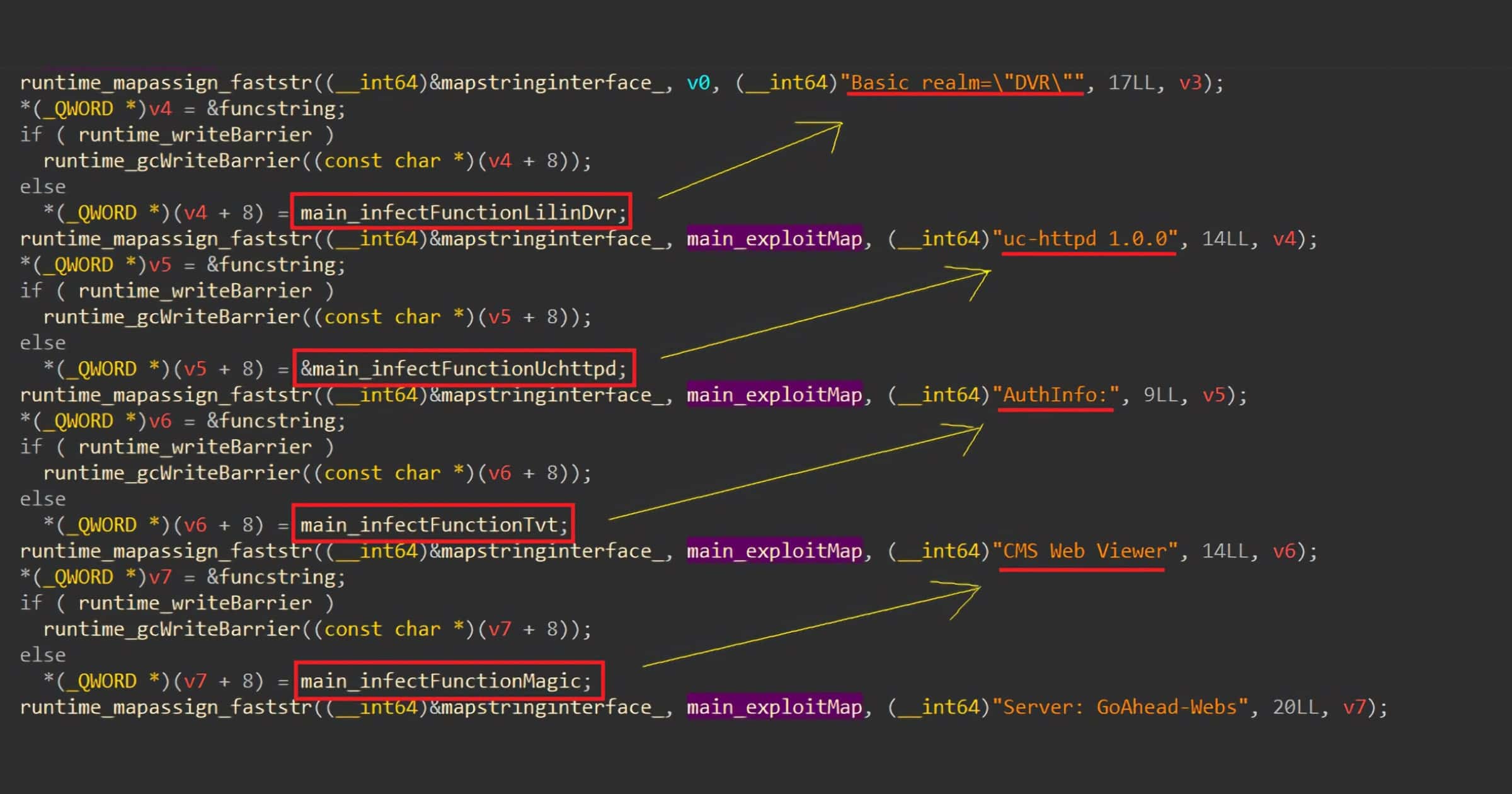
Security researcher Jeremiah Fowler together with the WebsitePlanet research team found an unprotected database belonging to Deep6. The records appear to contain data of those based in the United States.
Update: Deep6 reached out and said the news is misleading, saying “In August, a security researcher accessed a test environment that contained dummy data from MIT’s Medical Information Mart of Intensive Care (MIMIC) system, an industry standard source for de-identified health-related test data. To confirm, no real patient data or records were included in this ephemeral test environment, and it was completely isolated from our production systems.”
Meanwhile, according to WebsitePlanet, Mr. Fowler said, “I sent 3 follow up emails on Aug 11, Aug 12, Aug 23. No one has ever replied since the first message on Aug 10th. I validated that the doctor’s names were real individuals by searching obscure names (see screenshot). This is highly unusual in my experience to use real individuals’ data in a ‘dummy environment’ under any circumstances. Because no one replied, we added our disclaimer that we are highlighting that no patient data appeared in plain text, the records were “medical related”, and we never implied any wrongdoing or risk.”