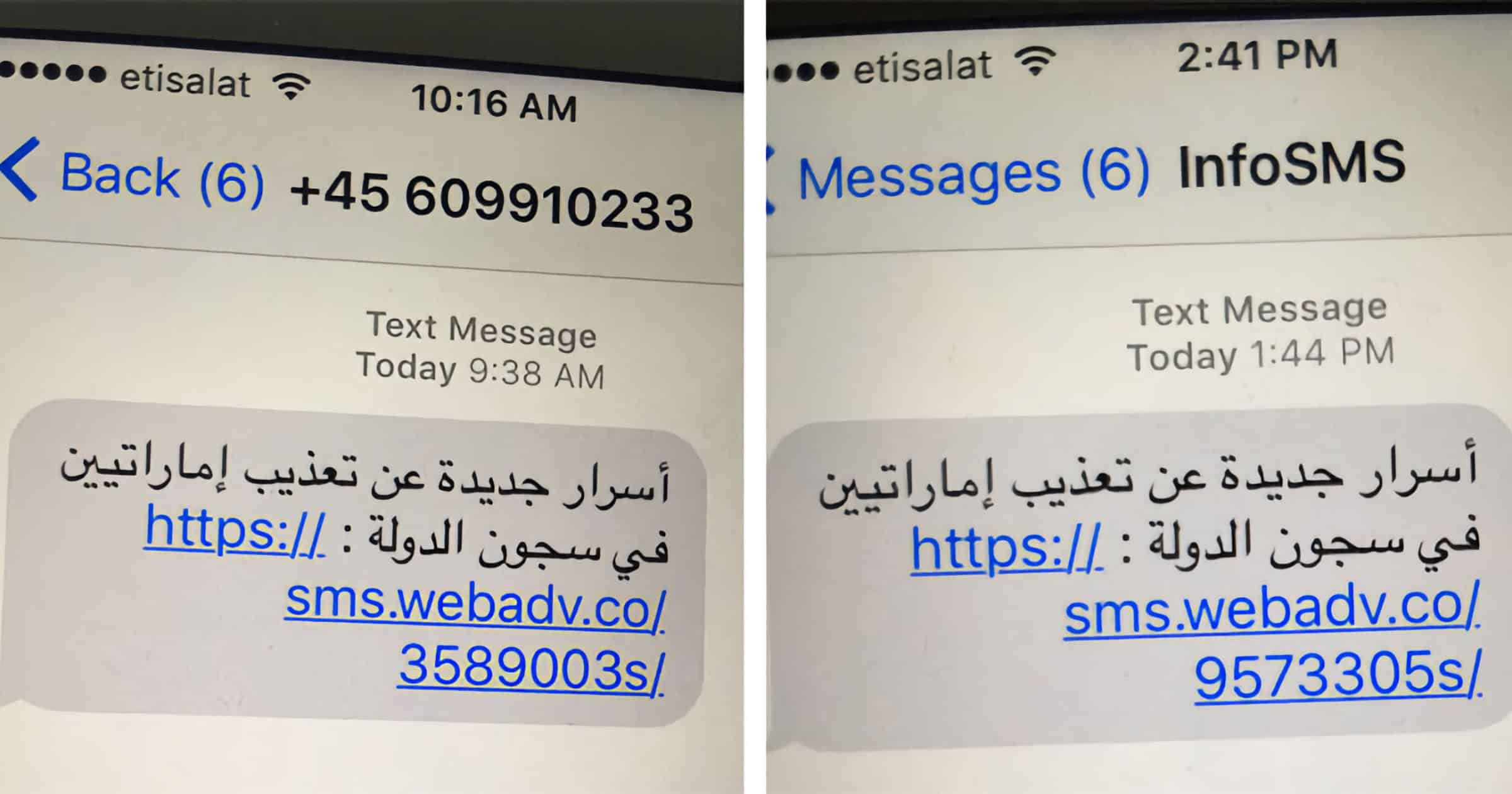
How To Recognize and Protect Yourself From an iMessage Scam
Learn about the various iMessage scams, how to recognize, block, and report them to Apple, and recover if you have fallen prey to a scam.
How to Prevent Network Provider Charges for FaceTime and iMessage Activation
Tom Victor offers tips to avoid unnecessary network provider charges for FaceTime and iMessage activation on your iPhone.
