Like most iOS users, I didn’t think I’d need to know how to remove hackers from my iPhone because malware shouldn’t affect it. Unfortunately, that’s not the case. Although iOS mobile devices rarely get infected by malware, they aren’t impervious to all forms of cyberattacks and fraudulent activities. Carelessness with personal data could lead to a security breach. But don’t worry if you come across hacking attempts. You can still take back your phone from hackers even after their malware attacks slip past your defenses. Keep reading to find out how!
How to Know If My iPhone Is Hacked?
It’s crucial to know the warning signs of an iOS hacking attack. You can mitigate more potential damages to your privacy and security if you stop suspicious activities quickly. Delaying the appropriate security fixes will only give hackers access to more personal data.
Start monitoring your online accounts, digital wallets, and social media profiles, among other attractive targets, more closely if you notice these red flags:
- Unusually slow performance
- Random third-party apps appearing
- Strange notifications popping up continuously
- Shady calls and messages are coming in more frequently
- Unrecognized websites in your browser history
- Unauthorized transactions in your online banking apps
- Suspicious activities on your social media profiles
Can I Stop My iPhone From Being Hacked?
Removing hackers from your iPhone isn’t as complex as you might think. You can already stop several active and future attacks by following these cybersecurity practices.
1. Invest in Advanced iOS and macOS Security Programs
Invest in a good antivirus software program if you don’t already have one. You’ll find dozens of options online, but I suggest going for systems specifically designed for the Apple ecosystem. Remember: iOS only supports specific programs. Antivirus software for Android devices won’t run properly on Apple products, especially if they’re unavailable on the App Store.
Just make sure you do your research before shelling out money. I suggest starting with a reputable option like the Intego Mac Premium Bundle X9. It’s a sophisticated antivirus software program that you can use across various Apple devices, plus its monthly fees cost less than a cup of coffee.
2. Change Your Apple ID Password
Change your Apple ID password the moment you notice suspicious activities on your iPhone. It’s safe to assume that phone hackers already know your login credentials—they’ll continue exploiting your data unless you kick them out of your account.
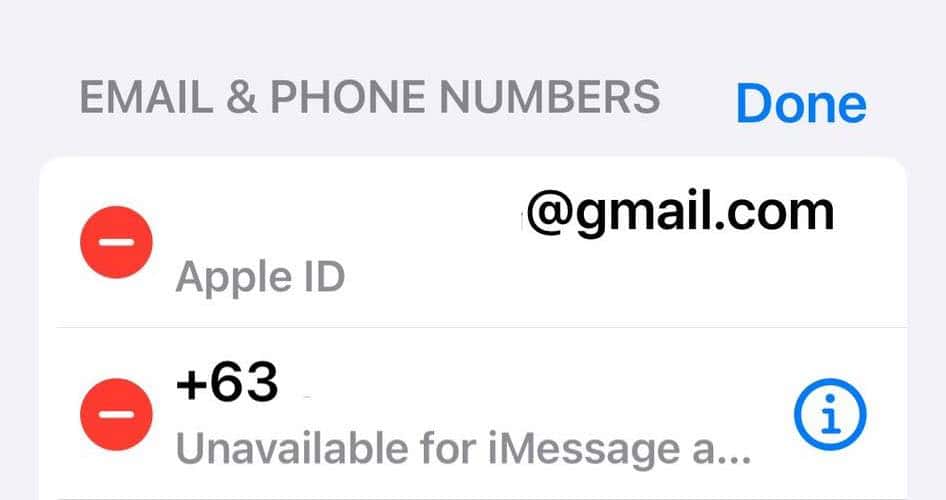
- Open Settings, tap your Apple ID > Sign-In & Security.
- Double-check the contact details linked to your account and remove anything you don’t recognize. Just swipe left on the row you need to edit and tap Delete.
- Afterward, tap Change Password, enter your iPhone passcode, and type your new Apple ID login credentials. Please choose a stronger password that uses alphanumeric and special characters.
- Log your Apple ID out of all devices to ensure hackers don’t retain remote access.
