Last week, Zoom passed the 300 million daily users mark. Despite the well-documented company-level privacy problems, the video-conferencing platform has become essential to so many of us in this new home working era. As a user who may, for any number of legitimate reasons, have to use the service, there are various ways you can do so safely and effectively.

Use a Password for a Zoom Meeting
On April 5, Zoom password-protected meetings by default. While you can undo this via the settings in your Zoom account, you really shouldn’t. It is also important that you only send the password to the people you actually want to attend the call.
To password protect a meeting you want to schedule in advance, tap the Schedule icon in the Zoom app. In the Meeting ID section, you can choose to ‘Generate Automatically’ or use a Personal Meeting ID (PMI). If you tap the PMI option, you can choose a password. An automatically generated Meeting ID also has an auto-generated Password. Whichever way, you can then share that invite with the intended participants.
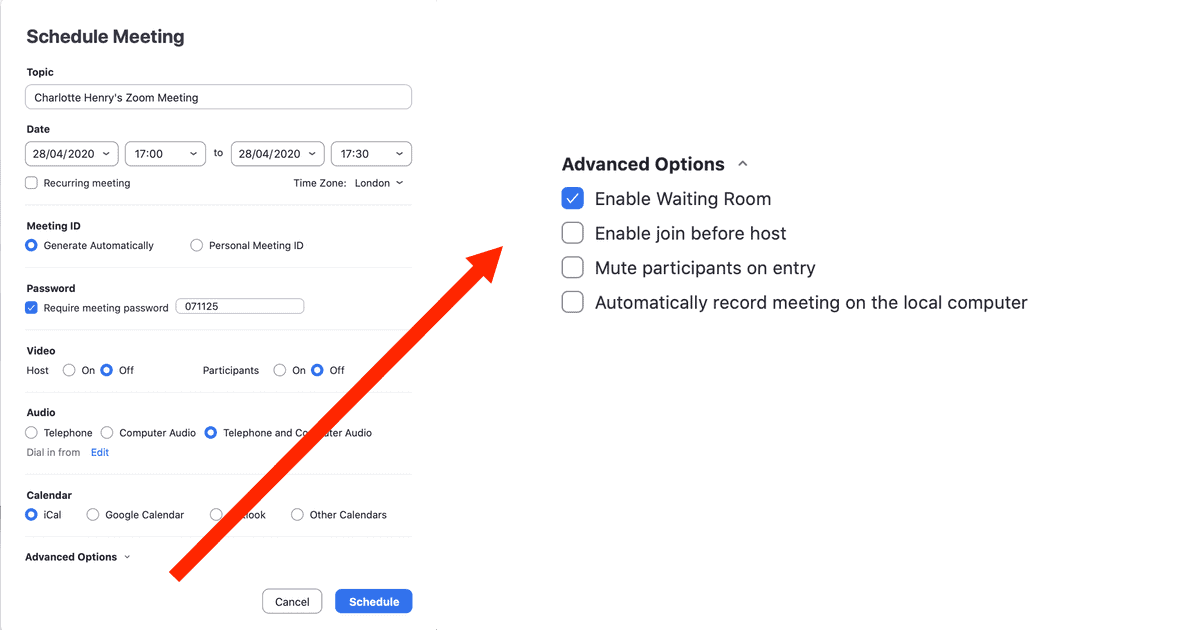
There are also advanced options most of which should be kept as default as show above. However, you might want to have participants muted on entry.
If you’re inviting people to instantly join a meeting that you’ve already started, if you tap Participants > Invite a meeting password will again be automatically created and included in your meeting invite. Alternatively if you want to do this using your personal meeting ID, tap to bring up the drop-down menu next to the New Meeting icon. Tick the box next to Use my Personal Meeting ID (PMI). Hover across your meeting ID to get an additional menu, then tap PMI Settings.
