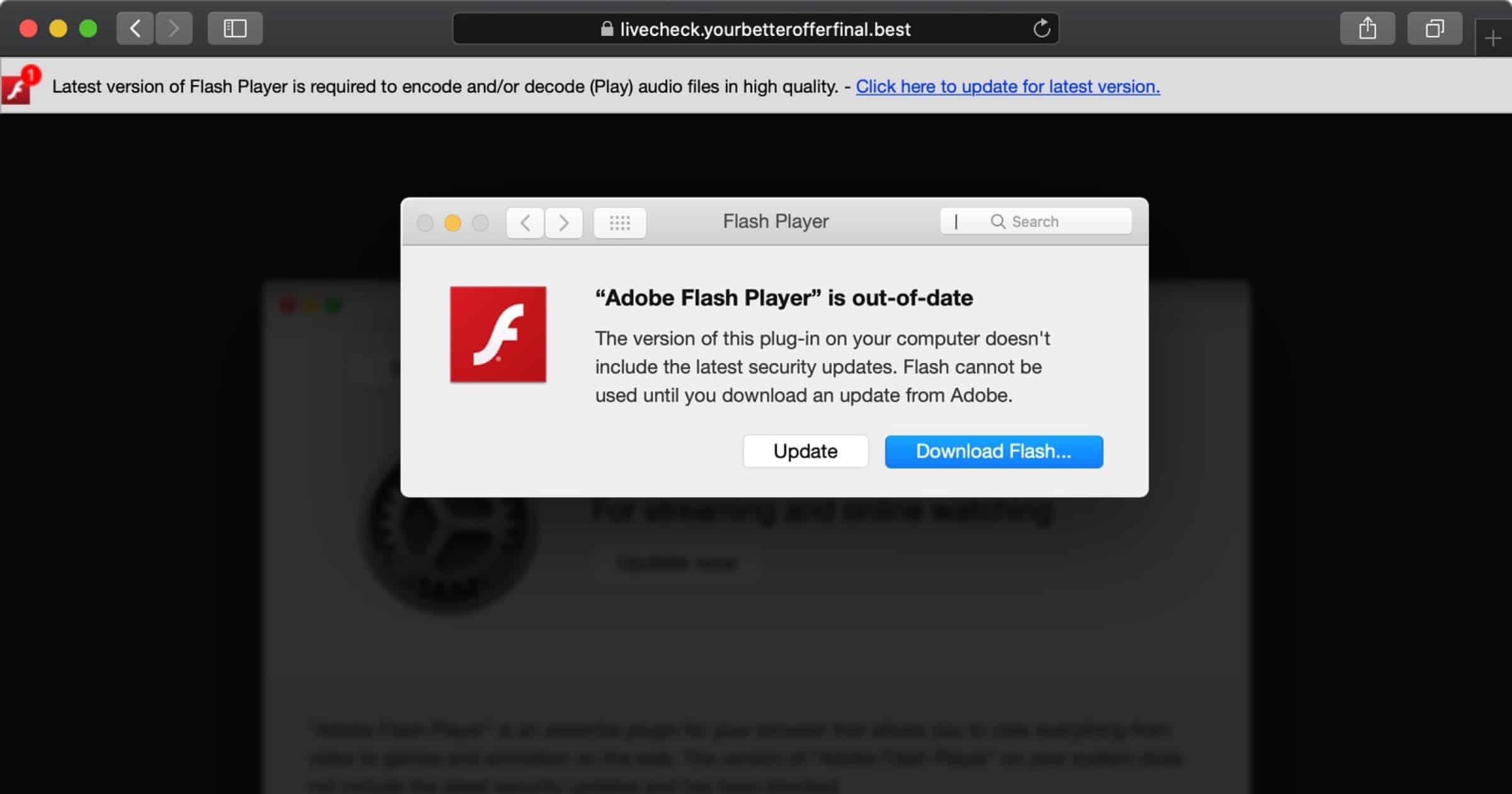
Security researchers say they have found a piece of malware disguised as an Adobe Flash installer and contained code notarized by Apple, which means it could run on Macs.
Notarized OSX.Shlayer
Introduced in macOS Catalina, Apple’s notarization process scans and approves software from developers before it can be distributed on the platforms. All developers who want to release Mac software have to submit an application to Apple. If Apple approves, the software is notarized. If a Mac user tries to open a non-notarized piece of software, macOS will block it and warn the user.
Researchers Peter Dantini and Patrick Wardle were able to confirm that Apple approved code used by the OSX.Shlayer malware, which was said to be the most common threat to Macs in 2019.
