British police recently arrested seven people, aged 16 to 21, as part of its investigation into the group of Okta hackers known as Lapsus$.
Security
Arizona First State to Accept ID in Apple Wallet at TSA Security
Apple Wallet users in Arizona will soon be able to use their devices to gain clearance at select TSA checkpoints. More states will follow.
New Malware Known as GIMMICK Affecting Mac Systems in Asia
Volexity’s security experts recently detected new malware, GIMMICK. It’s primarily affecting users in Asia, and there are ways to combat it.
New Malware Coming Through Email Posing as IRS
A new phishing scam posing at the IRS is making the rounds through email. Infamous botnet Emotet is behind many of the attacks.
Use Focus Mode to Make your iPhone a Gaming-Only Device
With Apple’s Focus Mode, iPhone users can create a custom, games-only profile, giving them peace of mind when a child plays with their phone.
Here's What We Know About PYSA Ransomware
PYSA ransomware is a piece of malware from an unknown APT group. It attacks what the FBI calls “soft targets.”
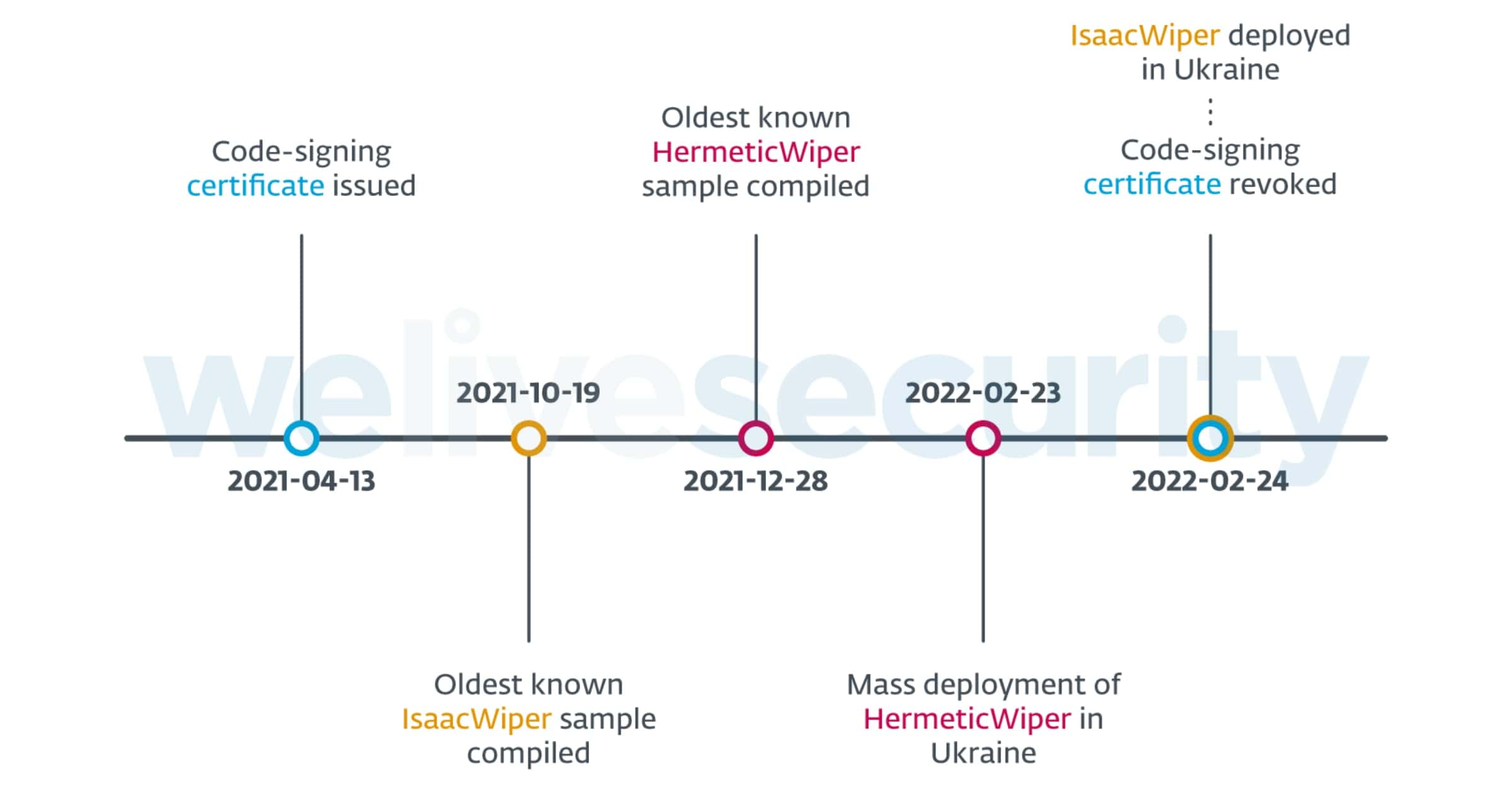
Security Firm Examines Recent Cyberattacks Against Ukraine
Entities in Ukraine have been targeted by hackers that wipe hard drives of all data. An investigation from PCMag reveals what has happened.