How To Fix iMessage Not Working for a Particular Contact Issue
Learn how to fix the ‘iMessage not working for a particular contact’ issue. If everything fails, we will learn how to send the it as an SMS.
How To Find and Delete Links from iPhone's 'Shared With You' Section on Safari
Learn how to find and delete Shared With You links on your Safari app. This article also shows how to disable the Shared With You feature.
What To Do When Mac Messages Are Not Syncing With iPhone
If you find your Mac messages are not syncing with your iPhone anymore, Jeff Butts has the solution to the problem.
Fix: iMessage and FaceTime Number Has Expired
Resolve the iMessage and FaceTime number expired issue with our step-by-step guide for reactivating your number.
Fix: Red Exclamation Mark on Message Icon
Seeing a red exclamation mark on Message. It means your message is not sent. Read to know how to fix red exclamation mark on iMessage.
11 Ways to Fix iMessage Not Working on iPhone
If you can’t send iMessages to your friends or if you’re facing green bubble issues with iMessage, here’s how to fix iMessage not working.
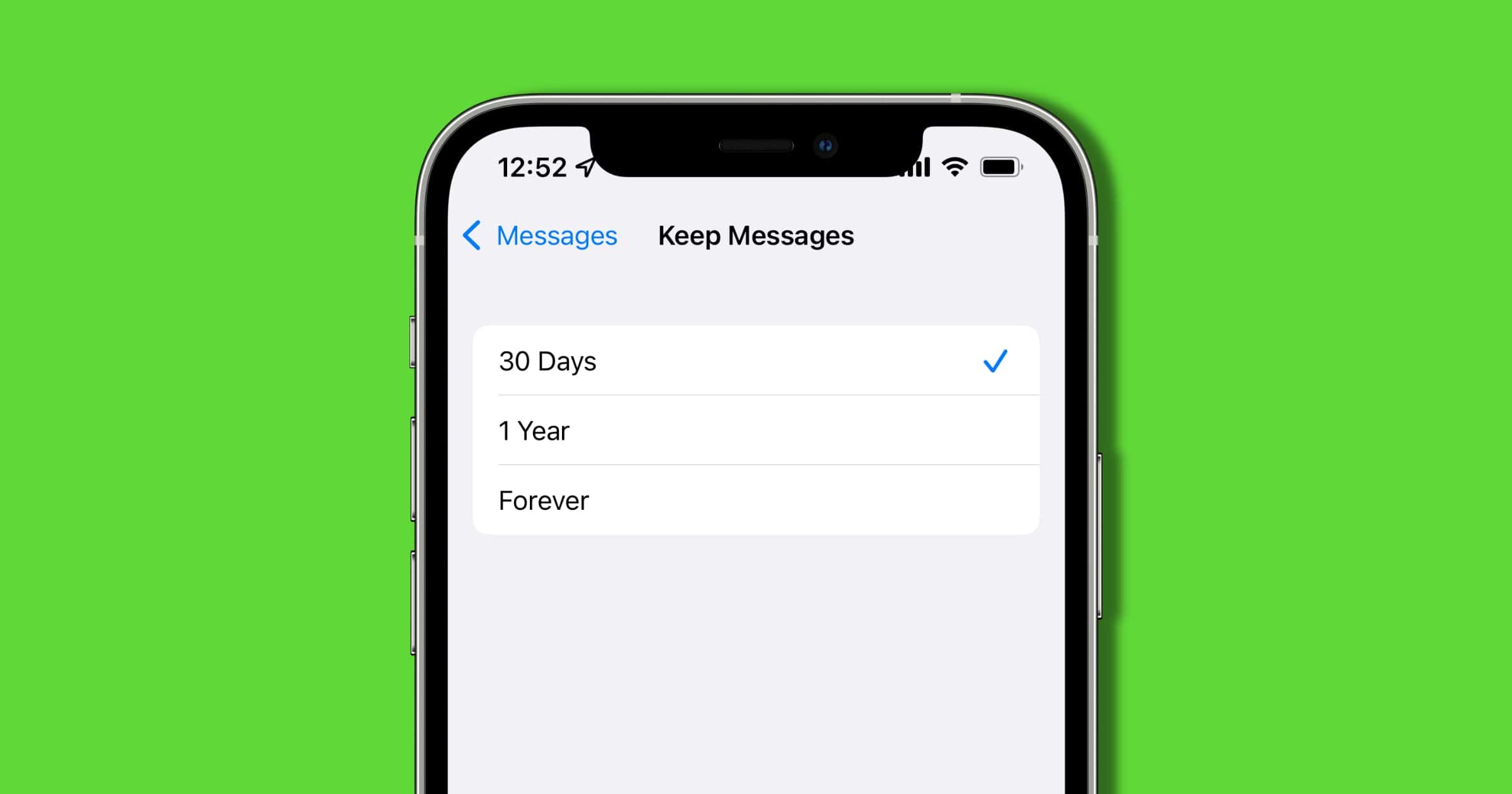
How to Fix 'Messages in iCloud Not Available' Error
Here are troubleshooting tips that you can follow to resolve the error message, “Messages in iCloud not available.”
