Andrew Orr joins host Kelly Guimont to discuss Security Friday news and introduce a rating system for how worried to be about certain stories.
Malware
'EWDoor' Malware Attacks Thousands of AT&T Internet Subscribers
Hackers are exploiting a bug from 2017 to attack the EdgeMarc Enterprise Session Border Controller. This device is used by businesses to manage phone calls and video calls.
The vulnerability being exploited to infect the devices is tracked as CVE-2017-6079, a command-injection flaw that penetration tester Spencer Davis reported in 2017 after using it to successfully hack a customer’s network. The vulnerability stemmed from an account in the device that, as Davis learned from this document, had the username and password of “root” and “default.”
Hackers Infiltrate Website Belonging to Sealand, Skimming Payment Data
Hackers have infiltrated a website belonging to the Principality of Sealand, using a web skimmer to steal user data such as payment information.
'FinSpy' Spyware is Adept at Hiding Itself With a Four-Layer Method
FinSpy, a well-known piece of spyware from German company FinFisher, is good at hiding. Researchers at Kaspersky have reverse-engineered the malware.
In addition to a four-layer obfuscation method, the spyware also now employs a UEFI (Unified Extensible Firmware Interface) bootkit for infecting its targets, and it also encrypts the malware in memory, according to the researchers. The Kaspersky team’s research began in 2019, and they are finally sharing their findings today at Kaspersky’s online Security Analyst Summit.
Crypto Miners Most Detected Malware Type in 2021
A report on Tuesday found that crypto-mining malware was the most detected malware type in the first half of 2021.
The most active cryptocurrency miner in the first half of 2021 was MalXMR, with 44,587 detections. MalXMR is a crypto-mining malware that exploited EternalBlue for propagation and abused Windows Management Instrumentation (WMI). During the infection, high CPU utilization can be noticed with powershell.exe or schtasks.exe.
Pluggin a service I use: NextDNS. There’s a toggle you can turn on to “Prevent the unauthorized use of your devices to mine cryptocurrency.”
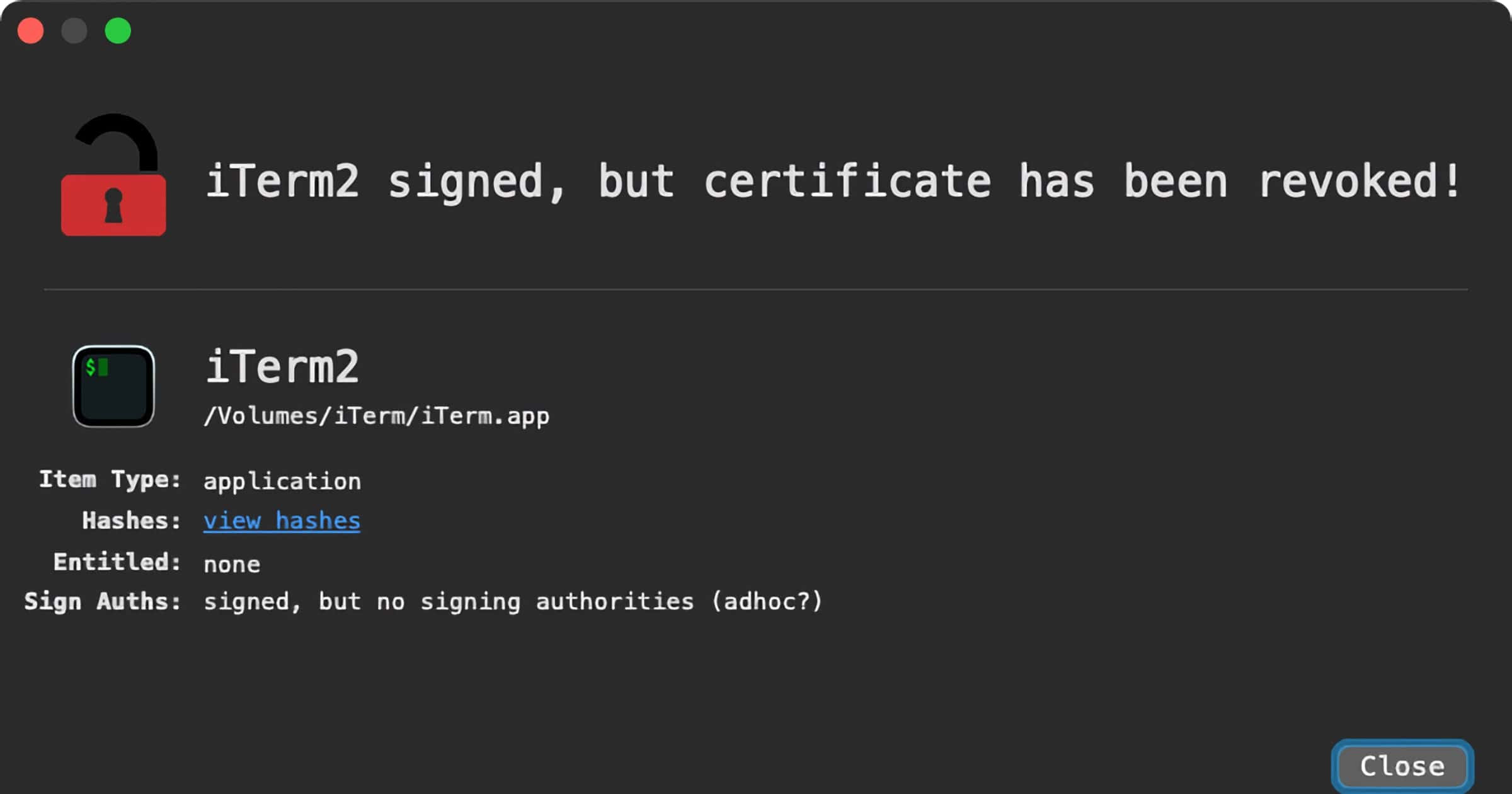
'OSX.ZuRu' Malware Spreads From Trojanized Apps via Sponsored Search Results
The latest Mac malware to be discovered is called OSX.ZuRu. It spreads via infected apps from sponsored search results.
The legitimate and the malicious iTerm2 application bundles contain a massive number of files, including several Mach-O binaries. Moreover, the malicious version appears largely benign (as is the case with most applications that have been surreptitiously trojanized). As such, it takes us a minute to uncover the malicious component.
