After this week’s (brief) ban on TikTok, users rushed to look for competing short video apps. One of the main alternatives is RedNote, but you may be worried about how to protect your data during usage. Here are some important steps to take to safeguard your personal information.
Is RedNote Dangerous To Use? Does It Harvest Data?
Firstly, let’s get things straight: RedNote isn’t less or more secure than TikTok ‚ or any social media, for that matter. It’s not that they aren’t going to dig through every possible bit of information to build your behavior profile. They will. However, they all will.
There’s a saying that all transactions have a buyer, a seller, and a product. For free-to-use social media, you’re neither the buyer nor the seller, so there’s only one thing left for you to be… the product.
In general, behavioral profiles are reportedly used to help advertisers show ads to people more likely to purchase their products. Users, in turn, get to see ads more likely to catch their interest, instead of generic offerings. In that aspect, it’s a matter of personal preference whether to allow social media platforms to harvest your data.
There are, however, other uses for this information, mainly developing strategies to make you use the apps for longer. That’s why, e.g., attorney generals from almost all US states opposed a kids-oriented Instagram variant.
There’s also the issue that parent companies are known to ignore mental health issues that arise from their apps. CNN reported one major case in 2023, related to Instagram (and Meta, which also owns Facebook and WhatsApp). However, scientific studies about that topic are plenty and cover all major platforms.
Now, it’s not our place to tell whether you should use one or another social media platform. That choice is yours. What we have to state plainly is that: RedNote collects your data, just like TikTok. But so do Instagram, Facebook, Twitter X, LinkedIn, and almost any social media site you can think of.
Safeguarding Personal Information While Using RedNote: 4 Methods
Now, if you want to try the “harm reduction” approach, you can limit what information each app gathers about you. This is part of a larger set of good cybersecurity practices, some of which I have listed below.
1. Don’t Neglect Device Updates
Firstly, always check for OS updates and app updates — and install them — on all your devices. It’s highly unlikely that RedNote (or any app installed through the App Store) will install malware on your iPhone. However, links you follow from within those apps can take you to suspicious websites.
Keeping your device up-to-date is one way of reducing (but not preventing) the possible damage these may inflict. Always remember to follow good cybersecurity practices to protect your data, in RedNote or elsewhere.
