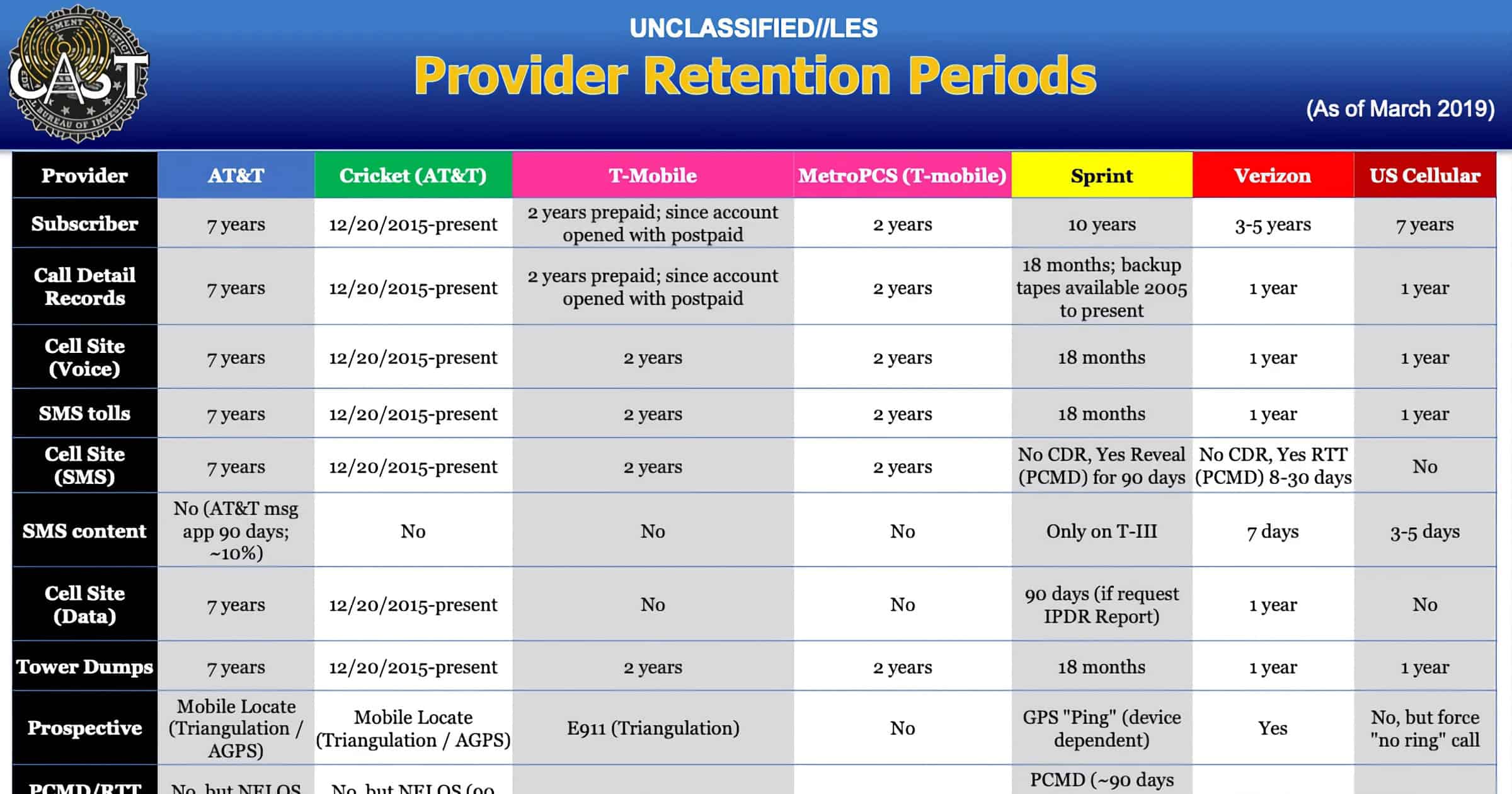
An internal document for the FBI reveals how the agency obtains phone location data from carriers like AT&T, Verizon, and others.
Security Friday
Security Friday: News and Apple Watch Tips – TMO Daily Observations 2021-10-22
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and updates on ransomware and hacking, and share how your Watch can make you safer.
'REvil' Ransomware Group Taken Down Through Multi-Country Effort
The FBI, working with Cyber Command, the Secret Service, and other countries, took down REvil.
According to three people familiar with the matter, law enforcement and intelligence cyber specialists were able to hack REvil’s computer network infrastructure, obtaining control of at least some of their servers. After websites that the hacker group used to conduct business went offline in July, the main spokesman for the group, who calls himself “Unknown,” vanished from the internet.
