If you use a password or passcode to lock your phone, cops can’t make you unlock it. But if you use Face ID or Touch ID, they can force you.
Security
Beware! Hackers Are Using Fake CleanMyMac Installers To Steal Your Data
Beware! Scammers are now using fake CleanMyMac X installers in an attempt to obtain your personal data, including passwords.
Apple Users Get Hit by MFA Bombing Attacks That Exploit System Glitch
Beware! Don’t approve this Reset Password prompt, Apple users are being hit by an MFA bombing attack, exploiting a system glitch.
iPhone Call Failed? 13 Ways To Fix It
Learn how to fix the iPhone call failed immediately issue. Know the reasons behind why calls fail and easy ways to fix the issue.
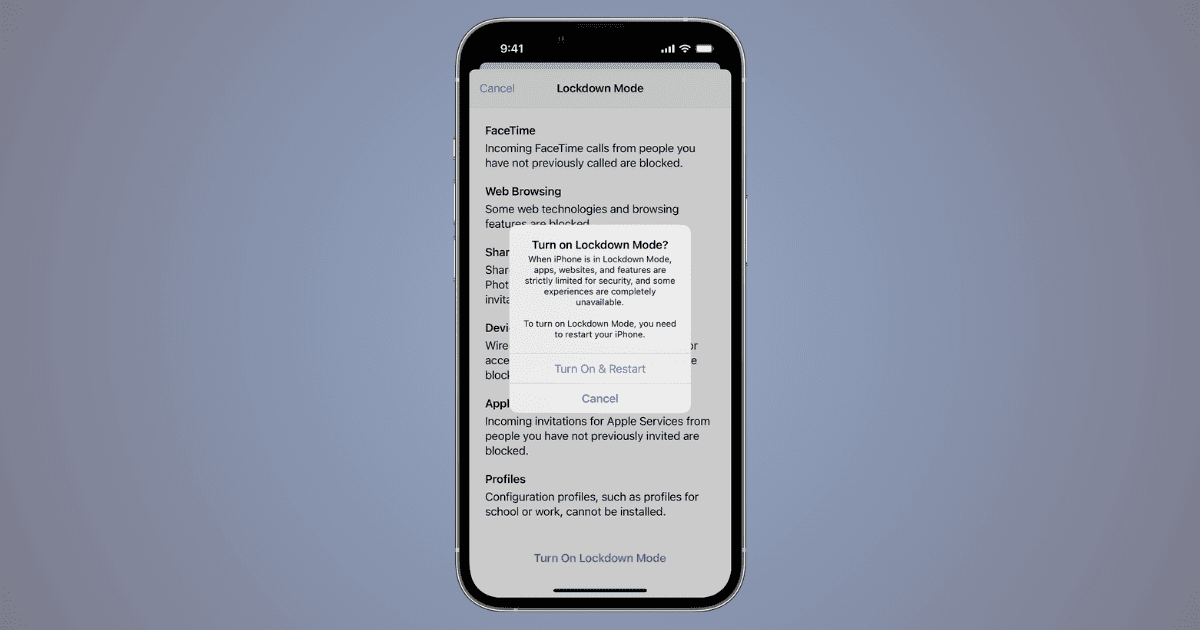
How To Use iPhone’s Lockdown Mode Against High-Profile Cyberattacks
Learn about the iPhone’s lockdown mode for enhanced security. Activate it easily and explore additional Apple device security tips.
How To Protect Your iPhone Number and Private Data
Need a comprehensive guide on how to protect your iPhone number and private data? Check out our guide which covers a variety of topics.
How to Configure USB & Thunderbolt Security in macOS
Discover Accessory Security Settings through a guide on macOS. Learn four different ways to configure USB and Thunderbolt security.
How to Delete Your Private Data from Apple's Servers
In order to delete your private data from Apple’s servers you need to delete your Apple ID. Alternatively can also learn how to deactivate it.