Backup Tool ‘iMazing’ Updated to Detect Pegasus Spyware
The team behind iMazing has updated their tool to detect NSO Group’s Pegasus spyware. You don’t have to buy an iMazing license to scan for it.
It would therefore be possible to relatively quickly re-implement MVT’s methodology in our toolkit, and integrate a user-friendly ‘wizard’ in iMazing’s user interface. And because iMazing can already perform iOS backups and decrypt backup files, the tool we envisaged had the potential to dramatically reduce the technical barrier of entry whilst enhancing performance and promoting backup encryption.
Malware Dubbed ‘Raccoon Stealer’ Targets Crypto Wallets
Researchers at Sophos have been tracking a piece of malware called Raccoon Stealer. A recent update means it can target cryptocurrency wallets.
Raccoon can collect passwords, cookies, and the “autofill” text for websites, including credit card data and other personal identifying information that may be stored by the browser. Thanks to a recent “clipper” update, Raccoon Stealer also now targets cryptocurrency wallets, and can retrieve or drop files on infected systems.
Hackers Increasingly Using Discord to Spread Malware
Researchers found that hackers are turning to Discord to spread malware, such as password-hijacking and Discord chat bot APIs.
But the greatest percentage of the malware we found have a focus on credential and personal information theft, a wide variety of stealer malware as well as more versatile RATs. The threat actors behind these operations employed social engineering to spread credential-stealing malware, then use the victims’ harvested Discord credentials to target additional Discord users.
Researchers Hid Malware Inside an AI’s Brain
This is straight out of a sci-fi novel. Researchers created a proof-of-concept technique that let them hide malware inside of an AI’s neurons to avoid detection.
According to the paper, in this approach the malware is “disassembled” when embedded into the network’s neurons, and assembled into functioning malware by a malicious receiver program that can also be used to download the poisoned model via an update. The malware can still be stopped if the target device verifies the model before launching it, according to the paper. It can also be detected using “traditional methods” like static and dynamic analysis.
NSO Group’s ‘Pegasus’ Spyware Targets Journalists and Activists
Spyware known as Pegasus from NSO Group was used to hack 37 smartphones belonging to journalists, activists, and business executives around the world.