US Bans Export of Hacking Tools to Authoritarian Regimes
The Commerce Department’s Bureau of Industry and Security (BIS) announced new rules for hacking tools and their export to other countries.
Ransomware Attack on Sinclair Broadcasting Linked to Russian Group 'Evil Corp'
Last weekend, Sinclair Broadcast Group found itself the victim of a ransomware attack, and sources claim Russian group Evil Corp. was behind it.
Missouri Governor Pursues Journalist Who Read Website Code
Missouri Governor Mike Parson wants to prosecute a journalist who discovered the government’s website was leaking Social Security Numbers.
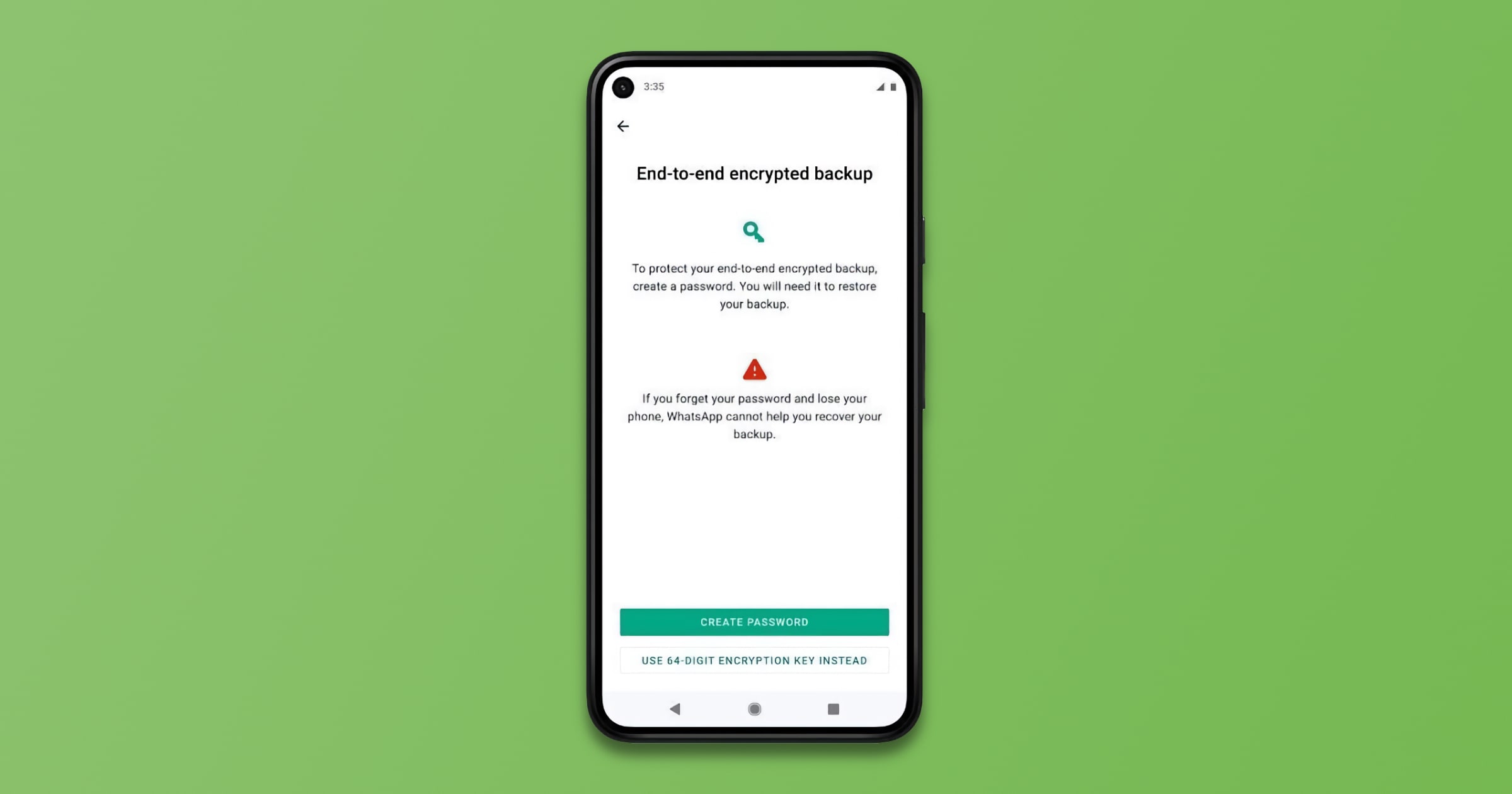
WhatsApp Rolls Out Support for End-To-End Encrypted Backups
WhatsApp is rolling out support for end-to-end encrypted backups for Google Drive and iCloud. Here’s how to enable the feature.
