Jeremiah Fowler together with the Website Planet research team found an unsecured Transcredit data leak of 822,789 records.
Security Friday
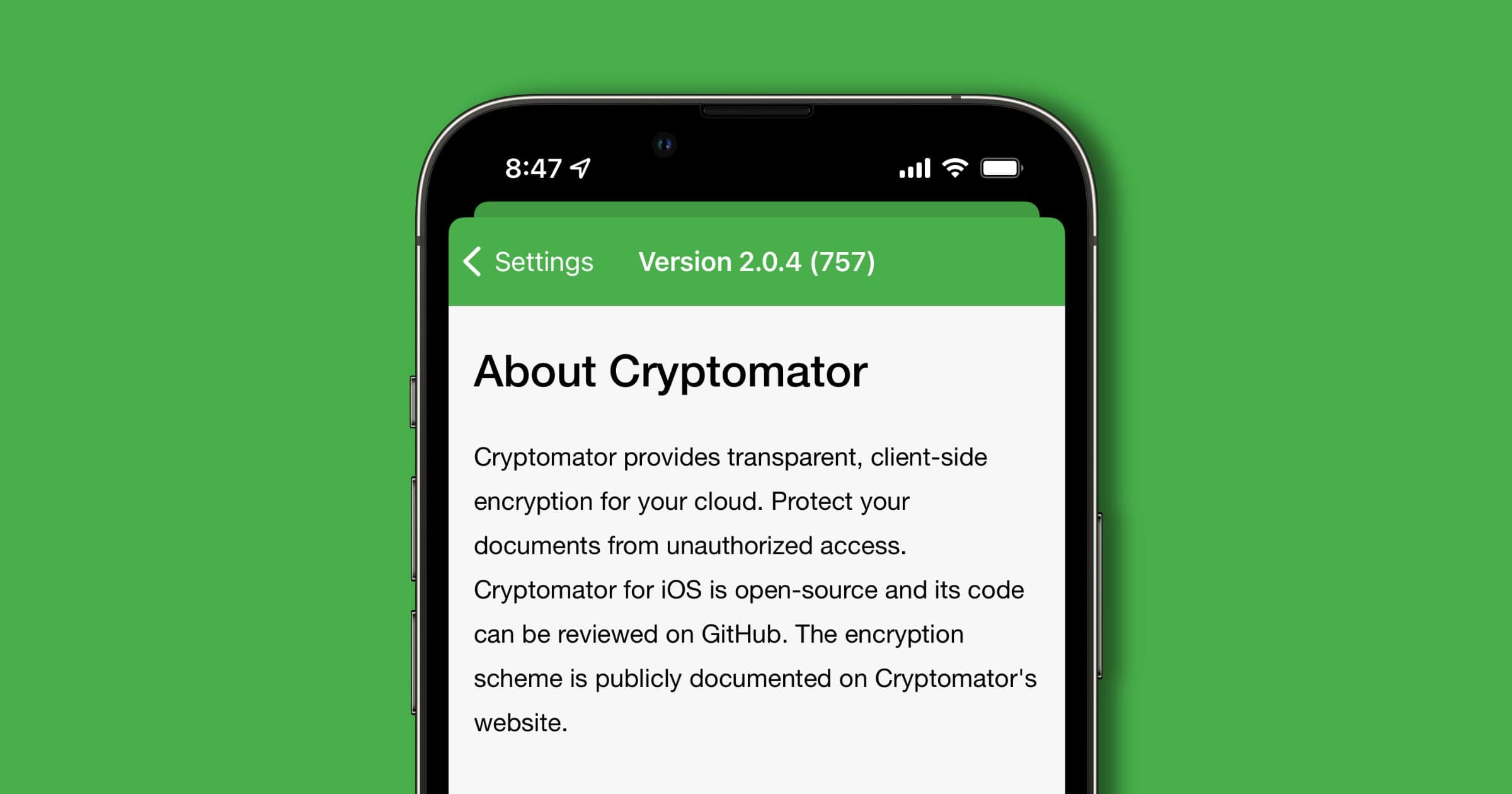
Update Immediately: Bug in 'Cryptomator' Leaks Encrypted File Paths to Apple
A bug in Cryptomator was recently found and reported on for the iOS app. The team wrote about the vulnerability on Tuesday.