The phones appeared on a list of more than 50,000 numbers that are concentrated in countries known to engage in surveillance of their citizens and also known to have been clients of the Israeli firm, NSO Group, a worldwide leader in the growing and largely unregulated private spyware industry, the investigation found.
New Malware Infects Software Pirates and Blocks The Pirate Bay
Andrew Brandt reports on a new malware campaign that isn’t like your typical malware. This one blocks people from accessing many popular pirating websites.
We weren’t able to discern a provenance for this malware, but its motivation seemed pretty clear: It prevents people from visiting software piracy websites (if only temporarily), and sends the name of the pirated software the user was hoping to use to a website, which also delivers a secondary payload.
Looks like this is aimed more towards Windows users. The malware takes the form of .EXE executables, and may display a message saying the victim is missing an important .DLL file.
The Story of BonziBuddy and its Company’s Demise
In the third episode of Kernel Panic, Mashable tells the story of one of the first virtual assistants known as BonziBuddy.
Behind the facade of that friendly gorilla, Bonzi Software, the company responsible for BonziBuddy, was collecting private information and contacts from the unsuspecting internet users who downloaded it — and bombarding them with ads and pop-ups that Bonzi would profit from.
Harry Potter and the Curse of Bonzi. If you ever downloaded this purple ape and noticed strange things start to happen, let us know in the comments. Maybe your browser was full of ads, or maybe he whispered into your ear at night, encouraging you to commit securities fraud.
128 Million Apple Users Unknowingly Downloaded Malware in 2015
Emails published in the Epic v Apple trial on Friday revealed that 128 million users downloaded malware from the App Store in 2015.
Malvertising Campaign ‘Tag Barnakle’ Infected 120 Ad Servers
First discovered a year ago, malvertising campaign Tag Barnakle has infected over 120 ad servers to insert malicious code into ads.
Stein says that while last year Tag Barnakle had targeted users of desktop browsers with redirects to malware download sites, over the past year, the gang has switched to going after mobile users and redirecting them to online scams peddling various scammy products.
New ‘XcodeSpy’ Malware Targets Apple Developers
A new form of malware has been discovered that explicitly targets Apple developers. It’s called “XcodeSpy.”
How to Find Out if Your Mac has ‘Silver Sparrow’ Malware
Right now we know that Malwarebytes can detect it, and other anti-malware vendors will likely be updated soon.
Silver Sparrow and You – TMO Daily Observations 2021-02-22
Andrew Orr join host Kelly Guimont to discuss Silver Sparrow malware, including what it’s actually doing and how concerned you should be.
Mysterious ‘Silver Sparrow’ Malware Confuses Researchers
Over the weekend we got news of a mysterious piece of malware called Silver Sparrow. It has infected 30,000 machines so far and there is a version of it built for M1 Macs. But security researchers can’t figure out its purpose.
Once an hour, infected Macs check a control server to see if there are any new commands the malware should run or binaries to execute. So far, however, researchers have yet to observe delivery of any payload on any of the infected 30,000 machines, leaving the malware’s ultimate goal unknown. The lack of a final payload suggests that the malware may spring into action once an unknown condition is met.
Security Friday: Malware, Passwords, Security Guides – TMO Daily Observations 2021-02-19
Security Friday! Andrew Orr joins host Kelly Guimont to discuss security news and tips, including some new malware for the new M1 Mac.
