A hacker was able to hack a Verizon Employee database. Verizon has concluded that the information was not sensitive.
Hackers
The Search for Infamous Phone Phreaker Susy Thunder
The Verge has a cool story about searching for Susy Thunder, a phone phreaker and social engineer.
Susan found her way into the hacker underground through the phone network. In the late 1970s, Los Angeles was a hotbed of telephone culture: you could dial-a-joke, dial-a-horoscope, even dial-a-prayer. Susan spent most of her days hanging around on 24-hour conference lines, socializing with obsessives with code names like Dan Dual Phase and Regina Watts Towers. Some called themselves phone phreakers and studied the Bell network inside out; like Susan’s groupie friends, they knew how to find all the back doors.
MultiChain Hack Still Affecting Customers a Week Later
The Multichain hack is still affecting crypto users a week later, despite promises from the company that it had been contained.
China Hacking Group 'APT27' Attack German Companies
A China-based hacking group known as APT27 has been targeting German companies in areas such as technology and pharmaceuticals.
A Crypto Wallet Crack Recovered $2 Million in Tokens
The Verge had a fascinating story out yesterday about a crypto wallet crack that helped two friends get their tokens back. It’s a long-ish read but not overly technical.
Reich gave up and wrote off the money in his mind. He was willing to take the loss — until the price started to rise again. From a low of around $12,000, the value of their tokens started to skyrocket. By the end of 2020, it would be worth more than $400,000, rising briefly to over $3 million. It would be hard to get into the wallet without the PIN — but it wasn’t impossible. And with potentially millions on the line, Reich and his friend vowed to find a way inside.
Merck Wins Court Dispute Over 'NotPetya' Attack
Merck wins a court dispute with insurance companies for US$1.4 billion in losses due to the NotPetya attack. This was a cyberattack in 2017.
Red Cross Data Breach Affects 515,000 Vulnerable People
A contractor for The International Committee of the Red Cross (ICRC) suffered a data breach, as revealed on Wednesday.
Hackers Scam Blockchain City Group 'CityDAO' and Stole Funds
CityDAO, a group that bought 40 acres of land in Wyoming to build a blockchain-based city, has gotten hacked this week.
Saudi Activist With EFF Sues DarkMatter Group for Hacking iPhone
Saudi human rights activist Loujain AlHathloul, along with the Electronic Frontier Foundation, is suing DarkMatter for hacking her iPhone. DarkMatter Group was created and run by former U.S. intelligence operatives.
Reuters broke the news about the hacking program called Project Raven in 2019, reporting that when UAE transferred the surveillance work to Emirati firm DarkMatter, the U.S. operatives, who learned spycraft working for the National Security Agency and other U.S. intelligence agencies, went along and ran DarkMatter’s hacking program, which targeted human rights activists like AlHathloul, political dissenters, and even Americans residing in the U.S.
Hacking US Diplomats in Uganda May Have Led to NSO Group Downfall
ArsTechnica shares the story of how U.S. diplomats in Uganda were hacked by Pegasus, a spyware tool from NSO Group.
Israeli and US officials declined to confirm that the Ugandan hack directly triggered a decision to blacklist NSO. But one US official who discussed the issue with Israel’s defense ministry said: “Look at the entire sequence of events here—this is careful, not by chance.” He added that putting NSO, one of the jewels of Israel’s tech community, on a US blacklist was designed to “punish and isolate” the company.
DHS Announces 'Hack DHS' Bug Bounty Program to Improve Security
On Tuesday, the Department of Homeland Security (DHS) announced a bug bounty program called Hack DNS to improve security.