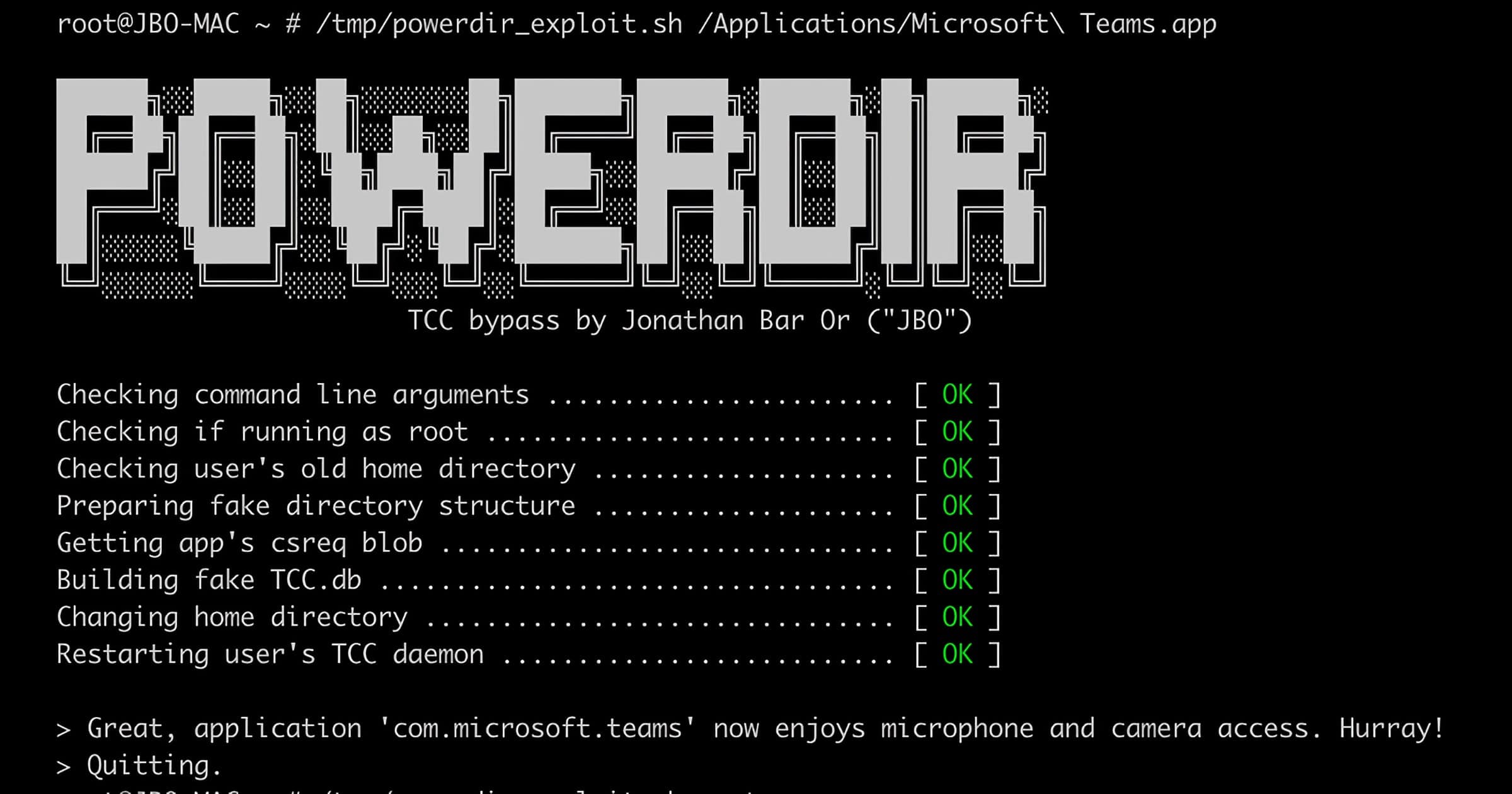
macOS Bug 'Powerdir' Could Let Attacker Access User Data
Microsoft’s security team has published an analysis of “powerdir” a vulnerability in macOS that could let an attacker access a person’s data.