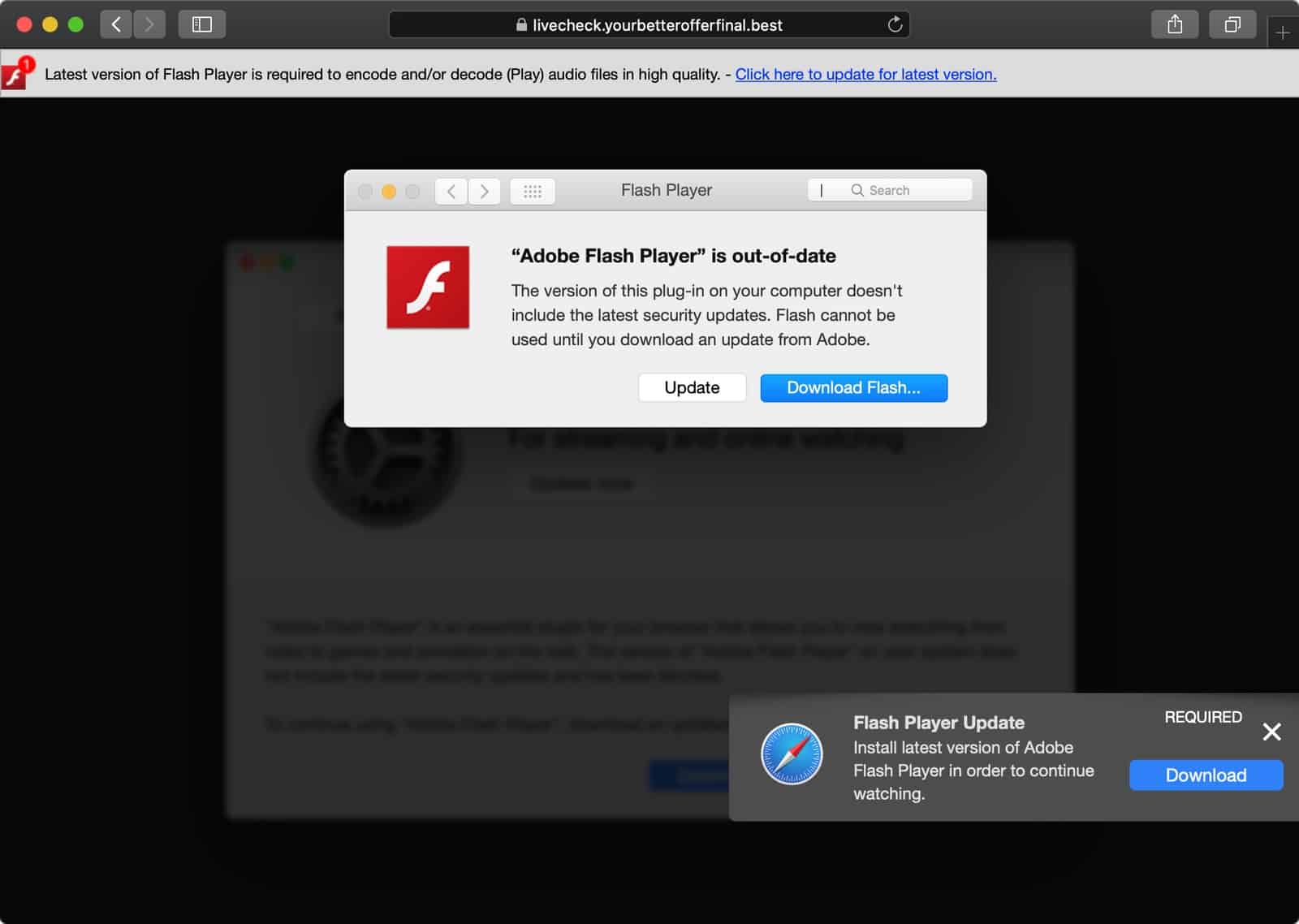
On Friday Mr. Dantini noticed that the website for Homebrew software was hosting an active adware campaign. If a user visited Homebrew.sh they would be redirected to a page saying that Adobe Flash Player is out of date, and a link to download an installer. Such malware is usually unnotarized so it can’t be run, but this installer did contain notarized code under a developer ID belonging to one Darien Watkins.
Once installed, OSX.Shlayer will persistently install other types of macOS adware. The researchers notified Apple which promptly revoked the notarization certificates on Friday, August 28. But as of Sunday the adware campaign is ongoing and are again notarized under a new developer ID (Aimee Shorter).