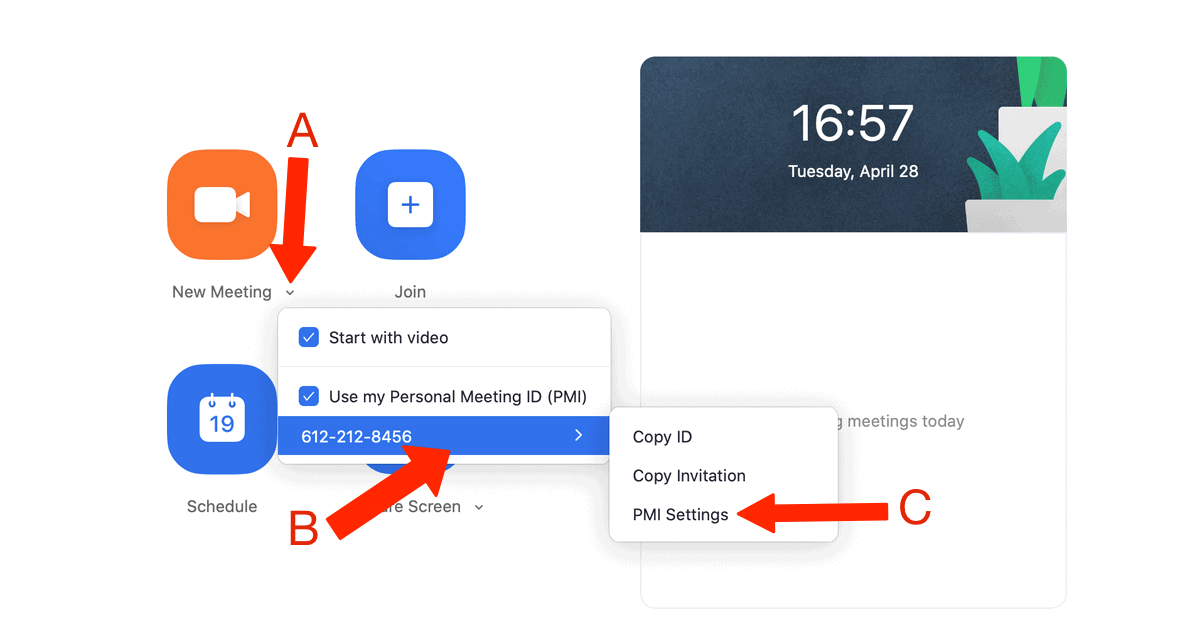
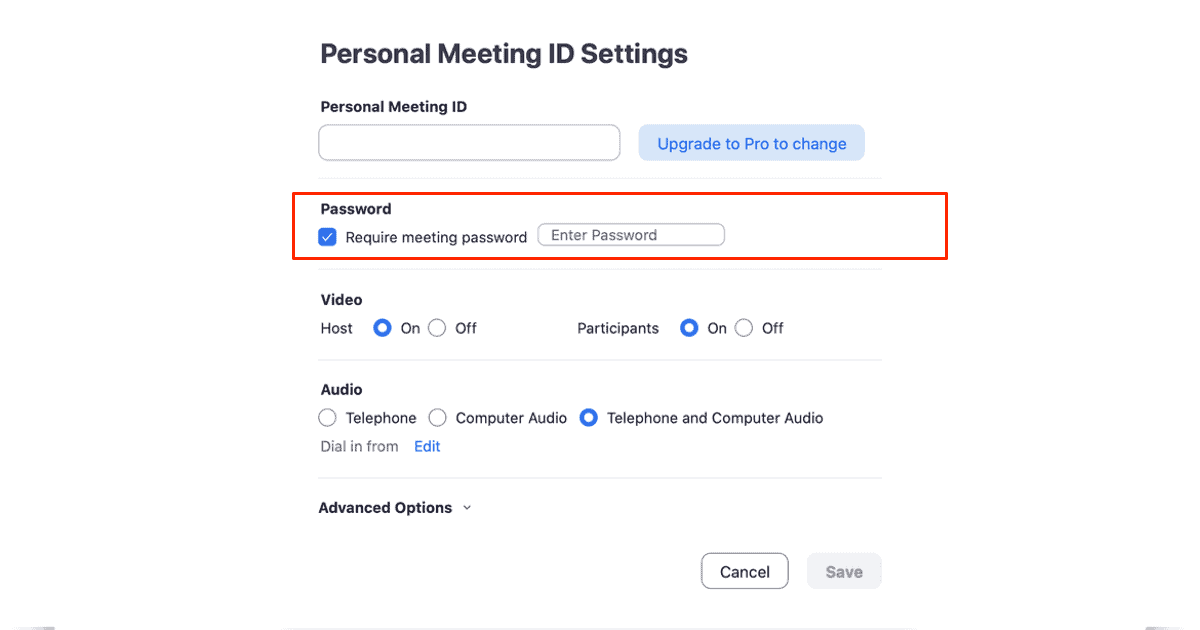
Then tap the ‘require meeting password’ box and enter the password and share it with those you want to attend the meeting.
More Security Settings
As shown in the image above, there are other security options in the Advanced Section. For instance, Enable Waiting Room is now set to on by default. This means that the host can vet who is entering the meeting, instead of them joining automatically. Furthermore, by default, nobody can join a meeting before the host has. Beyond that, you can adjust a host of security settings by going to your profile on the Zoom website and going to My Account > Settings. There are lots of different options you can toggle on and off.
