An app used by the U.S. Army at a major combat training base was recently removed because some of its code was written in Russia.
data leak
Appointment Booker 'FlexBooker' Suffers Second Data Leak
The vpnMentor research team discovered a data leak from FlexBooker, a company that makes online appointment booking tools for businesses.
Security Friday: Everything Bad is New Again – TMO Daily Observations 2022-02-04
Andrew Orr and Kelly Guimont discuss Security Friday updates, including some suggested beverage pairings for each topic.
Civicom Data Leak Affects Over 100,000 Files
Video conference company Civicom has had a data leak, found by the Website Planet Security team. Over 100,000 files were included.
Security Friday: This Week in (Sad) Data Breaches – TMO Daily Observations 2022-01-21
Andrew Orr joins host Kelly Guimont to discuss a Safari data leak, encrypted messaging, and as always, a new data breach.
Security Friday: This Week in Data Leaks – TMO Daily Observations 2021-12-17
Andrew Orr and Kelly Guimont discuss the security news and updates of the week, including two data leaks and end on a festive note.
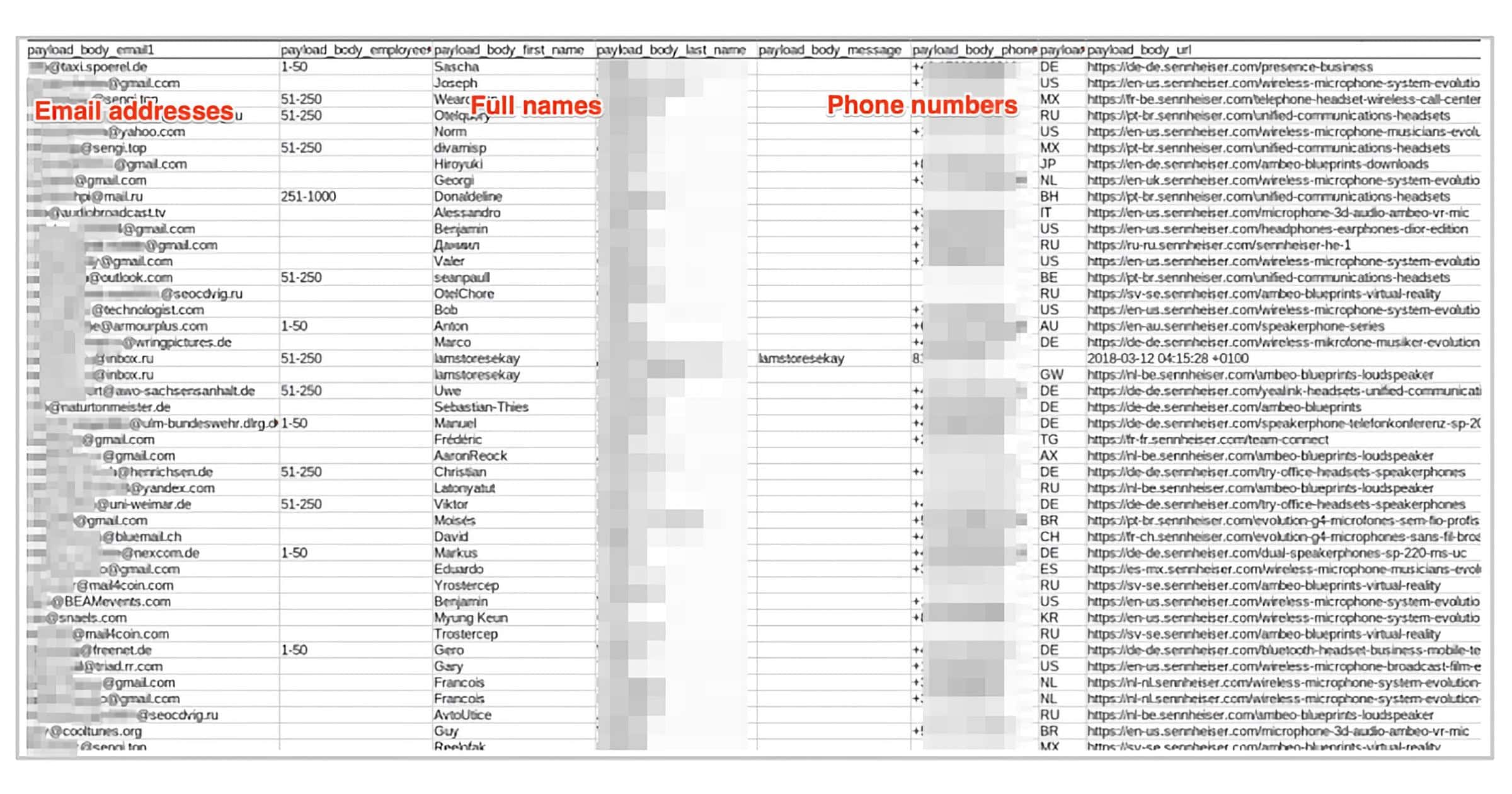
Sennheiser Leak Exposed 55GB of Data for Thousands of Customers
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a cache of data from audio company Sennheiser. It appears to be from an old cloud account that’s been dormant since 2018. Over 28,000 Sennheiser customers were exposed, with sensitive private data leaked.