Mailbag Monday! Now on Friday! - TMO Daily Observations 2023-03-03
TMO Managing Editor Jeff Butts and Ken bring Mailbag Monday back for a second round. Email on China, AirDrop, and Passcodes. First though, the EC wants every messaging app to interoperate with every other messaging app. The TDO duo has thoughts.
Insufferable ATMs and Planting Flags in the App Store - TMO Daily Observations 2023-02-22
The Financial Times seems torn between praise of Apple’s business acumen and disdain for some of its users. TMO writer Nick deCourville and Ken talk that over. Plus – Florida’s A.G. wants Apple to label apps with where they were developed… for safety?
But Just Wait 14 Months - TMO Daily Observations 2022-12-02
Want a positive spin on the current quarter? Ken tries to convince TMO Managing Editor Jeff Butts how great things will look for Apple in Q1FY24 – provided nothing goes wrong. Also – Android is getting one communications app to rule them all (and ditch the green text bubbles). Jeff fills us in on Sunbird.
Sunbird App Will Bring iMessage to Android, Ending Blue Bubble vs Green Bubble Bullying
The upcoming Sunbird app for Android will finally bring iMessage to those devices easily and quickly, hopefully ending blue bubble envy.
Tim Cook Makes Apple’s Stance on RCS Clear: Our Users Don’t Want It
Speaking at a developers’ conference, Apple CEO Tim Cook made it clear the iPhone maker’s users simply don’t care about RCS messaging.
Google Puts More Pressure on Apple to Adopt RCS with ‘Get the Message’ Campaign
In a new campaign, “Get the Message,” Google is once again calling on Apple to implement RSC support for the iPhone.
T-Mobile iPhone Users Plagued by iMessage Deactivation Due to eSim Bug
T-Mobile iPhone users report an iMessage deactivation problem likely caused by an eSIM bug. Only switching to a physical SIM resolves it.
Private Relay and Unified Messaging – TMO Daily Observations 2022-01-12
Andrew Orr and Jeff Butts join host Kelly Guimont to discuss an issue with iCloud Private Relay and the future of messaging on mobile devices.
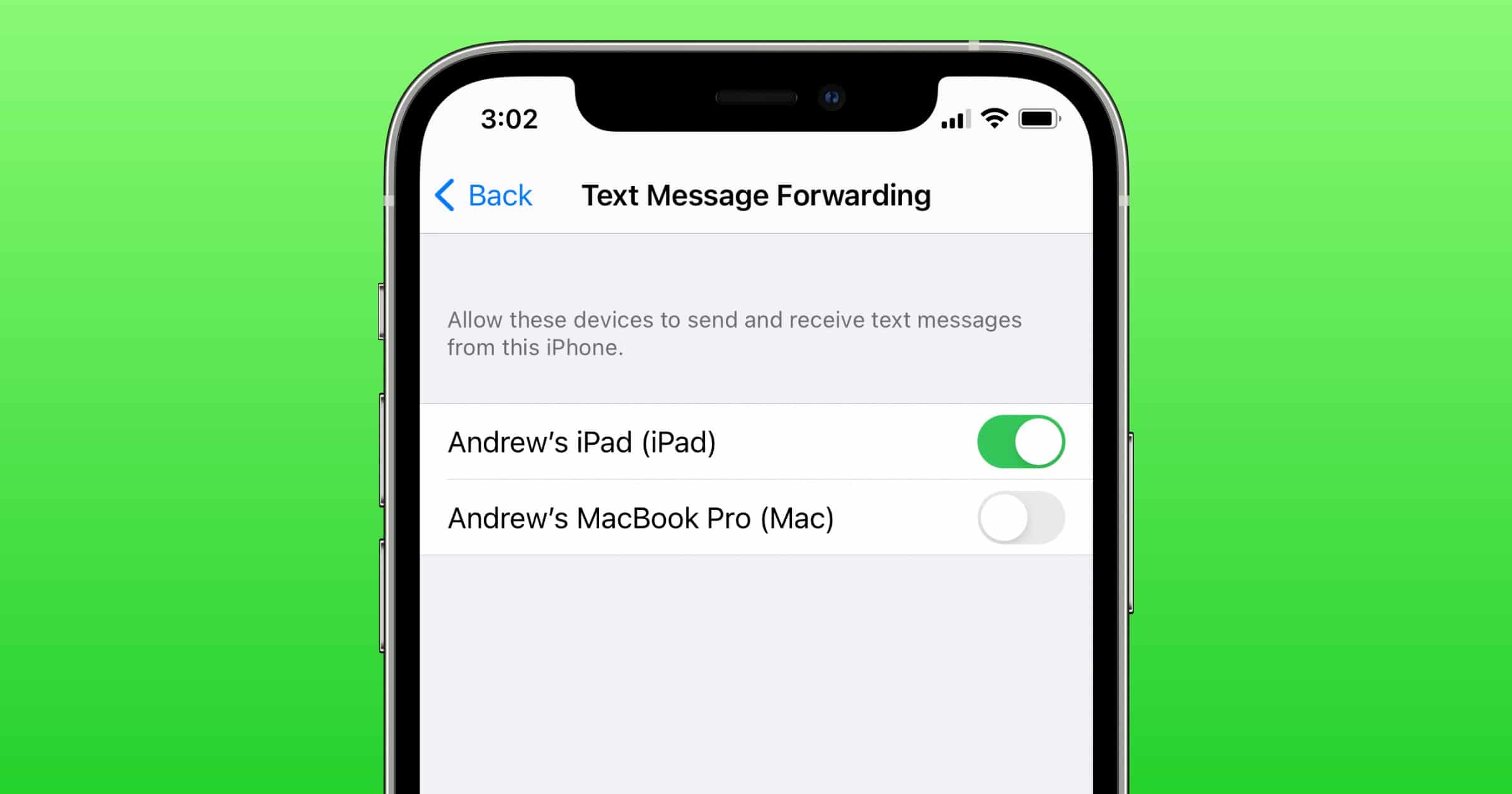