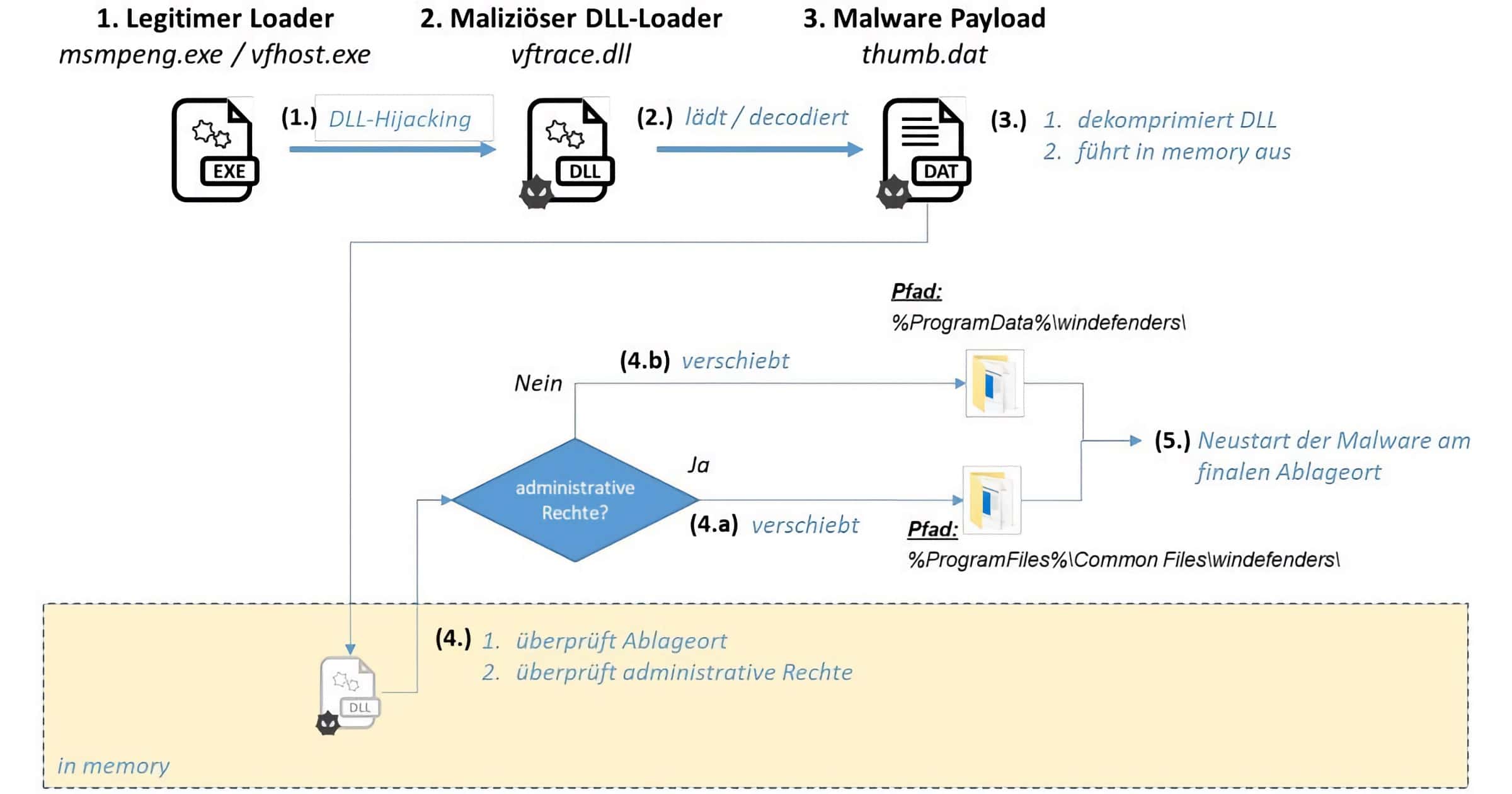
Microsoft Seizes Domains From Chinese Group 'NICKEL' Used to Attack Governments
NICKEL is a China-based threat actor that targets governments, diplomatic entities, and NGOs around the world. Microsoft’s Digital Crimes Unit has disrupted their operation.
MSTIC has observed NICKEL actors using exploits against unpatched systems to compromise remote access services and appliances. Upon successful intrusion, they have used credential dumpers or stealers to obtain legitimate credentials, which they used to gain access to victim accounts. NICKEL actors created and deployed custom malware that allowed them to maintain persistence on victim networks over extended periods of time.