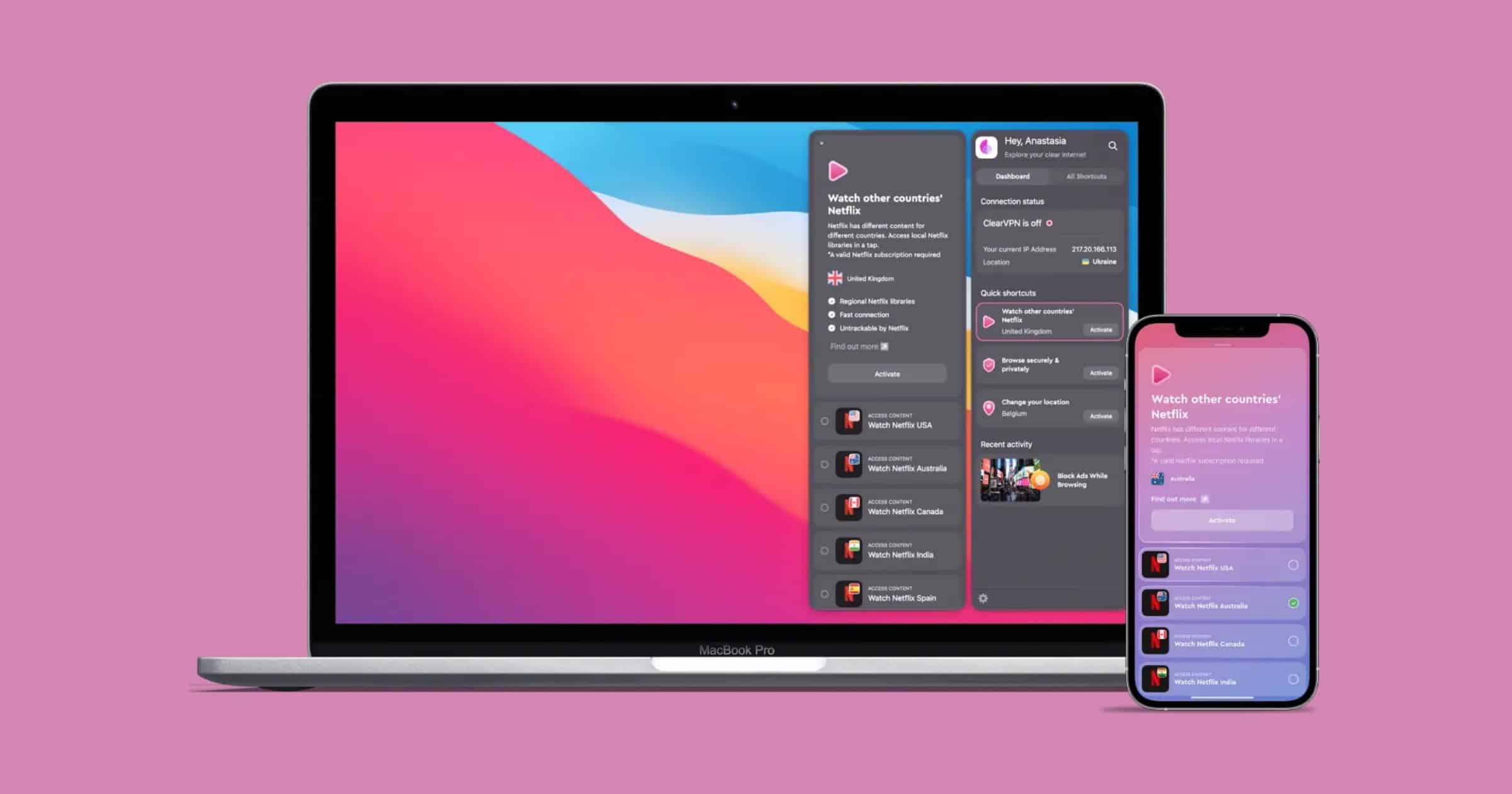
Here's How 'ClearVPN' From MacPaw Helps People Support Ukraine
ClearVPN from MacPaw, a company based in Kyiv, Ukraine, released a shortcut with information on trusted ways to support Ukraine.
