The FBI’s fight for government mandated backdoors into our encrypted data and devices is far from over, and Director James Comey says he plans to bring that back to the forefront next year. Mr. Comey says it’s time for an “adult conversation” on the topic, and that law enforcement needs an easy way to access our private data for criminal investigations.
Security
Apple Patches 2 Critical Security Flaws in OS X Yosemite and El Capitan
Apple released separate security updates for OS X Yosemite and OS X El Capitan on Thursday. Both updates patch the same two critical security flaws. One flaw potentially exposed kernel memory, and the other allowed a maliciously crafted app to take over your system.
Apple Patches Critical Zero-Day Data Security Exploit in iOS 9.3.5 Update
Apple released iOS 9.3.5 on Thursday to address a big security flaw that could expose iPhone and iPad user’s personal data. The threat could be used to exploit information from email, contacts, text messages, phone calls, and more—and it looks like NSO Group has been doing just that so governments can spy on journalists and people they classify as dissidents.
Checking Your 'Find My Mac' Status (And Why You Might Need To!)
Today’s Quick Tip is about Find My Mac. Are you sure your settings are working properly? Have you checked to be certain you can locate your device if it’s stolen or lost? We’ll tell you how!
Apple Patches Pangu Jailbreak Exploit with iOS 9.3.4
Apple released iOS 9.3.4 on Thursday, only a couple weeks after rolling out iOS 9.3.3. This surprise update shuts down the Pangu jailbreak, and the credit card and PayPal security breaches that came along with it.
New Security Threat Targets OS X, iOS through Graphics
There’s a new security threat for OS X and iOS that could let attackers remotely control your device or install malware by sending you an image file. The threat is fairly serious, although so far it’s still just a proof of concept, and Apple patched the flaw in OS X 10.11.6 and iOS 9.3.3.
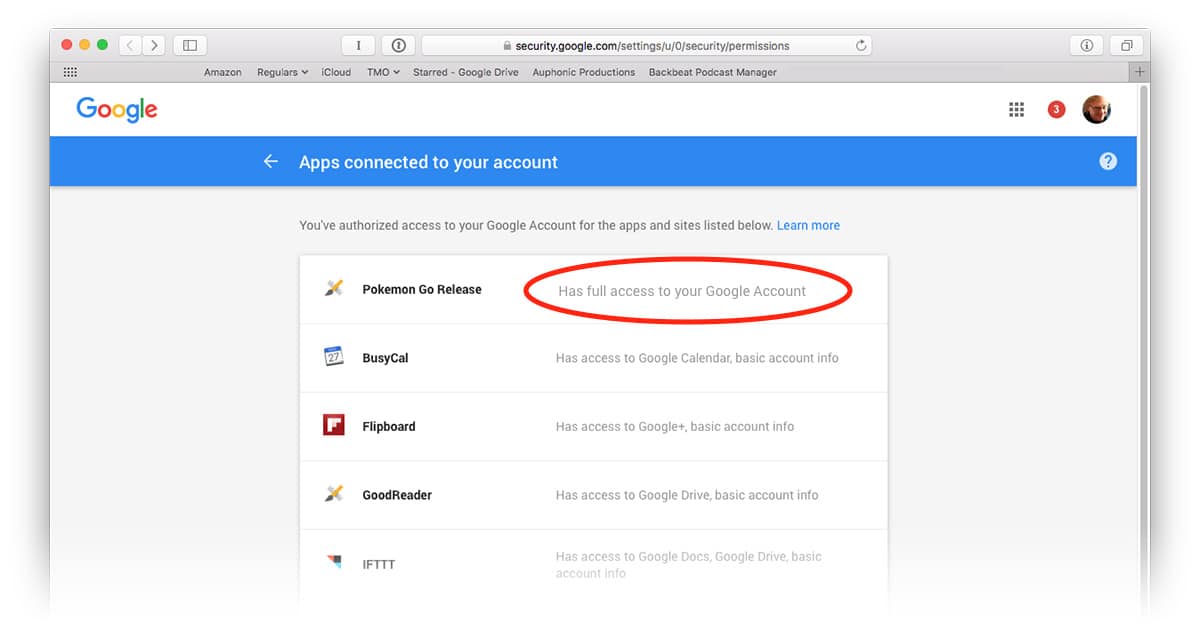
How to Limit Pokémon GO's Access to Your Google Account
Nintendo and Niantic’s wildly popular Pokémon GO came under fire only days after it launched when users found out the game had permission to access everything in their Google accounts. Niantic said the game checked only basic account information and wasn’t supposed to get unfettered access to everything. There’s an patch out that fixes the permissions issue, but you’ll need to do more than simply install the update. Read on to learn how to limit Pokémon GO’s access to your Google account.
Pokémon GO isn't Stealing all Your Data
Pokémon GO is the game to play, and it’s so popular that Nintendo’s servers can’t keep up with demand. That led to loads of people signing up with their Google ID, promptly followed by loads of people freaking out thinking the game is accessing all of their email, contacts, and documents. The game isn’t really stealing all your data, and the developers said they’re fixing the error that granted Pokémon GO full access to your Google account.
Backdoor.MAC.Elanor Malware Access Mac Webcams, Steals Data, More
There’s a new Mac malware threat in the wild dubbed Backdoor.MAC.Elanor that’s particularly nasty because it lets attackers take control of your Mac’s camera, download data from your computer, and remotely run code. Mac users can fall victim to the threat by downloading what otherwise appears to be a legit app and has even shown up on some mainstream Mac software repositories.