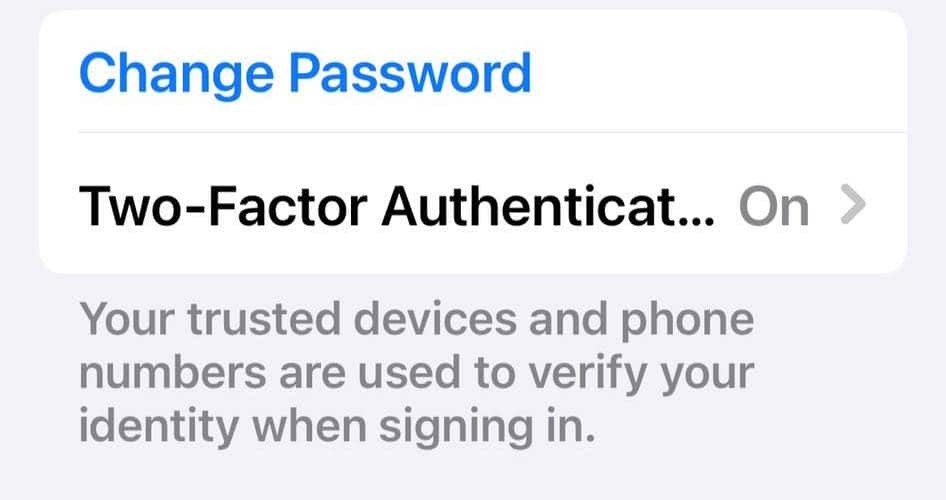
3. Set Up Two-factor Authentication
Prevent similar hacking threats moving forward by setting up two-factor or multi-factor authentication for your Apple ID. It adds an extra layer of security to your login credentials. Even if hackers know your password, they can only access your account if they also have your authenticator device.
- Open Settings, tap your Apple ID > Sign-In & Security.
- Go to Two-Factor Authentication, tap the toggle button, and then request a verification code for confirmation. Just make sure your linked contact details are correct.
- For extra security, you can also set up physical security keys.
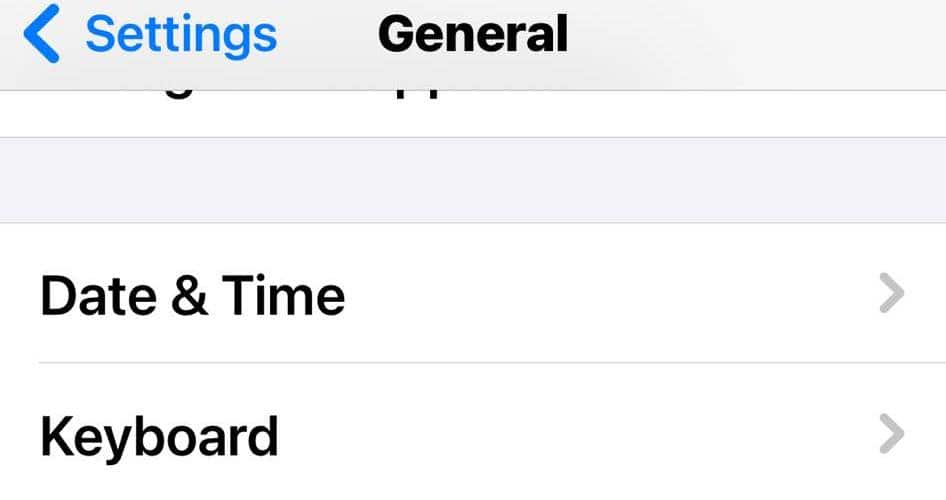
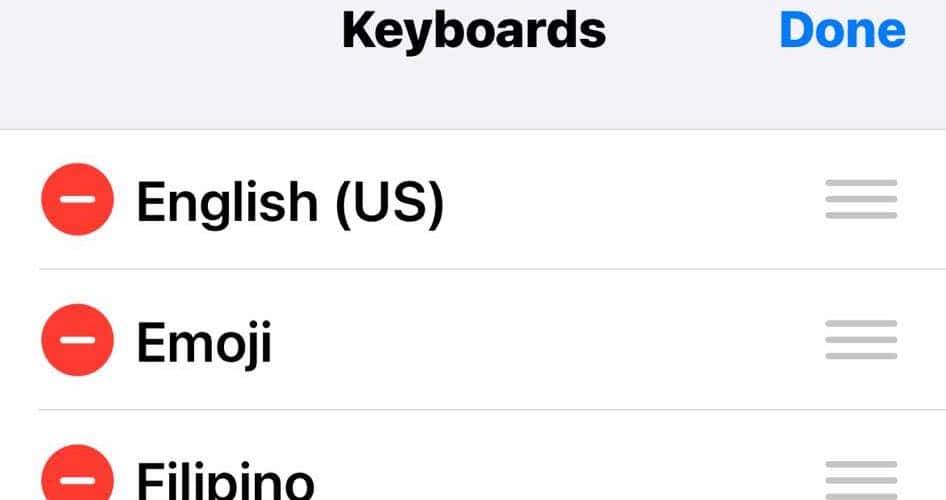
4. Uninstall Custom Keyboards
Hackers can spy on your phone and steal login credentials through keystroke logging, also known as keylogging, tools. They’re often malicious codes disguised as custom keyboards.