Nvidia Confirms Data Breach From Ransomware Attack
Nvidia has confirmed that data was stolen in a data breach that occurred last week. The hackers claim to have stolen 1 terabyte in files.
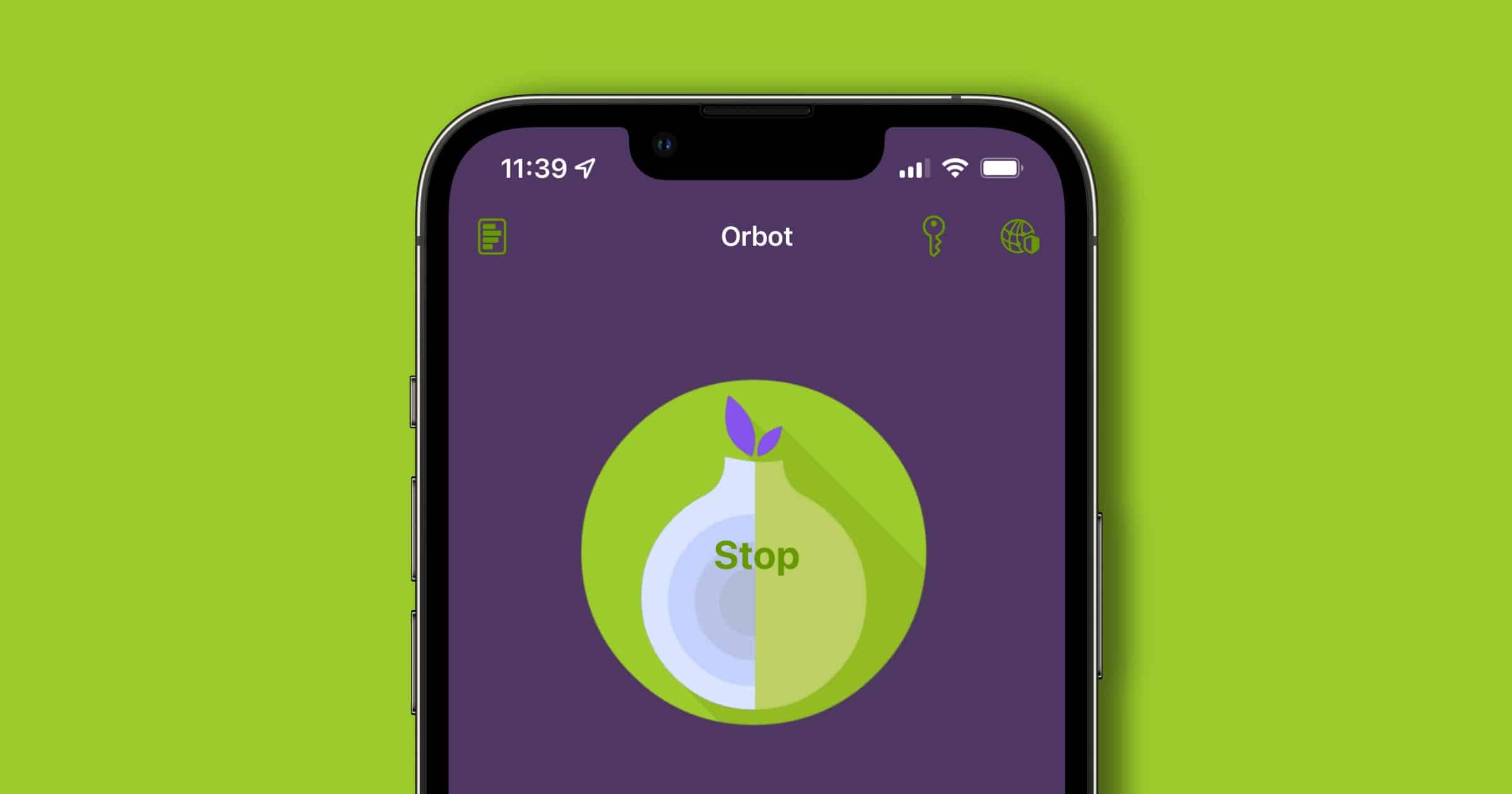
Need Tor on iOS? 'Orbot' has Arrived on the Platform
Do you need Tor on iOS? Orbot, the official app from The Tor Project, has arrived to iOS to secure your network traffic.
Security Friday: News and a Protection Checklist – TMO Daily Observations 2022-02-25
Jeff Butts and Andrew Orr join host Kelly Guimont to discuss this week’s security news, and some tips for better online safety.
Cybercrime Group 'Sandworm' Uses New Cyclops Blink Malware
A group or individual known as Sandworm or Voodoo Bear is using a piece of malware never before seen in the wild, called Cyclops Blink.
Security Friday: Actually Some Good News – TMO Daily Observations 2022-02-18
Andrew Orr and Kelly Guimont discuss the Security Friday news of the week including deepfake scams and nefarious AirTag schemes.
FBI Warns of Money Transfer Scams Over Video Calls
The FBI is warning consumers to be aware of scammers impersonating high-level company executives to trick employees into transferring money.
Passware's Cracking Tool Can Unlock Macs With T2 Chip