Make sure you’ve got the latest version of WhatsApp.
Open Settings.
Tap Chats > Chat Backup > End-to-end Encrypted Backup.
Click Continue, then follow the prompts to create your password or 64-digit encryption key.
Hit Done, and wait for your end-to-end encrypted backup to be prepared. You may need to connect to a power source.
Customer Accounts of 'Visible' Phone Carrier Hacked, Unauthorized Purchases Made
Visible, a carrier owned by Verizon, suffered what some believed was a data breach on Wednesday, with some customer accounts hacked.
1Password Users Can Now Share Passwords and Other Data
1Password announced on Tuesday that its users can now share virtually anything inside their vault, even if the recipient doesn’t use 1Password.
iOS 15.0.2 Fixes a Zero-Day Bug That May Have Been Exploited
Along with bug fixes, iOS 15.0.2 released on Monday patches a zero-day exploit that Apple believes may have been actively used.
Secure Your Stuff Friday: Twitch and Licenses – TMO Daily Observations 2021-10-08
Andrew Orr and Kelly Guimont talk about the latest Security Friday headlines including Twitch and a new standard for ID on phones.
Anonymous Hacker Shares Twitch Source Code and Payout Data
An anonymous hacker shares data claimed to be Twitch source code. That’s right, not just Twitch data but Twitch itself, its source code and user payout data.
The user posted a 125GB torrent link to 4chan on Wednesday, stating that the leak was intended to “foster more disruption and competition in the online video streaming space” because “their community is a disgusting toxic cesspool”.
VGC can verify that the files mentioned on 4chan are publicly available to download as described by the anonymous hacker.
I have to chuckle about the part where they go on 4chan to complain about toxic websites. Update: Twitch has confirmed the incident.
Proposed Bill Would Require Disclosures of Ransomware Payments
Under the Ransom Disclosure Act, victims of ransomware who pay their attackers would have to report the payment within 48 hours.
Researcher Discloses Telegram Bug After Disappointing Response From Company
A security researcher has shared a bug with Telegram’s auto-delete feature. But the company has seemingly ignored him.
The researcher contacted Telegram in early March. And after a series of emails and text correspondence between the researcher and Telegram spanning months, the company reached out to Dmitrii in September, finally confirming the existence of the bug and collaborating with the researcher during beta testing.
Since then, the researcher claims he has been ghosted by Telegram, which has given no response and no reward.
SMS Routing Company 'Syniverse' Admits it was Hacked in 2016
Syniverse provides backbone services to wireless carriers like AT&T, Verizon, T-Mobile, and several other carriers. It discovered the breach in May 2021 but it began in May of 2016.
Syniverse repeatedly declined to answer specific questions from Motherboard about the scale of the breach and what specific data was affected, but according to a person who works at a telephone carrier, whoever hacked Syniverse could have had access to metadata such as length and cost, caller and receiver’s numbers, the location of the parties in the call, as well as the content of SMS text messages.
Security Friday: Privacy Not Included – TMO Daily Observations 2021-10-01
Andrew Orr joins host Kelly Guimont to discuss Security Friday news including Mozilla’s product guide and an AirTag attack.
Researchers Hack Apple Pay to Steal Money With Visa
Apple claims that the problem lies with Visa’s network, while Visa says the payments are secure and “attacks of this type were impractical outside of a lab.”