While it’s unclear how all this data was collected, it appears to be from customers and businesses requesting samples of Sennheiser products.
Examples of entries: Full names, Email addresses, Phone numbers, Home addresses, Names of companies requesting samples, Number of the requesting company’s employees
US Logistics Company 'D.W. Morgan' Leaks Data Through Amazon S3
A report from Website Planet reveals D.W Morgan left an Amazon S3 bucket unprotected, resulting in the exposure of over 2.5 million files.
An Amazon S3 bucket owned by D.W. Morgan was left accessible without authorization controls in place, exposing sensitive data relating to shipments and the company’s clients.
As a market leader, D.W. Morgan provides services to some of the biggest companies in the world and there are major Fortune 500 organizations with data exposed on the open bucket.
Digital Marketing Agency 'Cronin' Leaks 92 Million Employee, Client Records
Security researcher Jeremiah Fowler in cooperation with the WebsitePlanet research team found an unprotected database from Cronin. It exposed 92 million database records from employees and clients.
The exposed server was named “Cronin-Main” and many of the records contained references to Cronin. These records included internal data such as employee and client information. Also included in the dataset was a “Master Mailing List” with direct physical names, addresses, Salesforce IDs, phone numbers, and references to where the leads came from.
(Update) Medical AI Company 'Deep6' Leaks 68 GB Trove of Patient Records
Security researcher Jeremiah Fowler together with the WebsitePlanet research team found an unprotected database belonging to Deep6. The records appear to contain data of those based in the United States.
Update: Deep6 reached out and said the news is misleading, saying “In August, a security researcher accessed a test environment that contained dummy data from MIT’s Medical Information Mart of Intensive Care (MIMIC) system, an industry standard source for de-identified health-related test data. To confirm, no real patient data or records were included in this ephemeral test environment, and it was completely isolated from our production systems.”
Meanwhile, according to WebsitePlanet, Mr. Fowler said, “I sent 3 follow up emails on Aug 11, Aug 12, Aug 23. No one has ever replied since the first message on Aug 10th. I validated that the doctor’s names were real individuals by searching obscure names (see screenshot). This is highly unusual in my experience to use real individuals’ data in a ‘dummy environment’ under any circumstances. Because no one replied, we added our disclaimer that we are highlighting that no patient data appeared in plain text, the records were “medical related”, and we never implied any wrongdoing or risk.”
Security Friday: Phishin and Strippin – TMO Daily Observations 2021-09-17
Andrew Orr and Kelly Guimont discuss Security Friday news and updates, including new phishing scams and sketchy wifi networks.
'GetHealth' Leaks Apple HealthKit Data With 61 Million Records
GetHealth, a health and wellness company in New York City, leaked data from a non-password protected database with over 61 million records.
Security Friday: News, Leaks vs Breaches, Metadata – TMO Daily Observations 2021-08-27
Andrew Orr joins host Kelly Guimont to discuss data leads vs data breaches, security news, and what metadata actually entails.