Passware’s forensic cracking tool can now be used on Macs that have Apple’s T2 security chip, a report says on Thursday.
GiveSendGo Data Breach Affects Donors of 'Freedom Convoy'
Attackers have breached the systems of GiveSendGo, a Christian fundraising platform. People who donated to the Freedom Convoy in Canada.
FBI: BlackByte Ransomware Attacks Critical Infrastructure
The FBI and Secret Service have seen signs of BlackByte ransomware attacking at least three critical infrastructure sectors in the U.S.
Security Friday: NDAs and Special Guests – TMO Daily Observations 2022-02-11
Andrew Orr and host Kelly Guimont discuss security news and sit down with John Kheit to talk about NDAs and using them for good or…less good.
Appointment Booker 'FlexBooker' Suffers Second Data Leak
The vpnMentor research team discovered a data leak from FlexBooker, a company that makes online appointment booking tools for businesses.
FBI Flash Report Warns of Attacks With LockBit 2.0 Ransomware
The FBI has issued a flash report this week that details indicators of compromise (IOC) linked to LockBit 2.0 ransomware.
iOS 15.3.1 Fixes an Issue With Braille Displays Not Working
Apple has released iOS 15.3.1 on Thursday that that fixes a problem with an accessibility feature. It also contains security fixes.