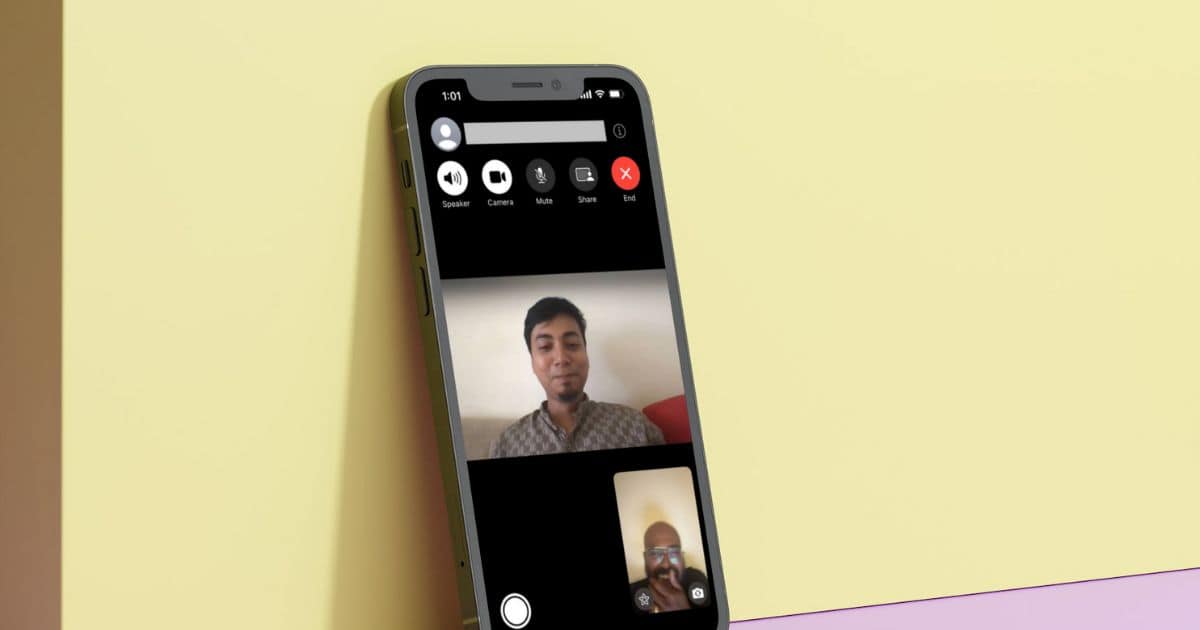
How to Turn FaceTime On / Off on Your iPhone: A Step-by-Step Guide
Learn how to turn off FaceTime on your iPhone and how to reactivate it. Turn off FaceTime for one contact and set a usage limit to FaceTime.
Here's How to Create an Apple ID Recovery Key on iPhone
Ensure the security of your Apple account as you follow our step-by-step guide to create an Apple ID recovery key on your iPhone.