Cuba Ransomware Gang Made $43.9 Million in Ransom Payments
The FBI also said it traced attacks with Cuba ransomware to systems infected with Hancitor. This is a malware operation to access Windows machines.
It is also worth mentioning that Cuba is also one of the ransomware groups that gather and steal sensitive files from compromised companies before encrypting their files. If companies don’t pay, the Cuba group will threaten to dump sensitive files on a website they have been operating on the dark web since January this year.
Planned Parenthood Hack Leaked Data for 400,000 Patients
In October, a Planned Parenthood facility in Los Angeles suffered a data breach. It affected about 400,000 patients.
Letters from PPLA to affected patients warned that “we identified files that contained your name and one or more of the following: address, insurance information, date of birth, and clinical information, such as diagnosis, procedure, and/or prescription information.”
Members of Hacking Group 'The Community' Sentenced for Stealing Cryptocurrency
A sixth member of international hacking group The Community has been sentenced in late November. The group stole millions in cryptocurrency.
Hackers Infiltrate Website Belonging to Sealand, Skimming Payment Data
Hackers have infiltrated a website belonging to the Principality of Sealand, using a web skimmer to steal user data such as payment information.
Intel Chip Flaw Lets Attackers Install Malicious Firmware to Bypass Security
A flaw found within certain Intel chips lets an attacker with physical access to the install malicious firmware onto the system.
US Issues Joint Advisory Warning Companies of Iranian Ransomware
In a joint advisory issued on Wednesday, the U.S. is warning that Iranian state-backed hackers are targeting infrastructure companies with ransomware.
The Iranian government-sponsored APT actors are actively targeting a broad range of victims across multiple U.S. critical infrastructure sectors, including the Transportation Sector and the Healthcare and Public Health Sector, as well as Australian organizations. FBI, CISA, ACSC, and NCSC assess the actors are focused on exploiting known vulnerabilities rather than targeting specific sectors.
FBI Says Data Was Not Compromised After Hackers Took Over Email Server
Hackers took over an FBI server over the weekend, sending thousands of fake cyberattack warnings. The agency says no personal information or data was affected.
The agency said it has fixed the software vulnerability that allowed the attack.
The fake emails originated from an FBI-operated server, which was dedicated to pushing notifications to the Law Enforcement Enterprise Portal (LEEP), which the FBI uses to communicate with state and local agencies. The compromised server was not part of the FBI’s corporate email service, the FBI added.
'REvil' Ransomware Group Taken Down Through Multi-Country Effort
The FBI, working with Cyber Command, the Secret Service, and other countries, took down REvil.
According to three people familiar with the matter, law enforcement and intelligence cyber specialists were able to hack REvil’s computer network infrastructure, obtaining control of at least some of their servers. After websites that the hacker group used to conduct business went offline in July, the main spokesman for the group, who calls himself “Unknown,” vanished from the internet.
US Bans Export of Hacking Tools to Authoritarian Regimes
The Commerce Department’s Bureau of Industry and Security (BIS) announced new rules for hacking tools and their export to other countries.
Ransomware Attack on Sinclair Broadcasting Linked to Russian Group 'Evil Corp'
Last weekend, Sinclair Broadcast Group found itself the victim of a ransomware attack, and sources claim Russian group Evil Corp. was behind it.
Anonymous Hacker Shares Twitch Source Code and Payout Data
An anonymous hacker shares data claimed to be Twitch source code. That’s right, not just Twitch data but Twitch itself, its source code and user payout data.
The user posted a 125GB torrent link to 4chan on Wednesday, stating that the leak was intended to “foster more disruption and competition in the online video streaming space” because “their community is a disgusting toxic cesspool”.
VGC can verify that the files mentioned on 4chan are publicly available to download as described by the anonymous hacker.
I have to chuckle about the part where they go on 4chan to complain about toxic websites. Update: Twitch has confirmed the incident.
Proposed Bill Would Require Disclosures of Ransomware Payments
Under the Ransom Disclosure Act, victims of ransomware who pay their attackers would have to report the payment within 48 hours.