2. Limit Which Data the App Has Access To
Now, for RedNote itself. Any App Store listing has a section showing which information an app collects about you and/or your devices. You can click or tap this link to see the details for the RedNote app.
Think of a note-taking app, e.g., that requests permission to place and receive phone calls. There’s little chance this has a legitimate reason, right? For that reason, Apple itself prevents apps from requesting data or accessing information they don’t need to work properly.
You may want to use apps that have justified reasons to collect specific data, but would rather not provide it. WhatsApp, e.g., can use your location for some features, but can also work without that kind of access. Whenever an app requests permission for the first time, iOS asks if you want to allow it. In case you do, but change your mind later, you can change that in the app’s settings.
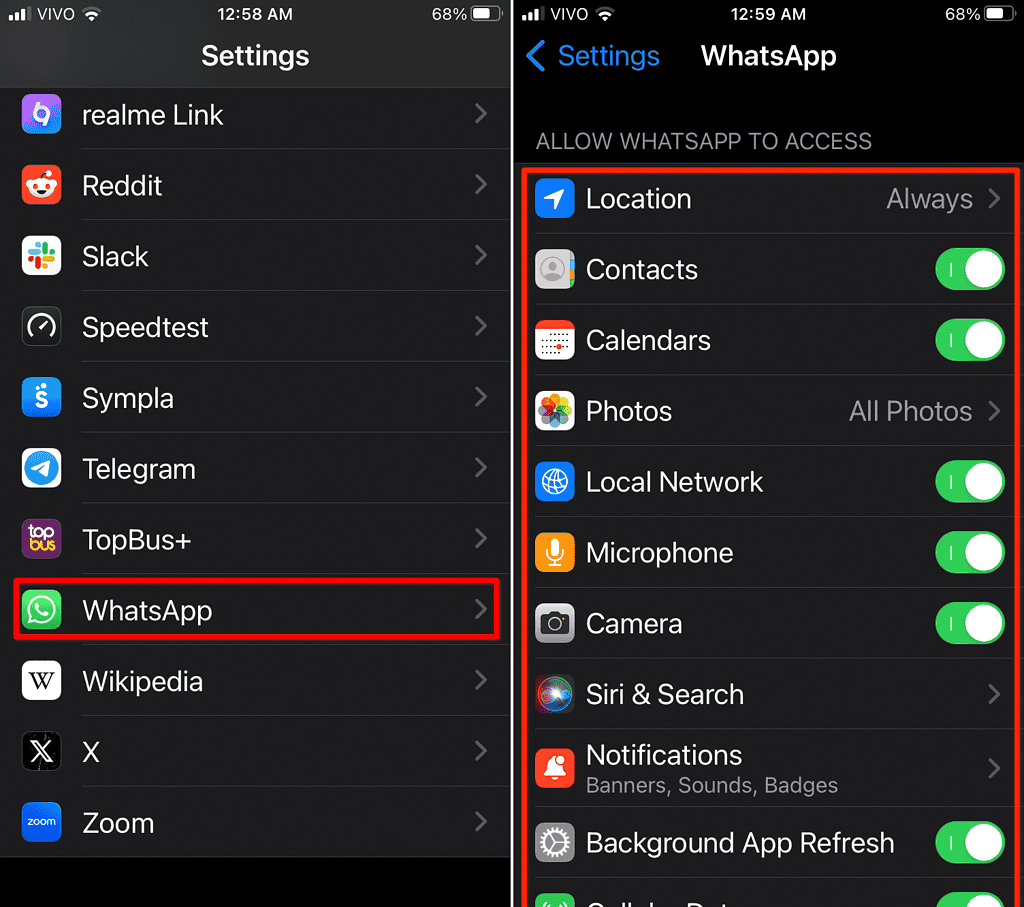
In the example above, I have chosen WhatsApp, but the same procedure applies to RedNote — or any app. All you have to do is select the app in Settings — the first screen you’ll see is the permissions list. From here, you can filter what to allow the app to use, and what to prevent it from accessing.
3. Use a VPN
Using a VPN is recommended if you want to prevent the app from gathering information about your network and location. When using a VPN, instead of accessing an app or website directly, you’ll connect to the VPN’s servers. These servers will receive your request and forward it to the app or website, hiding the connection’s origin.
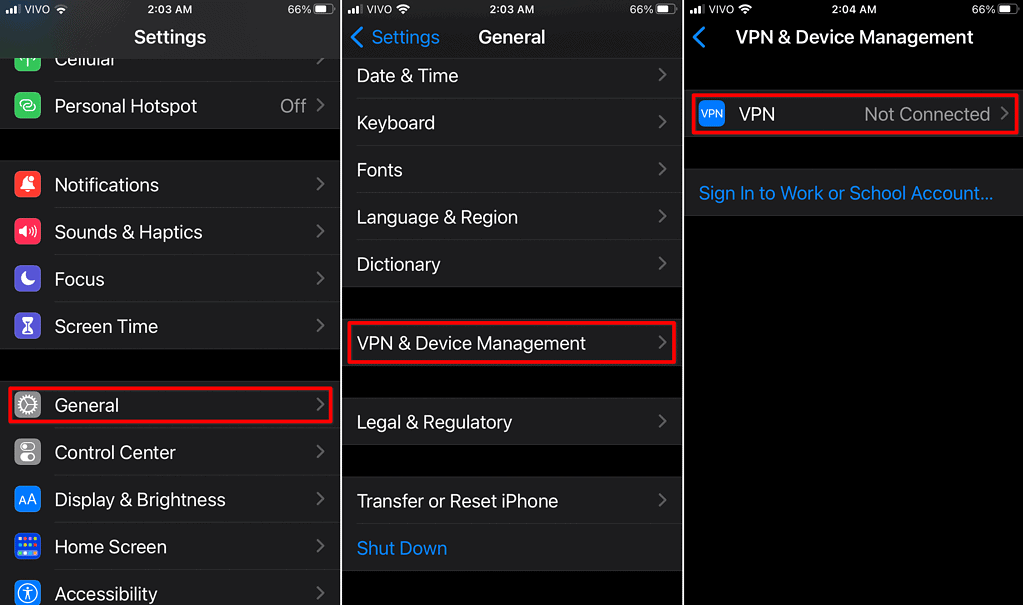
There are several reliable VPNs for iPhone. After selecting your preferred one, go to Settings > General > VPN & Device Management and set it up. Keep in mind, though, that there isn’t much sense in using a VPN if you reveal your whereabouts by other means. Whether it’s RedNote or another app, limit access to permissions to protect your location data. GPS, network information, and other features may give away your position.
4. Mind What Information You Share
Lastly, it’s always good to avoid sharing personal information on the internet. You can never know who’s watching, so refrain from sharing too much about the workplace, schools, home addresses, and so on. You can also check if your iPhone is being tracked, and make sure you’re clear of AirTag-abusing stalkers.

Whether RedNote (or even TikTok) is a national security risk is still the subject of conspiracy theories. It’s not for us to decide whether your short video craving poses a risk or not. If you’d rather play it safe without missing the next viral dance, though, our tips will help keep things secure.