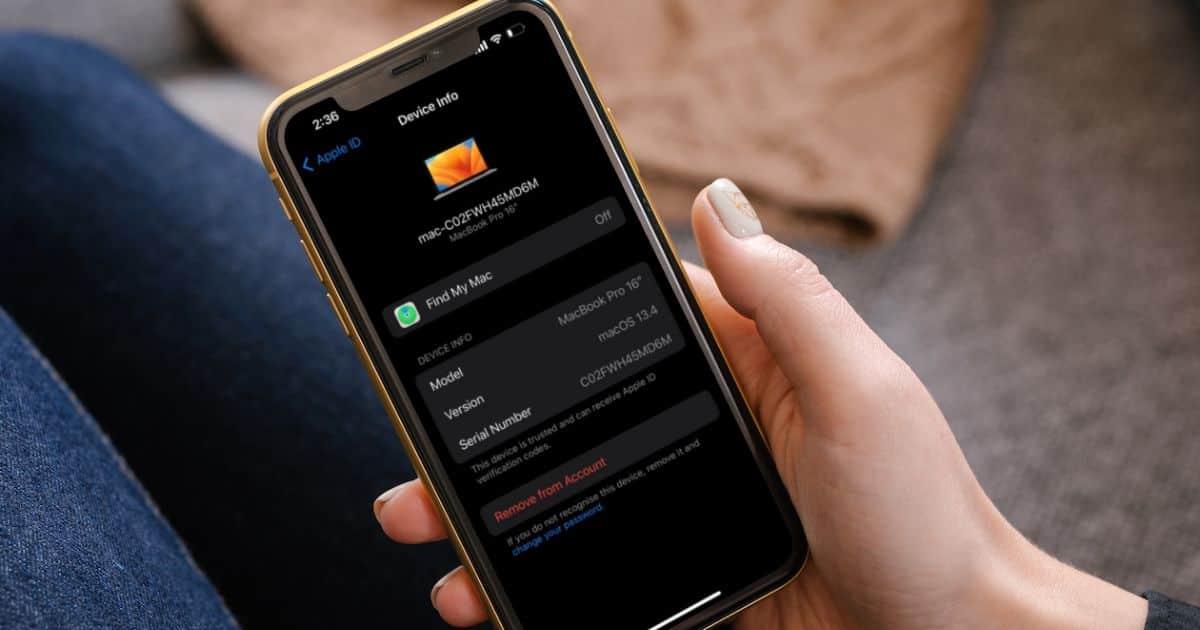
Best Ways To View and Remove Devices From Apple ID
Learn how to remove devices from your Apple ID using iPhone, iPad, Mac, browser, and iCloud. Also learn when to remove devices from Apple ID.
Best Mac Antivirus Software for Businesses
Learn about the best Mac antivirus solutions on the market. Learn about their best features, prices, and free trial period.
Why Parental Control Won't Work on Mac: Parental Control Setup Guide
Tom Victor explains how parents can safeguard their children by setting up Parental Control on Mac and implementing restrictions on app usage.
Best Mac Antivirus With VPN in 2024
Learn about the best antiviruses for Mac that have VPN services included. Find out their best features and pricing details.
Best AntiViruses for M2 MacBooks in 2024
What are the best antiviruses for Macs with an M2 processor? What are their best features and what are their pricing details?
Protecting Your Computer: A Guide to the Best Mac Antivirus
You should keep reading to explore the leading contenders for the best Mac antivirus software for your laptop or desktop.
How To Easily Fix Avast Not Working on Mac
Avast not working on Mac? Fix Avast issues on Mac by updating macOS, reinstalling the antivirus, or opting for an alternative antivirus.
How to Activate Lockdown Mode on Apple Watch
Apple has extended its Lockdown Mode to work on watchOS 10, too. Let’s look at what it does and how to activate it.
4 Expert Ways to Unlock iPhone Without a Passcode or Face ID
If you’ve forgotten the passcode for your iPhone and Face ID is failing you, you might wonder how to unlock it. Jeff Butts has the answers.
How to Check Microphone Usage on iPhone
Are you worried about apps accessing the microphone on your iPhone? Read along to learn how to check microphone usage on iPhone.
How To Use Find My iPhone for Someone Else
This article will teach you how to use Find My iPhone for someone else. It will also help you know how to add a new device to Find My app.
How To See If Someone Logged on to Your Instagram Account
If you want to see if someone has logged into your Instagram account, follow the steps here to check and secure your account.
Thieves, Soccer, and a Dopey Kid - TMO Daily Observations 2023-02-27
Thieves are stealing iPhones, punching in passcodes, and ruining people’s lives. Is it an iPhone problem or a person problem? TMO Managing Editor Jeff Butts joins Ken to sift through it. Plus, the first weekend of MLS on Apple TV and a kid AirDrops himself into jail.
Accidentally Training Your A.I. Replacement - TMO Daily Observations 2023-02-15
Apple used narration from human readers to train its A.I. voices. The real readers did not know that, and weren’t too happy when they found out. TMO writer Nick deCourville joins Ken to talk that over. Plus – an update on the Google Photos breakage, and some security advice for Apple Card holders.