iOS: How to Forward Text Messages to Apple Devices
In part two of managing communications with multiple Apple devices, Andrew shows you how to forward text messages to other devices.
Google's Project Zero Deep Dives into NSO Group 'FORCEDENTRY' Exploit
Google’s Project Zero security team published a deep dive into FORCEDENTRY, a zero-click exploit in iMessage used by NSO Group. Apple’s Security Engineering and Architecture (SEAR) group collaborated on the analysis.
Based on our research and findings, we assess this to be one of the most technically sophisticated exploits we’ve ever seen, further demonstrating that the capabilities NSO provides rival those previously thought to be accessible to only a handful of nation states.
The vulnerability discussed in this blog post was fixed on September 13, 2021 in iOS 14.8 as CVE-2021-30860.
Security Friday: News, Shenanigans, and Encrypted Backups – TMO Daily Observations 2021-10-15
Andrew Orr joins host Kelly Guimont to discuss Security Friday news, including This Week In Data Breaches and willful misunderstanding of “hacking.”
How to Turn Off iMessage Apps and Stickers on Your iPhone
You can easily turn off iMessage apps and stickers if you don’t use them and want to declutter the interface.
iMessages are End-To-End Encrypted But iCloud Backups Are Not
For Lifehacker, Jake Peterson wrote a reminder that under certain circumstances, Apple can theoretically access your iMessages.
Here’s the tricky thing; Messages in iCloud is end-to-end encrypted, just as you’d expect—that’s why there’s no way to access your messages on the web, such as by logging in to icloud.com. There’s one big problem, though: your iCloud Backup isn’t end-to-end encrypted—and Apple stores the key to unlock your encrypted messages within that backup.
Messages in iCloud has been a thing for a few years now, but you can turn it off.
Apple Releases iOS 15 With Live Text, Shared With You, Focus, and More
Apple has officially released iOS 15 for customers on Monday, bringing plenty of fresh new features and quality-of-life upgrades.