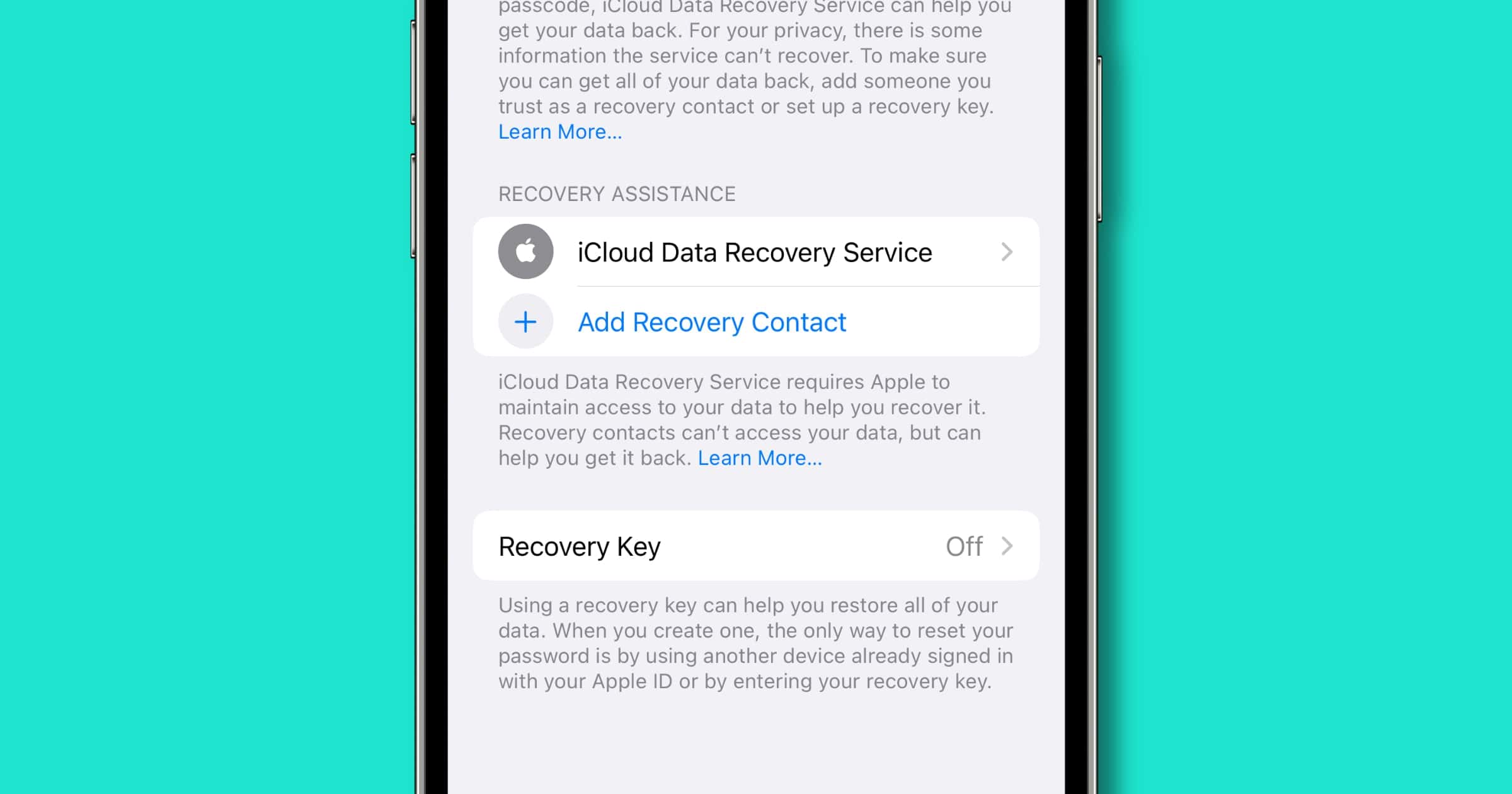
iOS 15: Here's How to Set Up an iCloud Data Recovery Contact
In recent versions of its operating systems, Apple has added a way to set up an iCloud Data Recovery contact.
'FinSpy' Spyware is Adept at Hiding Itself With a Four-Layer Method
FinSpy, a well-known piece of spyware from German company FinFisher, is good at hiding. Researchers at Kaspersky have reverse-engineered the malware.
In addition to a four-layer obfuscation method, the spyware also now employs a UEFI (Unified Extensible Firmware Interface) bootkit for infecting its targets, and it also encrypts the malware in memory, according to the researchers. The Kaspersky team’s research began in 2019, and they are finally sharing their findings today at Kaspersky’s online Security Analyst Summit.
AirTag Zero Day Found That Could Steal Your iCloud Password
A security researcher found a zero-day bug with AirTag that could let an attacker potentially steal your Apple ID.
Apple’s “Lost Mode” allows a user to mark their Airtag as missing if they have misplaced it. This generates a unique https://found.apple.com page, which contains the Airtag’s serial number, and the phone number and personal message of the Airtag owner.
1Password Adds Email Aliases Powered by Fastmail Called 'Masked Email'
1Password has teamed up with Fastmail to give users a way to create email aliases when signing up for accounts.
Security Friday: Bad, Real Bad, and Good News – TMO Daily Observations 2021-09-23
Andrew Orr joins host Kelly Guimont for a round of Security Friday news, including ransomware, hacking, and a way to protect your Apple Card.
macOS Finder Bug Lets Certain Files Run Arbitrary Commands
Researcher Park Minchan reported a bug within macOS Finder that lets certain files execute commands. It affects all versions of macOS up to Big Sur.
A vulnerability in the way macOS processes inetloc files causes it to run commands embedded inside, the commands it runs can be local to the macOS allowing the execution of arbitrary commands by the user without any warning / prompts.
Originally, inetloc files are shortcuts to an Internet location, such as an RSS feed or a telnet location; and contain the server address and possibly a username and password for SSH and telnet connections; can be created by typing a URL in a text editor and dragging the text to the Desktop.