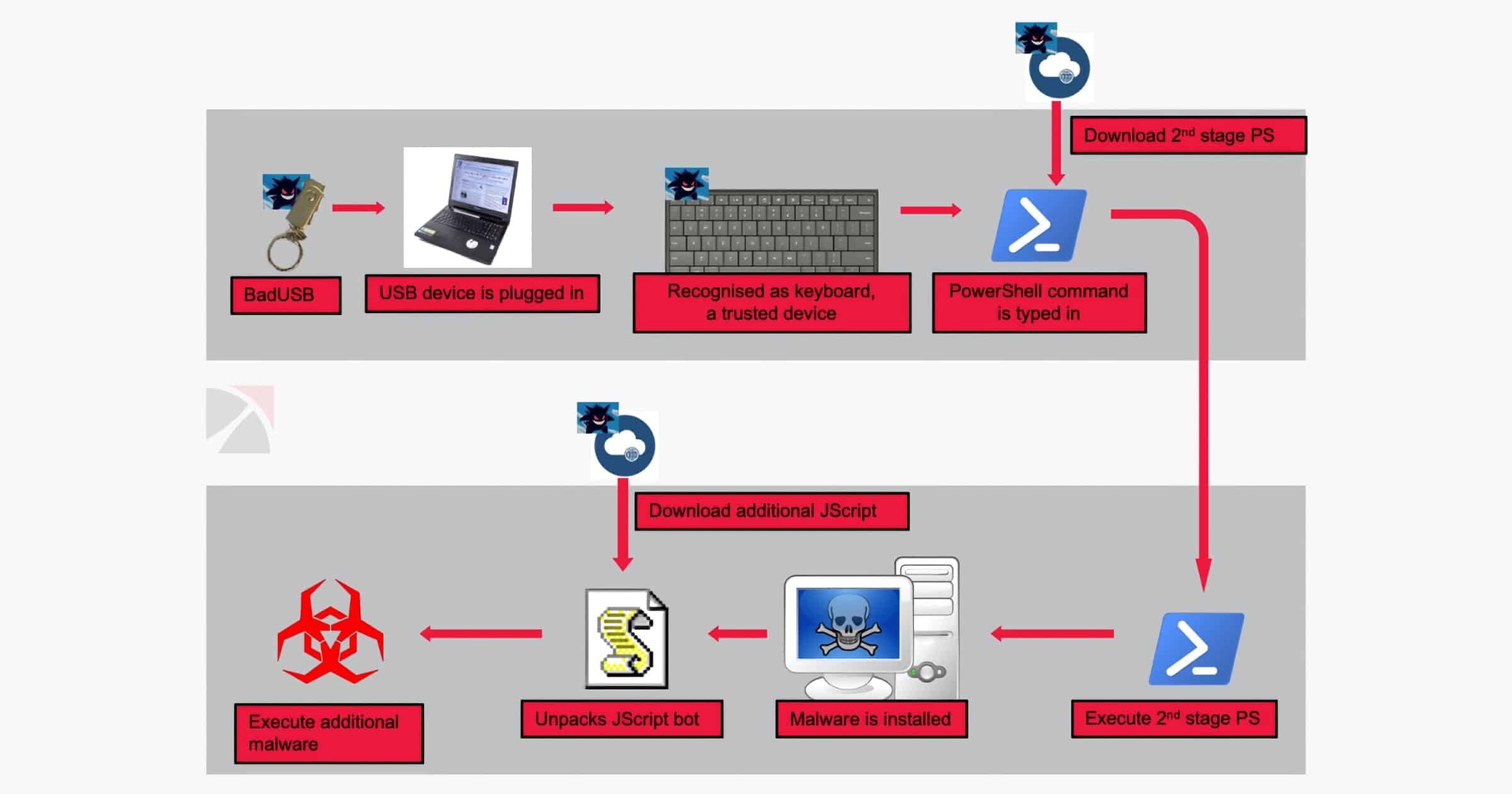
People are Mailing USB Drives With 'BadUSB' Malware to Companies
The FBI is warning that an Eastern European cybercriminal group is mailing USB drives filled with BadUSB malware to various companies.
