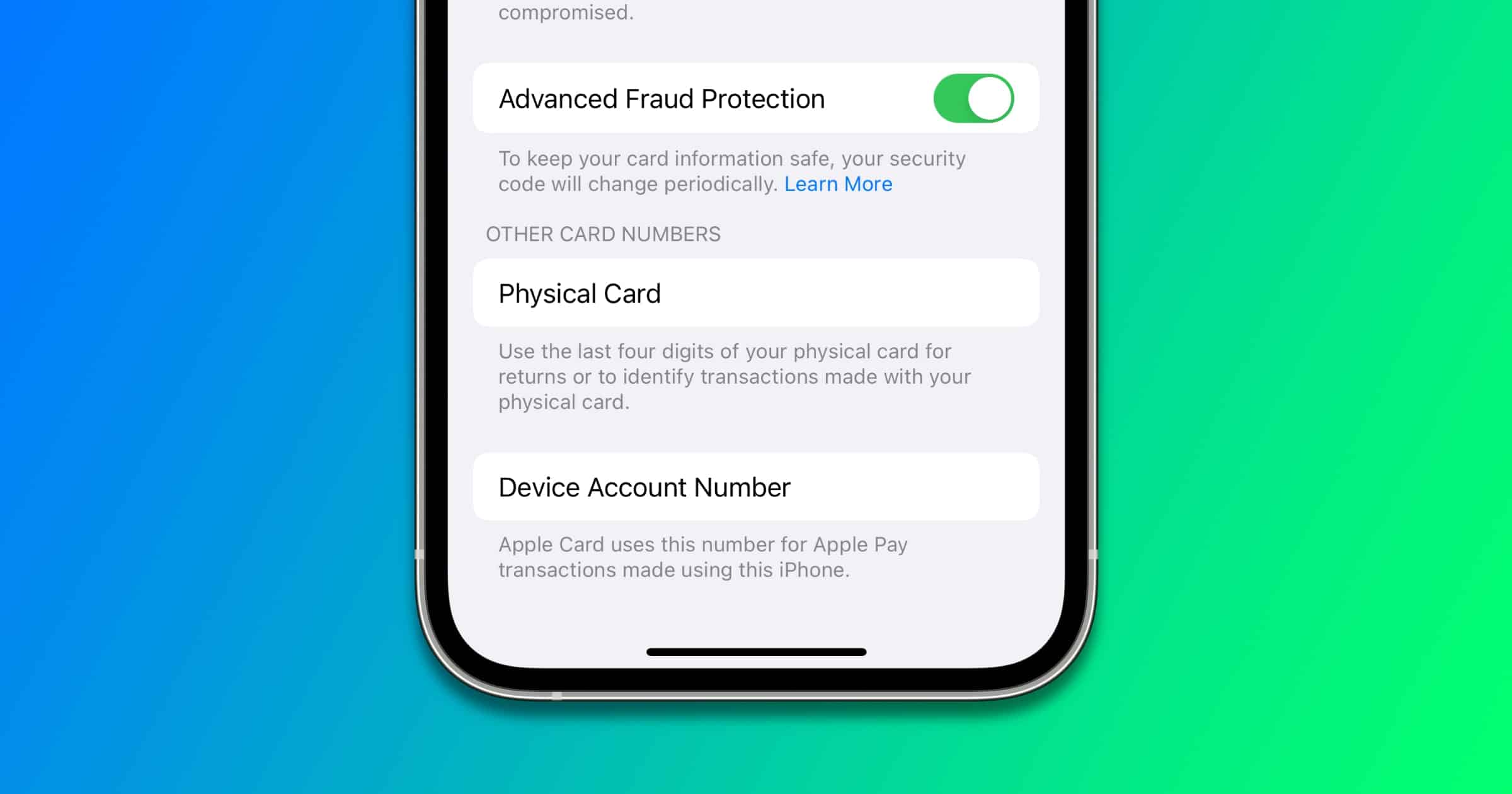
Apple is enabling an Advanced Fraud Protection feature for Apple Card customers. It lets you regularly change your CVV.