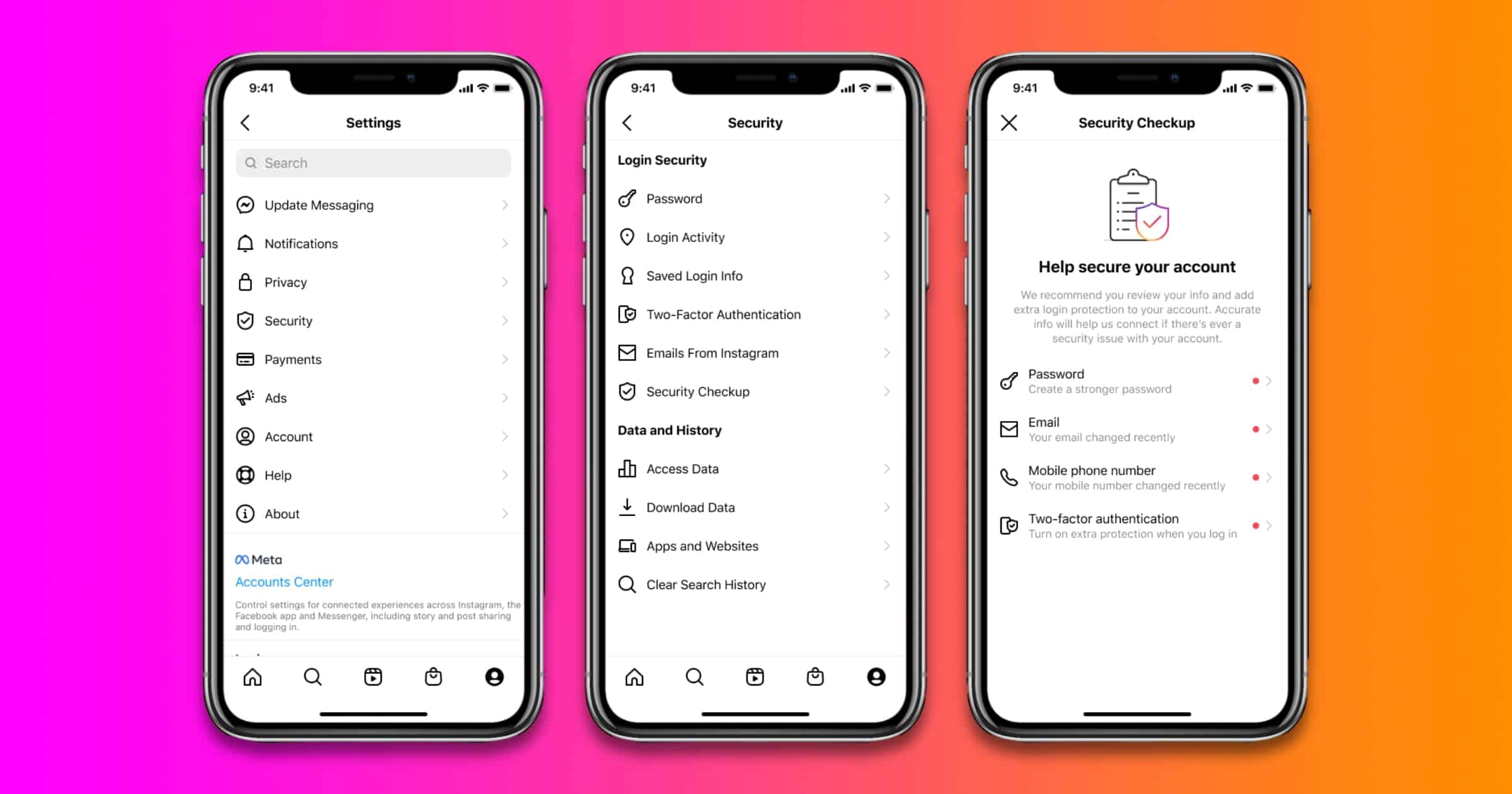
Instagram Security Checkup Expands to Users Worldwide
Instagram Security Checkup is a feature that people can use if their accounts may have been hacked. It’s rolling out to people globally.
ExpressVPN Bug Bounty Reward Increases to $100,000
The ExpressVPN bug bounty reward has increased to US$100,000, the company announced on Tuesday, ten times higher than the previous reward.
Security Friday: Everything Bad is New Again – TMO Daily Observations 2022-02-04
Andrew Orr and Kelly Guimont discuss Security Friday updates, including some suggested beverage pairings for each topic.