Data Leak From Chinese Company 'EskyFun' Affects 1 Million Gamers
The research team at vpnMentor discovered an unsecured server from Chinese mobile gaming company EskyFun. It exposed data for over a million Android gamers.
The resulting records contained a lot of sensitive information, including: IP address, IMEI number, Mobile application package doing the tracking, Device screen size – whether a device is ‘rooted’*, Device model, Phone number (if any), Platform (Android/iOS), NetType (WiFi or cellular), Events (open,login,level_up, etc).
Not so fun anymore.
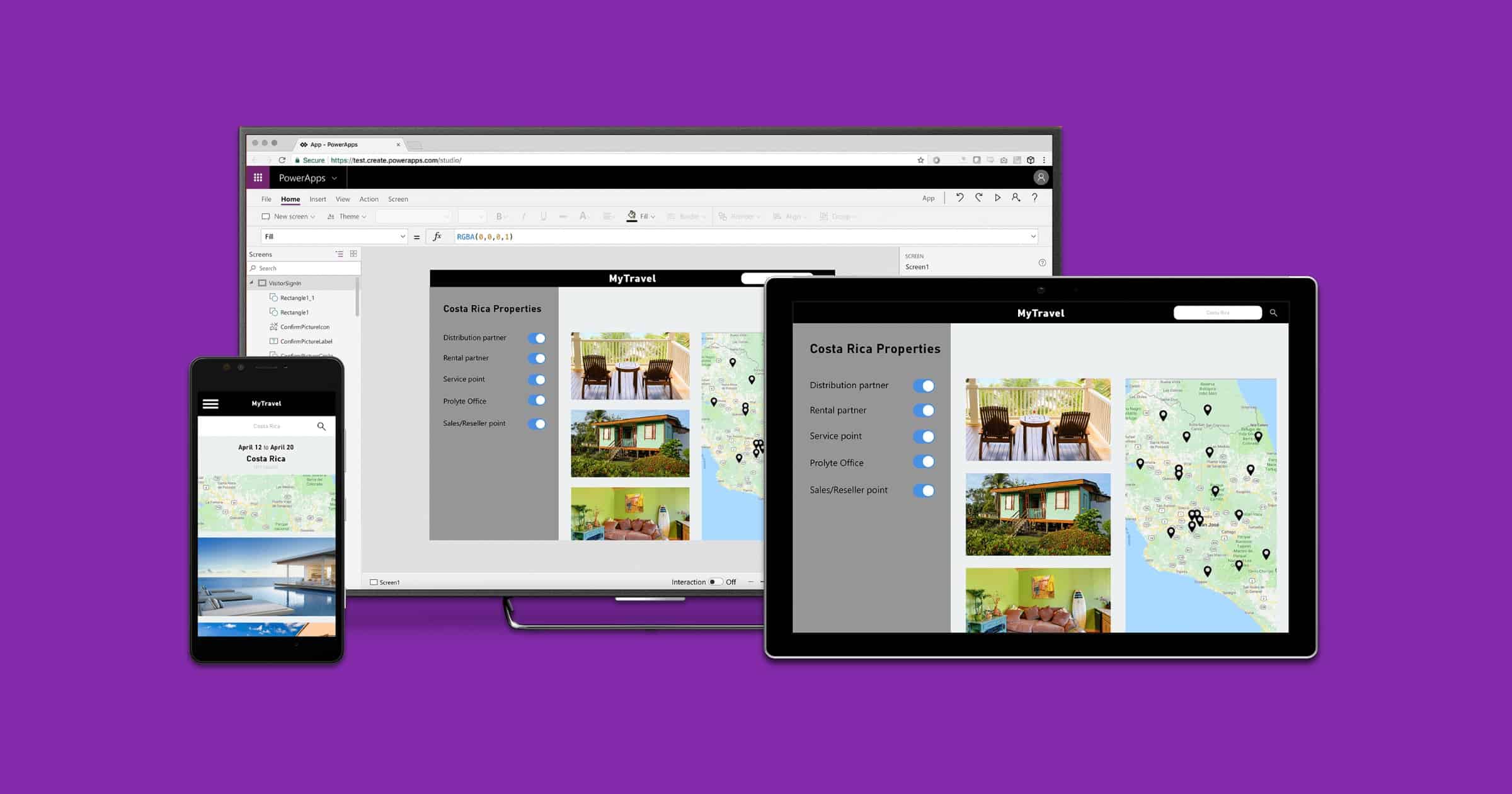
Misconfigured Microsoft Power Apps Leaked 38 Million Database Records
Over a thousand web apps from Microsoft’s Power Apps platform have leaked 38 million records. This data includes COVID-19 contact tracing.