- Open Settings > General > Keyboard.
- Go to the Keyboards section and check for custom keyboards that you don’t recognize.
- Delete anything you didn’t install. Either swipe right on the keyboard name’s row or tap Edit at the top-right corner of the screen.
5. Delete Unrecognized Programs
Look for unfamiliar downloads on your iPhone. Like most people, you probably have a long list of apps—it’s easy for malicious programs to hide behind them and masquerade as legitimate applications. Most people don’t even notice them until their mobile phones run out of storage.
The best approach is to look through your phone for apps you don’t recognize. Make sure you launch them because they often use seemingly official icons.
To prevent unwanted installations, only download from the App Store. You should also check your subscriptions routinely and see if you’re unknowingly paying monthly fees for apps you don’t recognize. Open the App Store, tap your profile icon in the top-right corner of the screen, and go to Subscriptions.
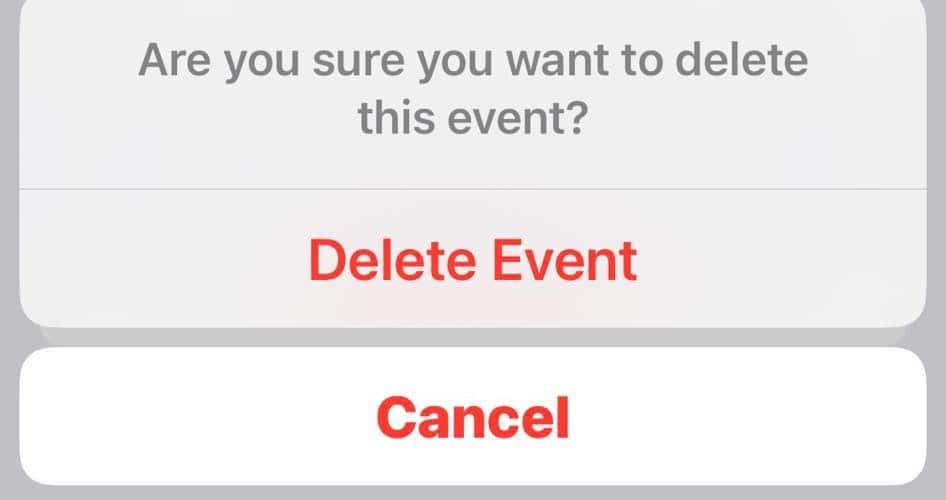
6. Unsubscribe to Random Calendar Events
The calendar virus is a social engineering attack that uses events to send bogus push notifications to your iPhone. Crooks will grab your attention with alarming messages. They might excite you with made-up rewards or scare you with hacking threats. Whatever the case may be, note that they’re fake.
- Although alarming, calendar viruses are virtually harmless if you quickly delete them from your Calendar app. Don’t download files, visit websites, or tap hyperlinks.
- Launch the Calendar app and look for unrecognized events. Zoom out to a monthly view; otherwise, you’ll waste time scrolling through the hourly breakdowns of your days.
- Open the event you need to remove and tap Edit > Delete.
- Repeat until you clear all random calendar events from your iPhone.
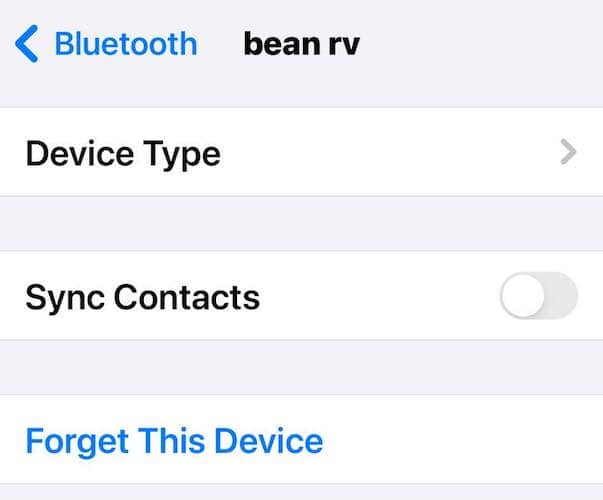
7. Unpair Unauthorized Bluetooth Devices
Protect your device from hackers by turning off Bluetooth and unpairing unauthorized connections. Crooks might send fake alerts and pop-ups through them. They usually target people using public Wi-Fi networks, so stay away from these and use your cellular data instead.