Security Friday
Alaska Health Service Attacked by Nation-State Cyber Attacker
The Department of Health and Social Service (DHSS) disclosed that it was the victim of a sophisticated cyberattack from a nation-state level actor.
Citing an investigation conducted together with security firm Mandiant, DHSS officials said the attackers gained access to the department’s internal network through a vulnerability in one of its websites and “spread from there.”
Officials said they believe to have expelled the attacker from their network; however, there is still an investigation taking place into what the attackers might have accessed.
Grain Cooperative 'New Cooperative Inc' Hit with BlackMatter Ransomware Attack
Cyber gang BlackMatter has attacked Iowa-based grain cooperative New Cooperative Inc with ransomware, successfully shutting down its systems.
The attack occurred on or around Friday, according to Allan Liska, senior threat analyst at the cybersecurity firm Recorded Future Inc. The ransomware gang, which goes by the name BlackMatter, is demanding a $5.9 million ransom, Liska said.
New Cooperative confirmed that they had been attacked and said they had contacted law enforcement and were working with data security experts to investigate and remediate the situation.
Security Friday: Phishin and Strippin – TMO Daily Observations 2021-09-17
Andrew Orr and Kelly Guimont discuss Security Friday news and updates, including new phishing scams and sketchy wifi networks.
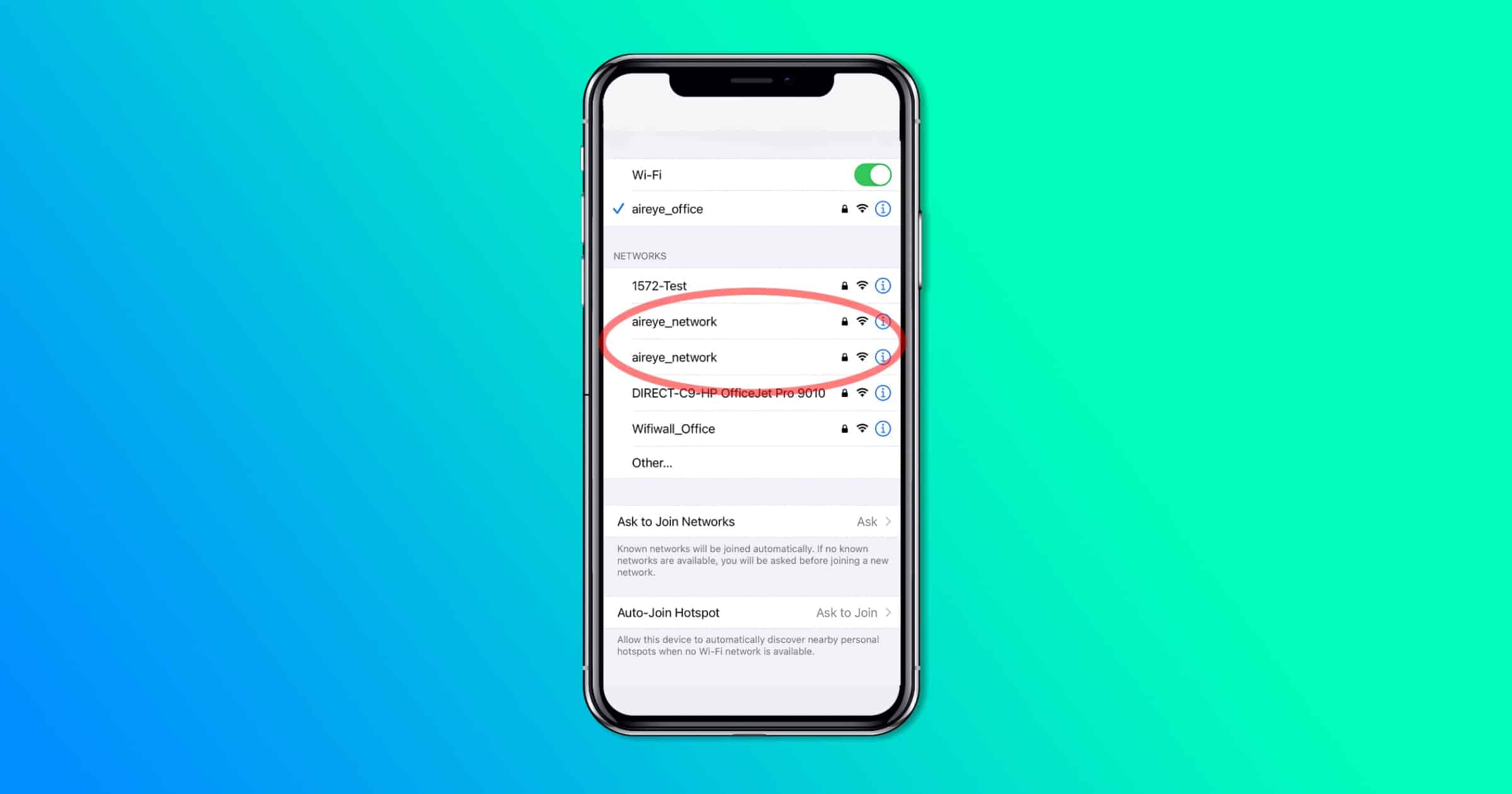
'SSID Stripping' Can Trick You Into Joining a Malicious Wi-Fi Network
Researchers have discovered a new type of network vulnerability dubbed SSID Stripping. It causes a network name to appear differently in a device’s list of networks, thus tricking people into joining a malicious network.
The SSID Stripping vulnerability affects all major software platforms – Microsoft Windows, Apple iOS and macOS, Android and Ubuntu. With SSID Stripping, it is possible to create a network name in a way that its display only shows a prefix that is similar to a legitimate network name (e.g. the corporate network name) while the actual network name includes the additional specially crafted information.
Researchers Uncover a Phishing Kit Used by Two Criminal Gangs
Led by Noam Rotem, vpnMentor’s research team has discovered two separate criminal gangs using slightly altered versions of the same phishing kit to scam people across the globe.