The data included a range of sensitive information, from people’s phone numbers and home addresses to social security numbers and COVID-19 vaccination status.
The incident affected major companies and organizations, including American Airlines, Ford, the transportation and logistics company J.B. Hunt, the Maryland Department of Health, the New York City Municipal Transportation Authority, and New York City public schools.
Security Friday: Leaks, Phishing and Updates – TMO Daily Observations 2021-08-06
Andrew Orr joins host Kelly Guimont for Security Friday news and updates, including This Week in Data Leaks, and an update to a previous tip.
Raffle House Data Leak Exposes Personal Data of ‘Hundreds of Thousands’
Discovered on June 7, 2021, Raffle House suffered a data leak that leaked the personal data of hundreds of thousands of users.
Hackers Leak ‘Humana’ Data of Over 6,000 Patients
An SQL database containing what appears to be highly sensitive health insurance data of more than 6,000 patients has been leaked on a hacker forum.
The author of the post claims that the data was acquired from US insurance giant Humana and includes detailed medical records of the company’s health plan members dating back to 2019. The leaked information includes patients’ names, IDs, email addresses, password hashes, Medicare Advantage Plan listings, medical treatment data, and more.
Security Friday: News, Data Leaks, and Betas – TMO Daily Observations 2021-07-02
Andrew Orr joins host Kelly Guimont to discuss Security Friday news, discuss data privacy, and talk about some public betas available for testing.
Hackers Sell Personal LinkedIn Data From Leak Affecting 700M Users
Hackers are selling the personal information of over 700 million LinkedIn users. Here are the data types that were leaked:
Email Addresses; Full names; Phone numbers; Physical addresses; Geolocation records; LinkedIn username and profile URL; Personal and professional experience/background; Genders; Other social media accounts and usernames
On June 22nd, a user of a popular hacker forum advertised data from 700 Million LinkedIn users for sale. The user of the forum posted a sample of the data that includes 1 million LinkedIn users.
Web Hosting Service 'DreamHost' Leaked 814 Million Records of Customer Data
A database owned by Dreamhost was found unsecured and publicly accessible online. It contained 814 million entries of exposed usernames, display names, and emails for WordPress accounts.
The exposed log files contained what appears to be 3 years of records that range from 3/24/2018 to 4/16/2021 and each contained information about WordPress accounts hosted or installed on DreamHost’s server and their users. On May 4th a DreamHost representative acknowledged the discovery and informed us that the finding was being passed on to their legal team.
Update: DreamHost reached out to say that none of those records contain data that would have allowed access to DreamHost accounts. They consist entirely of entries that include object update records, error reports, and log entries. Data from just 21 individual websites were involved. More information can be found on its website.
Security Friday: Data Leaks and Drilling – TMO Daily Observations 2021-06-18
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and updates, including a way to obliterate that iPhone data once and for all.
Data Leak Exposes Customer Records With CVS Health
CVS Health recently leaked approximately one billion user records that include email addresses, user IDs, and metadata. The information was discovered in a non-password protected database.
CVS Health acted fast and professionally to secure the data and a member of their Information Security Team contacted me the following day and confirmed my findings and that the data was indeed theirs. I was informed that this was a contractor or vendor who managed this dataset on behalf of CVS Health, but it was confidential as to who the vendor was.
Security Friday and Facebook's Relationships – TMO Daily Observations 2021-05-07
Andrew Orr joins host Kelly Guimont for Security Friday’s news, including Facebook’s latest move involving your data.