In a new blog post, ProtonVPN announced it will fully encrypt its exit servers to help stop man-in-the-middle (MITM) attacks.
[ProtonMail Complied With 336 Government Requests in 2018]
MITM
A man-in-the-middle attack is when a third party secretly accesses the communication between two parties. The danger is that this attacker can control and possibly alter the communication.
When you connect to a VPN, you create an encrypted tunnel between your device and the VPN provider’s server. Your network traffic goes through this tunnel. People on your local network can no longer spy on this encrypted traffic. However, theoretically the VPN provider can see your traffic, although most don’t keep logs of what you do.
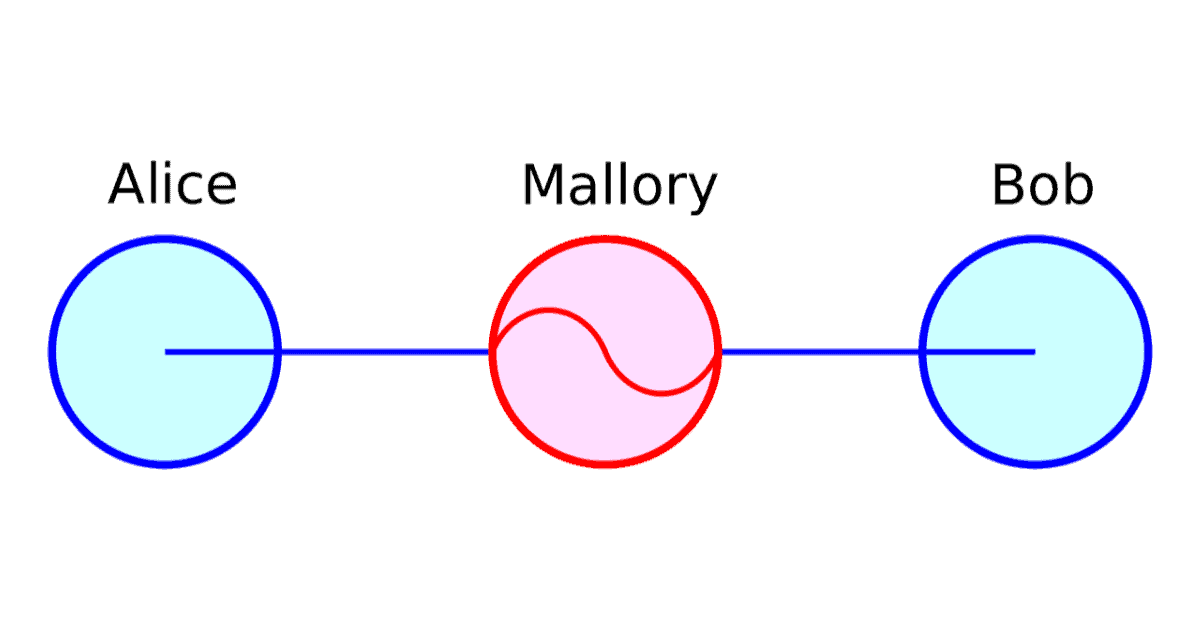
An example of an MITM attack against a VPN provider would be an attacker seizing control of the VPN server, stealing its certificate, and redirecting your traffic to a different server. This kind of attack is hard to do and in most cases only an attacker with the resources of a government could do it.
But if the VPN servers are encrypted, including the security certificates, an attacker can’t access the data even if they take over the server. As ProtonVPN notes,
During the transition to disk encryption, there will be some temporary outages as we reboot each exit server in turn. The majority of users won’t notice any down time. If you do, simply switch to a different VPN server. You can also enable kill switch (if supported on your device) so that even if your VPN connection drops, your device is blocked from sending unencrypted traffic over the network. Full disk encryption is already active on ProtonVPN’s Russia servers, and we will be rolling out this upgrade across our entire fleet of servers.

Is Proton as fast as ExpressVPN?