Security Friday: Smart Home Practical Tips – TMO Daily Observations 2022-01-07
Andrew Orr and host Kelly Guimont chat about Security Friday news and updates, including tips on keeping your smart home gear safe and secure.
Ransomware Attack on Finalsite Shuts Down 5,000 School Websites
Finalsite is a company that helps schools with websites. In a statement, it says it was hit by a ransomware attack on Tuesday, January 4.
'NoReboot' is an iOS Bug That Can Fake a Shutdown to Trick You
ZecOps writes about “NoReboot,” the ultimate persistence bug that can trick the user into thinking the device has been shut down.
Wi-Fi Gateway From Airangel Affects Hundreds of Hotels
Security researcher Etizaz Mohsin says that the Airangel HSMX Gateway, used by many hotels to offer Wi-Fi to guests, contains hardcoded passwords that are easy to guess.
With those passwords, which we are not publishing, an attacker could remotely gain access to the gateway’s settings and databases, which store records about the guest’s using the Wi-Fi. With that access, an attacker could access and exfiltrate guest records, or reconfigure the gateway’s networking settings to unwittingly redirect guests to malicious webpages, he said.
Security Friday: This Week in Data Leaks – TMO Daily Observations 2021-12-17
Andrew Orr and Kelly Guimont discuss the security news and updates of the week, including two data leaks and end on a festive note.
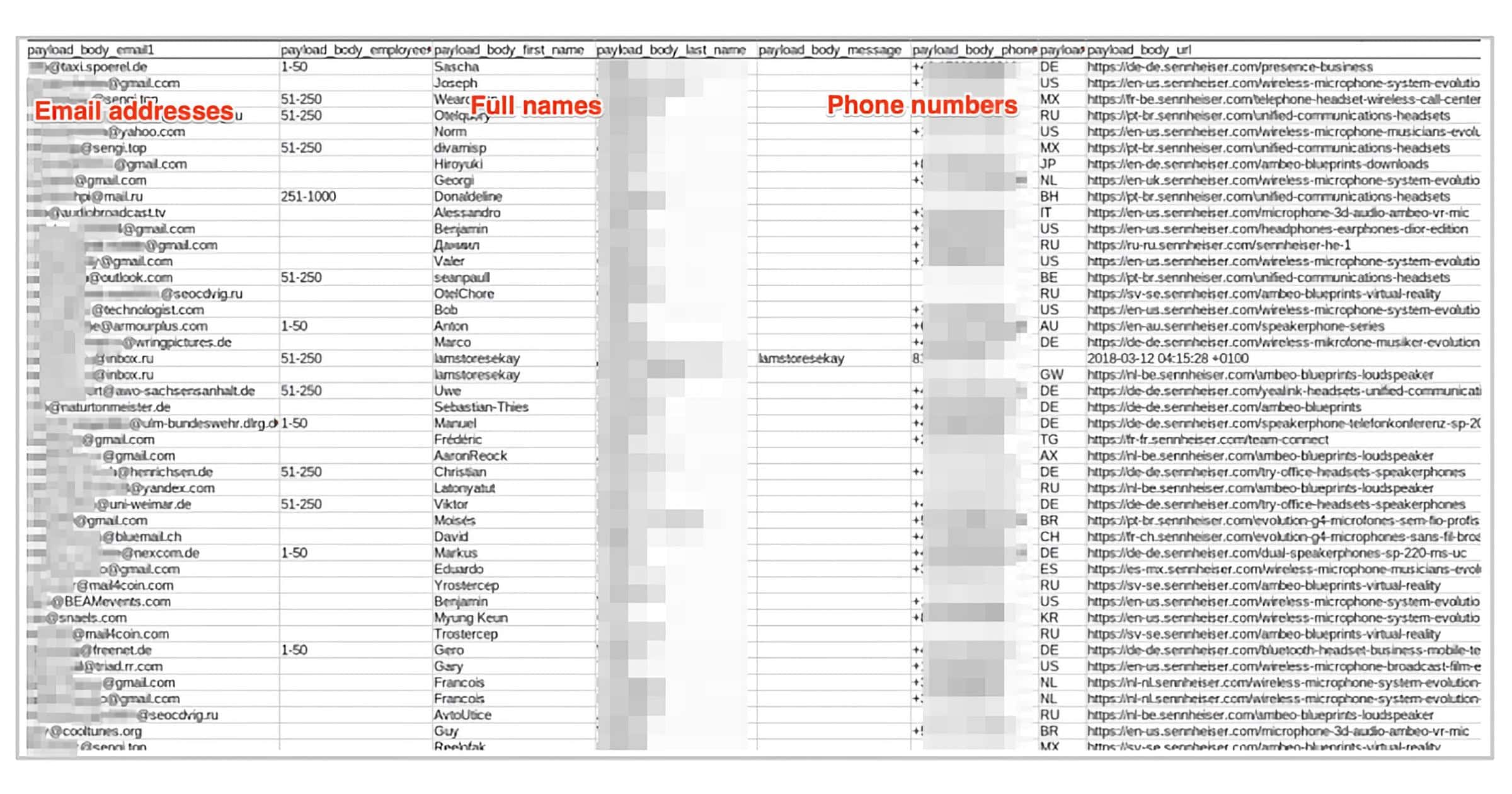
Sennheiser Leak Exposed 55GB of Data for Thousands of Customers
Led by Noam Rotem and Ran Locar, vpnMentor’s research team recently discovered a cache of data from audio company Sennheiser. It appears to be from an old cloud account that’s been dormant since 2018. Over 28,000 Sennheiser customers were exposed, with sensitive private data leaked.
While it’s unclear how all this data was collected, it appears to be from customers and businesses requesting samples of Sennheiser products.