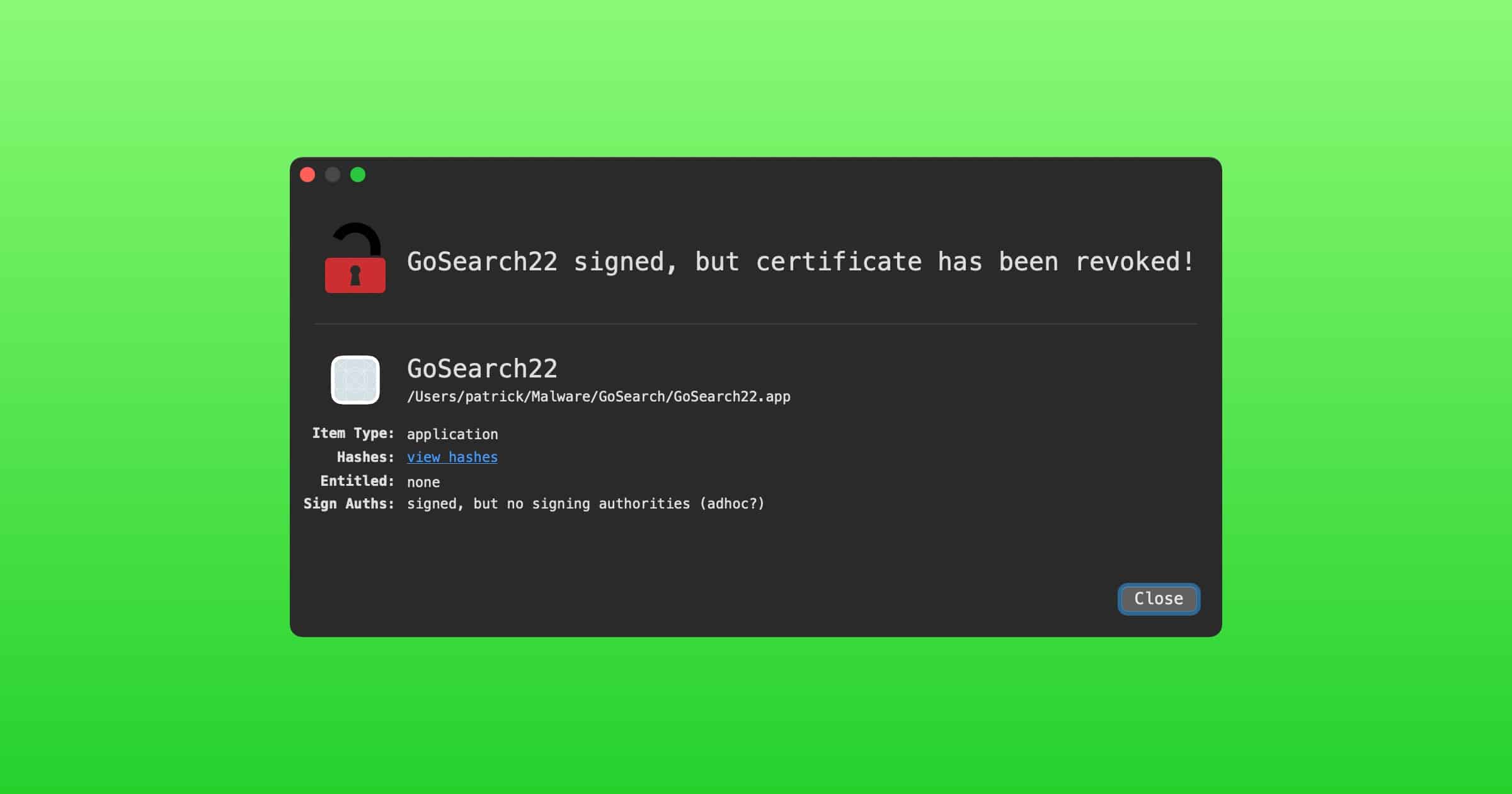
Safari Adware ‘GoSearch22’ Targets M1 Macs
Security researcher Patrick Wardle found a Safari adware extension called GoSearch22 has been rewritten to target M1 Macs.
‘ElectroRAT’ is the First Mac Malware Spotted in 2021
We’re barely a week into 2021 and a piece of Mac malware has already been spotted. Dubbed “ElectroRAT” its primary goal is to steal personal information from cryptocurrency users.
These [malicous] applications were promoted in cryptocurrency and blockchain-related forums such as bitcointalk and SteemCoinPan. The promotional posts, published by fake users, tempted readers to browse the applications’ web pages, where they could download the application without knowing they were actually installing malware.
Malware? Not Malware — Mac Geek Gab 841
Sometimes you feel like … a malware. Sometimes you don’t. That’s not how it goes, but that’s exactly how it felt for a lot of you this week! John and Dave talk through this and get to the bottom of it all. That’s hardly half of it, though. You know how Mac Geek Gab goes… your questions answered, your tips share, all with the goal of learning at least five new things along with your two favorite geeks!
HP Print Drivers Slash Malware – TMO Daily Observations 2020-10-27
John Martellaro joins host Kelly Guimont to discuss a technical issue that causes HP printer drivers to appear on your Mac as malware.