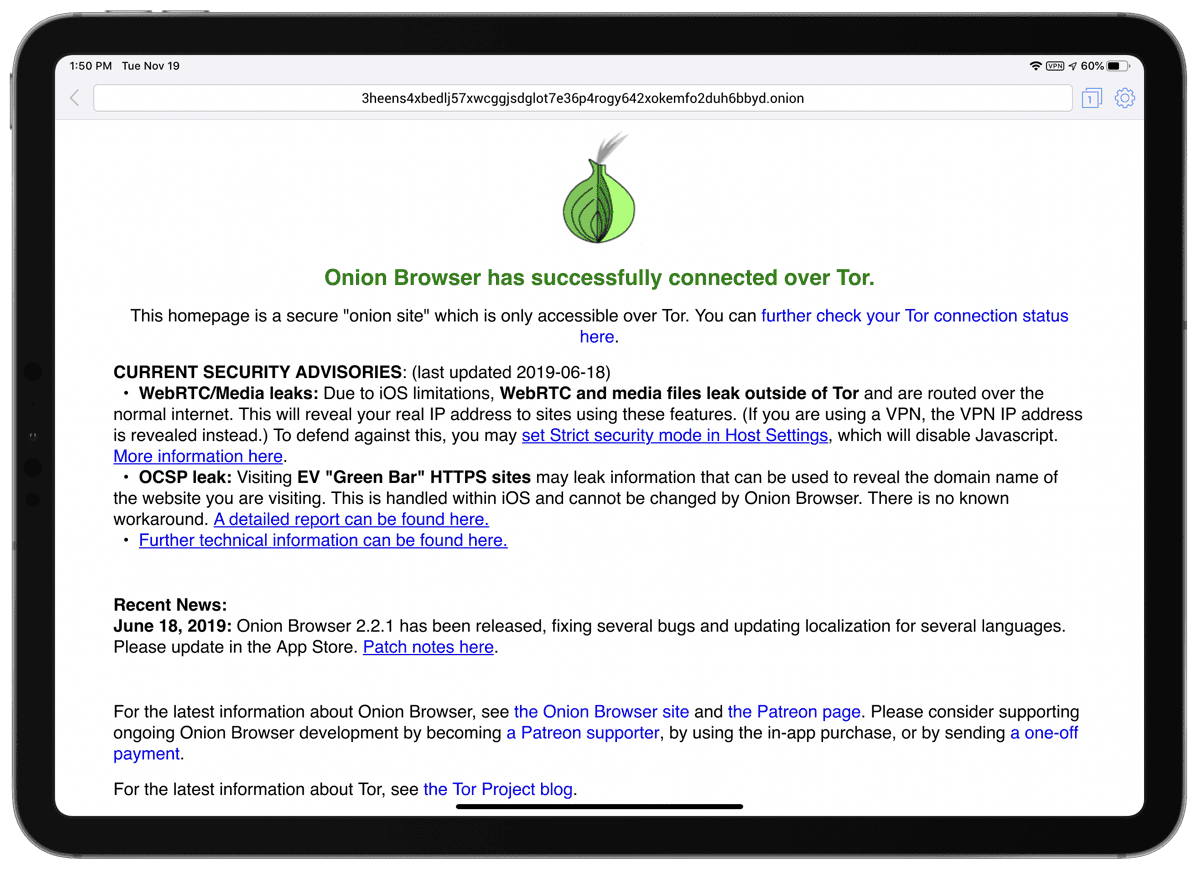
In computer security, a ‘chain of trust’ is when each component of hardware and software validates each other to make sure they haven’t been compromised. Kirk McElhearn explains the chain of trust on Apple devices.
It all begins with your Apple ID. When you create a new Apple ID on Apple’s website, or on a device you own, you provide your name, birthday, and email address, set up a password, then answer three security questions. You verify your email address, and your Apple ID now allows you to use Apple’s services.