Examples of entries: Full names, Email addresses, Phone numbers, Home addresses, Names of companies requesting samples, Number of the requesting company’s employees
US Logistics Company 'D.W. Morgan' Leaks Data Through Amazon S3
A report from Website Planet reveals D.W Morgan left an Amazon S3 bucket unprotected, resulting in the exposure of over 2.5 million files.
An Amazon S3 bucket owned by D.W. Morgan was left accessible without authorization controls in place, exposing sensitive data relating to shipments and the company’s clients.
As a market leader, D.W. Morgan provides services to some of the biggest companies in the world and there are major Fortune 500 organizations with data exposed on the open bucket.
DHS Announces 'Hack DHS' Bug Bounty Program to Improve Security
On Tuesday, the Department of Homeland Security (DHS) announced a bug bounty program called Hack DNS to improve security.
Security Friday: No News is Good News – TMO Daily Observations 2021-12-10
Andrew Orr and Kelly Guimont discuss Security Friday topics. They say no news is good news, and this week is FULL of news.
iCloud, Twitter, MineCraft, Cloudflare, All Vulnerable to a Powerful Bug
According to a report on Friday, major apps and services such as iCloud, Cloudflare, Steam, Twitter, and others are vulnerable to a bug.
On Thursday, researchers noticed that a popular Java logging library (log4j) had a bug that allows for Remote Code Execution or RCE, hacker lingo for one of the most dangerous types of vulnerabilities, one that essentially allows hackers to take control of the target. GitHub labeled the vulnerability as “critical severity,” and many researchers, as well as the Director of Cybersecurity at the NSA, are sounding the alarm.
If the NSA is publicly worried, you know it’s bad. Update: Cloudflare says they are not vulnerable, “We responded quickly to evaluate all potential areas of risk and updated our software to prevent attacks, and have not been able to replicate any external claims that we might be at risk.” The company published a blog post on the matter.