- Open Settings > Bluetooth.
- Tap the information button (i) next to the Bluetooth device you need to disconnect and select Forget This Device.
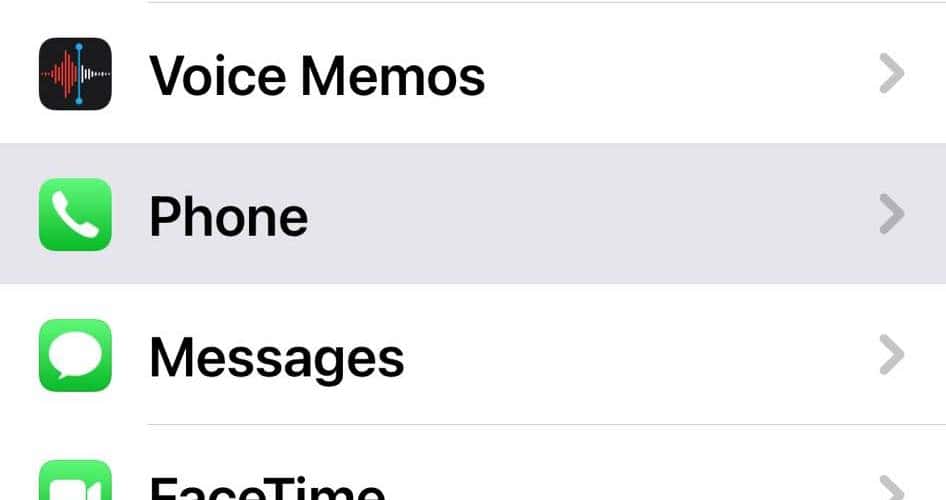
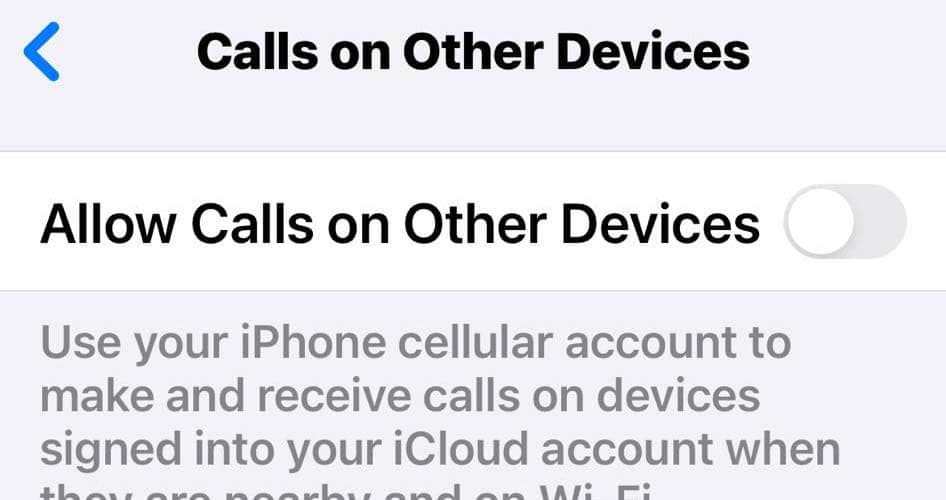
8. Disable the Calls on Other Devices Feature
The Allow Calls on Other Devices feature lets you make and receive calls across all devices linked to your iCloud account. It’s convenient if you’re fully invested in an Apple ecosystem. However, it also presents several security risks as hackers can take over your calls once they bypass your Apple ID password. It’s best to just turn it off to remove hackers from your iPhone.
- Open Settings > Phone > Calls on Other Devices.
- Tap the toggle button to turn off the feature across all your Apple devices.
Conclusion
Doing a factory reset, deleting malicious applications, and enabling 2FA, among other security measures, go a long way in preventing unauthorized access. That said, some malware attacks might still fall through the cracks. Keeping your phone secure is a long-term process; repeat these tips until bad actors can no longer get past your defenses.
Also, protect your other gadgets. Look into antivirus software programs suited for the entire Apple ecosystem.