It appears the phishing kit was being used to target people mostly living in Israel and France by two separate criminal gangs. However, we believe these two groups operate phishing websites and SMS operations based on the same phishing kit, possibly obtained from the same source. In addition, at least one of them is potentially affiliated with the OpIsrael political hacking group.
Security Researcher Finds CloudKit Bug That Broke Apple Shortcuts
Security researcher Frans Rosén wrote about a CloudKit bug he accidentally found that affected Apple News, Shortcuts, and iCrowd+.
On the third day, I started to connect the dots, realized how certain assets connected to other assets, and started to understand more how things worked. This is when some of the first bugs popped up, finally restoring my self-esteem a bit, making me more relaxed and focused going forward.
I dug up an old jailbroken iPad I had, which allowed me to proxy all content through my laptop. I downloaded all Apple owned apps and started looking at the traffic.
Coinbase Adds Option for Two-Factor Authentication Security Keys
Cryptocurrency exchange Coinbase announced an important update to its mobile app. Users can now secure their accounts with a two-factor authentication security key.
Hardware security keys are encrypted USB devices that you can register with your Coinbase account as a strong form of physical 2FA. Once registered, you’ll be prompted for your security key when logging in. You then plug in the key, or tap via near field communication (NFC), to your mobile device to securely access your account.
'GetHealth' Leaks Apple HealthKit Data With 61 Million Records
GetHealth, a health and wellness company in New York City, leaked data from a non-password protected database with over 61 million records.
Security Friday and Epic Updates – TMO Daily Observations 2021-09-10
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and the latest in the Apple v Epic lawsuit.
Security Researchers are Fed Up With Apple's Bug Bounty Program
For five years Apple has invited ethical hackers to break into its products to look for flaws. But these security experts are tired of the program.
The best programs support open conversations between the hackers and the company. Apple, already known for being tight-lipped, limits communication and feedback on why it chooses to pay or not pay for a bug, according to security researchers who have submitted bugs to the bounty program and a former employee who spoke on the condition of anonymity because of a nondisclosure agreement.
Germany Secretly Purchased NSO Group Spyware 'Pegasus'
A report reveals that Germany’s Federal Criminal Police Office (BKA) had purchased the Pegasus spyware to monitor suspects.