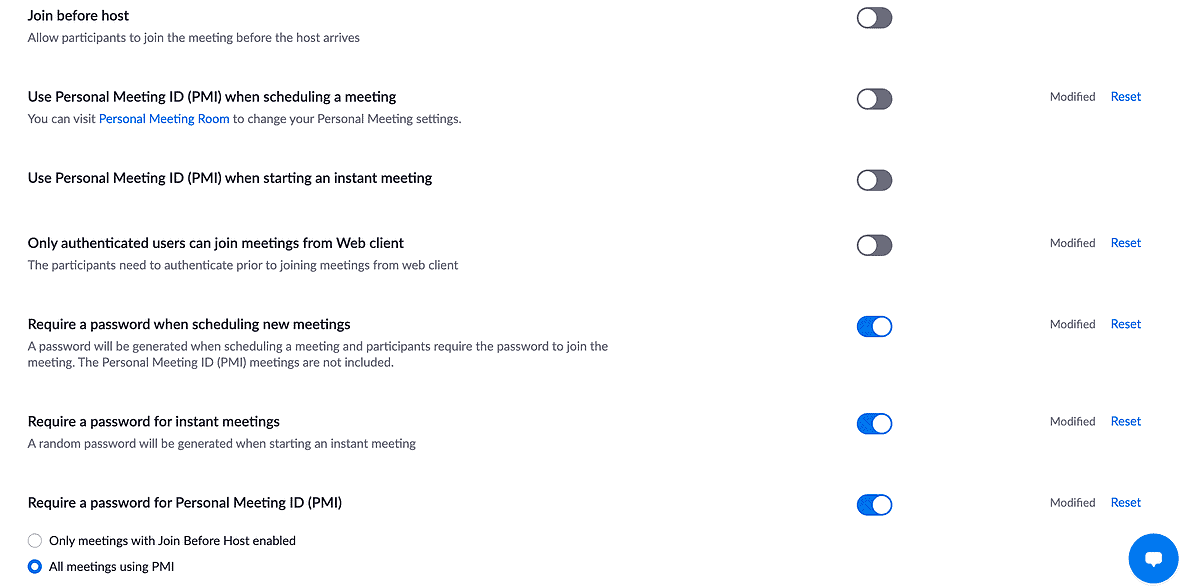
One of the available options is allowing a password to be embedded in a meeting link. Personally, I prefer to have this option set to off. It adds a small amount of friction – participants have to actively type in the password – but it means that someone who shouldn’t be on a call can’t join just by clicking a link that they’ve somehow got their hands on.

Lock Your Meetings
Once all the people you want have joined your meeting, you can lock the room to make sure nobody else can gatecrash.
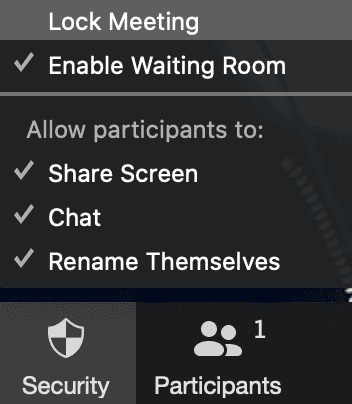
To do so, tap the security tab in the menu at the bottom of your meeting, then select the Lock Meeting.
How to be Good Zoom Meeting Participant
The above steps are those the host needs to take. There are though ways a participant can keep everyone else in the conversation safe. Mostly, don’t share a meeting password with anyone who shouldn’t have it – whether that be via a screenshot or an accidentally forwarded email. Oh, and mute your mic when you’re not speaking!

Charlotte:
This is very helpful. Most of my professional colleagues and I have implemented these security features, which while enhancing meeting-specific security, does nothing for other issues, such as end to end encryption, server routing, and the like.
As you’ve pointed out, Zoom has become a de facto standard for many. As with other platforms that service global communication, like Messenger or WhatsApp, one is limited by what is available to one’s colleagues abroad, who are, more often than not, using Android devices and Windows computers if they are in low and middle income countries.
For most of these meetings, like those with WHO, all of the countries that engage in state sponsored cyber-espionage, including industrial, are on the call, so one can argue, as many of my colleagues have, enhanced security is moot. Indeed, we hope that the major powers are listening.
As for calls regarding proprietary issues, like new therapeutics and vaccines under development by private industry, these should only be done on platforms with end to end encryption, which remains the industry standard.
“How to Host a Meeting Safely?” Don’t use Zoom