Co-Founder of Swiss SMS Giant 'Mitto AG' Accused of Government Surveillance
Swiss tech company Mitto AG is trusted by companies such as Twitter and Google to deliver SMS security codes to users, appointment reminders, sales promotions, and more. It’s co-founder and COO Ilja Gorelik has been accused of selling access to Mitto’s networks for surveillance.
The existence of the alternate service was only known to a small number of people within the company, these former employees said. Gorelik sold the service to surveillance companies which in turn contracted with government agencies, according to the employees.
Microsoft Seizes Domains From Chinese Group 'NICKEL' Used to Attack Governments
NICKEL is a China-based threat actor that targets governments, diplomatic entities, and NGOs around the world. Microsoft’s Digital Crimes Unit has disrupted their operation.
MSTIC has observed NICKEL actors using exploits against unpatched systems to compromise remote access services and appliances. Upon successful intrusion, they have used credential dumpers or stealers to obtain legitimate credentials, which they used to gain access to victim accounts. NICKEL actors created and deployed custom malware that allowed them to maintain persistence on victim networks over extended periods of time.
Verizon Automatically Tracks Your Data in New Update
In a new program called Verizon Custom Experience, the company is automatically opting customers in to track their data. But you can opt out.
A new program innocuously titled the “Verizon Custom Experience” is sold to users as a way for the company to “personalize our communications with you, give you more relevant product and service recommendations, and develop plans, services and offers that are more appealing to you.” To accomplish this, all a Verizon subscriber needs to do is… allow the company access to all the websites you visit, apps you use, as well as see everyone you happen to call and text.
Hundreds of Tor Servers From 'KAX17' Threaten to Deanonymize Users
Security researcher ‘Nusenu’ has uncovered hundreds of Tor servers belonging to an entity tracked as KAX17.
Grouping these servers under the KAX17 umbrella, Nusenu says this threat actor has constantly added servers with no contact details to the Tor network in industrial quantities, operating servers in the realm of hundreds at any given point.
KAX17’s focus on Tor entry and middle relays led Nusenu to believe that the group, which he described as “non-amateur level and persistent,” is trying to collect information on users connecting to the Tor network and attempting to map their routes inside it.
Security Friday: Smarthome Security, Breaches, and Grand Theft AirTag – TMO Daily Observations 2021-12-03
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and introduce a rating system for how worried to be about certain stories.
Hackers Steal $119 Million From Web3 Project 'BadgerDAO'
BadgerDAO reported on Wednesday that it lost about 2,100 bitcoin and 151 ether in a hacking attack.
Kryptobi, who said he is on the BadgerDAO support team and has been looking into the hack, told Motherboard that it appears someone injected a malicious script into BadgerDAO’s frontend after compromising an API key for BadgerDAO’s Cloudflare account. Cloudflare is a web infrastructure, content delivery network, and website security company, which is used by millions of sites on the internet.
Planned Parenthood Hack Leaked Data for 400,000 Patients
In October, a Planned Parenthood facility in Los Angeles suffered a data breach. It affected about 400,000 patients.
Letters from PPLA to affected patients warned that “we identified files that contained your name and one or more of the following: address, insurance information, date of birth, and clinical information, such as diagnosis, procedure, and/or prescription information.”
'EWDoor' Malware Attacks Thousands of AT&T Internet Subscribers
Hackers are exploiting a bug from 2017 to attack the EdgeMarc Enterprise Session Border Controller. This device is used by businesses to manage phone calls and video calls.
The vulnerability being exploited to infect the devices is tracked as CVE-2017-6079, a command-injection flaw that penetration tester Spencer Davis reported in 2017 after using it to successfully hack a customer’s network. The vulnerability stemmed from an account in the device that, as Davis learned from this document, had the username and password of “root” and “default.”
Hackers Infiltrate Website Belonging to Sealand, Skimming Payment Data
Hackers have infiltrated a website belonging to the Principality of Sealand, using a web skimmer to steal user data such as payment information.