Security Friday: News, Leaks vs Breaches, Metadata – TMO Daily Observations 2021-08-27
Andrew Orr joins host Kelly Guimont to discuss data leads vs data breaches, security news, and what metadata actually entails.
Your Internet Activity May be Traceable Even Through a VPN
Netflow data refers to IP network traffic that can be collected as it enters or exits an interface. Using this aggregate data, it’s possible to trace network traffic even if a person uses a VPN. Internet service providers sell this information to third parties.
At a high level, netflow data creates a picture of traffic flow and volume across a network. It can show which server communicated with another, information that may ordinarily only be available to the server owner or the ISP carrying the traffic. Crucially, this data can be used for, among other things, tracking traffic through virtual private networks, which are used to mask where someone is connecting to a server from, and by extension, their approximate physical location.
Social Engineering Majority of Business Attacks in 2020
Speaking of social engineering, new data from Atlas VPN shows this kind of attack was responsible for the majority of business breaches in 2020.
According to the data presented by the Atlas VPN team, social engineering cyberattacks were the primary cause of company breaches in 2020 at 14%, followed by advanced persistent threats, unpatched systems and ransomware. As a result, learning to prevent social engineering attacks needs to be a top priority for businesses.
Scammer Stole Over 620,000 iCloud Photos Looking for Nudes
Hao Kuo Chi, 40, of La Puente, has agreed to plead guilty to four felonies, including conspiracy to gain unauthorized access to a computer.
Tim Cook, Satya Nadella, Andy Jassy to Visit White House for Cybersecurity
The CEOs of Apple, Microsoft, and Amazon will attend a meeting at the White House to discuss cybersecurity.
Misconfigured Microsoft Power Apps Leaked 38 Million Database Records
Over a thousand web apps from Microsoft’s Power Apps platform have leaked 38 million records. This data includes COVID-19 contact tracing.
The data included a range of sensitive information, from people’s phone numbers and home addresses to social security numbers and COVID-19 vaccination status.
The incident affected major companies and organizations, including American Airlines, Ford, the transportation and logistics company J.B. Hunt, the Maryland Department of Health, the New York City Municipal Transportation Authority, and New York City public schools.
Security Friday: This Week In Data Breaches – TMO Daily Observations 2021-08-20
Andrew Orr and Kelly Guimont chat about the latest Security Friday news, including data breaches and ways to protect your data.
Since 2015 Cyber Attacks Have Cost Companies Over $25 Billion
A report on Wednesday shows that the damage from cyber attacks has reached over US$$25 billion since 2015.
The most costly attacks are credential attacks (the theft of an organization or individual’s passwords), which have accounted for $6.4 billion in company losses. Often, these credentials are stolen and then sold on the dark web, which happened in the recent T-Mobile breach. Backdoors, like what was used in the SolarWinds hack, have cost companies $5.6 billion.
Smart Home Cameras, Baby Monitors Affected by Software Bug
A flaw in the ThroughTek “Kalay” network affects millions of IoT devices including smart baby monitors, DVRs, smart cameras, and other products.
this latest vulnerability allows attackers to communicate with devices remotely. As a result, further attacks could include actions that would allow an adversary to remotely control affected devices and could potentially lead to remote code execution.
Due to how the Kalay protocol is integrated by original equipment manufacturers (“OEMs”) and resellers before devices reach consumers, Mandiant is unable to determine a complete list of products and companies affected by the discovered vulnerability.
GitHub No Longer Accepts Passwords, Use Security Keys Instead
GitHub will no longer accept passwords when authenticating Git operations and will require the use of strong authentication factors. Yubico also posted about the announcement here, and its 2FA hardware keys are an acceptable solution for GitHub users.
In December, we announced that beginning August 13, 2021, GitHub will no longer accept account passwords when authenticating Git operations and will require the use of strong authentication factors, such as a personal access token, SSH keys (for developers), or an OAuth or GitHub App installation token (for integrators) for all authenticated Git operations on GitHub.com. With the August 13 sunset date behind us, we no longer accept password authentication for Git operations.
Thousands of Wikipedia Pages Vandalized With Swastikas
On Monday morning thousands of Wikipedia pages were vandalized with swastikas. The vandalism was reversed and admins are fixing the issue.