Andrew Orr joins host Kelly Guimont for Security Friday news and updates, including This Week in Data Leaks, and an update to a previous tip.
Security
US Forms Joint Cyber Defense Collaborative to Fight Ransomware
CISA is forming an initiative called the Joint Cyber Defense Collaborative along with certain private sector companies such as Google and Microsoft.
Thursdays with Bob: Keyboard and Security Updates – TMO Daily Observations 2021-08-05
Dr Mac joins Kelly to give an update on the ergonomic keyboard search, and plead the case for security updates.
Backup Tool ‘iMazing’ Updated to Detect Pegasus Spyware
The team behind iMazing has updated their tool to detect NSO Group’s Pegasus spyware. You don’t have to buy an iMazing license to scan for it.
It would therefore be possible to relatively quickly re-implement MVT’s methodology in our toolkit, and integrate a user-friendly ‘wizard’ in iMazing’s user interface. And because iMazing can already perform iOS backups and decrypt backup files, the tool we envisaged had the potential to dramatically reduce the technical barrier of entry whilst enhancing performance and promoting backup encryption.
Malware Dubbed ‘Raccoon Stealer’ Targets Crypto Wallets
Researchers at Sophos have been tracking a piece of malware called Raccoon Stealer. A recent update means it can target cryptocurrency wallets.
Raccoon can collect passwords, cookies, and the “autofill” text for websites, including credit card data and other personal identifying information that may be stored by the browser. Thanks to a recent “clipper” update, Raccoon Stealer also now targets cryptocurrency wallets, and can retrieve or drop files on infected systems.
Raffle House Data Leak Exposes Personal Data of ‘Hundreds of Thousands’
Discovered on June 7, 2021, Raffle House suffered a data leak that leaked the personal data of hundreds of thousands of users.
Microsoft Warns Office 365 Users of New Phishing Campaign
Microsoft’s Security Intelligence team issued a warning to be on the lookout for an active phishing campaign targeting Office 365 users.
Hackers Leak FIFA 21 Source Code After Extortion Attempt
After a failed extortion attempt, hackers have leaked a 751GB cache of data stolen from Electronic Arts. The files include the source code for FIFA 21.
While initially, the hackers hoped to earn a big payday from the EA hack, they failed to find any buyers on the underground market, as the stolen data was mostly source code that lacked any value for other cybercrime groups, most of which are interested in user personal or financial data primarily.
After failing to find a buyer, the hackers tried to extort EA, asking the company to pay an undisclosed sum and avoid having the data leaked online.
Security Friday: Prototypes, VPNs, and Social Engineering – TMO Daily Observations 2021-07-30
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and dig into social engineering hacks, with tips on how to avoid them.
Hackers Increasingly Using Discord to Spread Malware
Researchers found that hackers are turning to Discord to spread malware, such as password-hijacking and Discord chat bot APIs.
But the greatest percentage of the malware we found have a focus on credential and personal information theft, a wide variety of stealer malware as well as more versatile RATs. The threat actors behind these operations employed social engineering to spread credential-stealing malware, then use the victims’ harvested Discord credentials to target additional Discord users.
Apple Releases Updates for Macs, iPhones, and iPads
Apple has released updates on Monday with macOS 11.5.1 and iPhone 14.7.1 with bug fixes and security updates.
Security Friday: News and Pegasus – TMO Daily Observations 2021-07-23
Andrew Orr and Bryan Chaffin talk Security Friday news with host Kelly Guimont, then dig into the Pegasus story you’ve heard about this week.
Researchers Hid Malware Inside an AI’s Brain
This is straight out of a sci-fi novel. Researchers created a proof-of-concept technique that let them hide malware inside of an AI’s neurons to avoid detection.
According to the paper, in this approach the malware is “disassembled” when embedded into the network’s neurons, and assembled into functioning malware by a malicious receiver program that can also be used to download the poisoned model via an update. The malware can still be stopped if the target device verifies the model before launching it, according to the paper. It can also be detected using “traditional methods” like static and dynamic analysis.
Worried if You Were Infected by Pegasus? This Tool Can Help
This week, a strain of malware known as Pegasus from NSO Group has been making headlines. It’s used by governments to target journalists, activists, and other people deemed dissidents. But there is a tool that could detect it.
MVT will let you take an entire iPhone backup (or a full system dump if you jailbreak your phone) and feed in for any indicators of compromise (IOCs) known to be used by NSO to deliver Pegasus, such as domain names used in NSO’s infrastructure that might be sent by text message or email.
Hackers Leak ‘Humana’ Data of Over 6,000 Patients
An SQL database containing what appears to be highly sensitive health insurance data of more than 6,000 patients has been leaked on a hacker forum.
The author of the post claims that the data was acquired from US insurance giant Humana and includes detailed medical records of the company’s health plan members dating back to 2019. The leaked information includes patients’ names, IDs, email addresses, password hashes, Medicare Advantage Plan listings, medical treatment data, and more.
So What’s Up With This NSO Group Pegasus Thing Anyway?
Hot news over the weekend reveals that spyware from Israeli company NSO Group may be culpable in the murders of certain journalists.
China Allegedly Behind Microsoft Exchange Hack Revealed in March 2021
The White House has formally accused China of hacking Microsoft Exchange servers, a security campaign that was revealed in March 2021.
NSO Group’s ‘Pegasus’ Spyware Targets Journalists and Activists
Spyware known as Pegasus from NSO Group was used to hack 37 smartphones belonging to journalists, activists, and business executives around the world.
The phones appeared on a list of more than 50,000 numbers that are concentrated in countries known to engage in surveillance of their citizens and also known to have been clients of the Israeli firm, NSO Group, a worldwide leader in the growing and largely unregulated private spyware industry, the investigation found.
Security Friday: News Old and New, and Future Updates – TMO Daily Observations 2021-07-16
Andrew Orr joins host Kelly Guimont to discuss updates to previous Security Friday news, and a couple of items coming to Firefox and iOS.
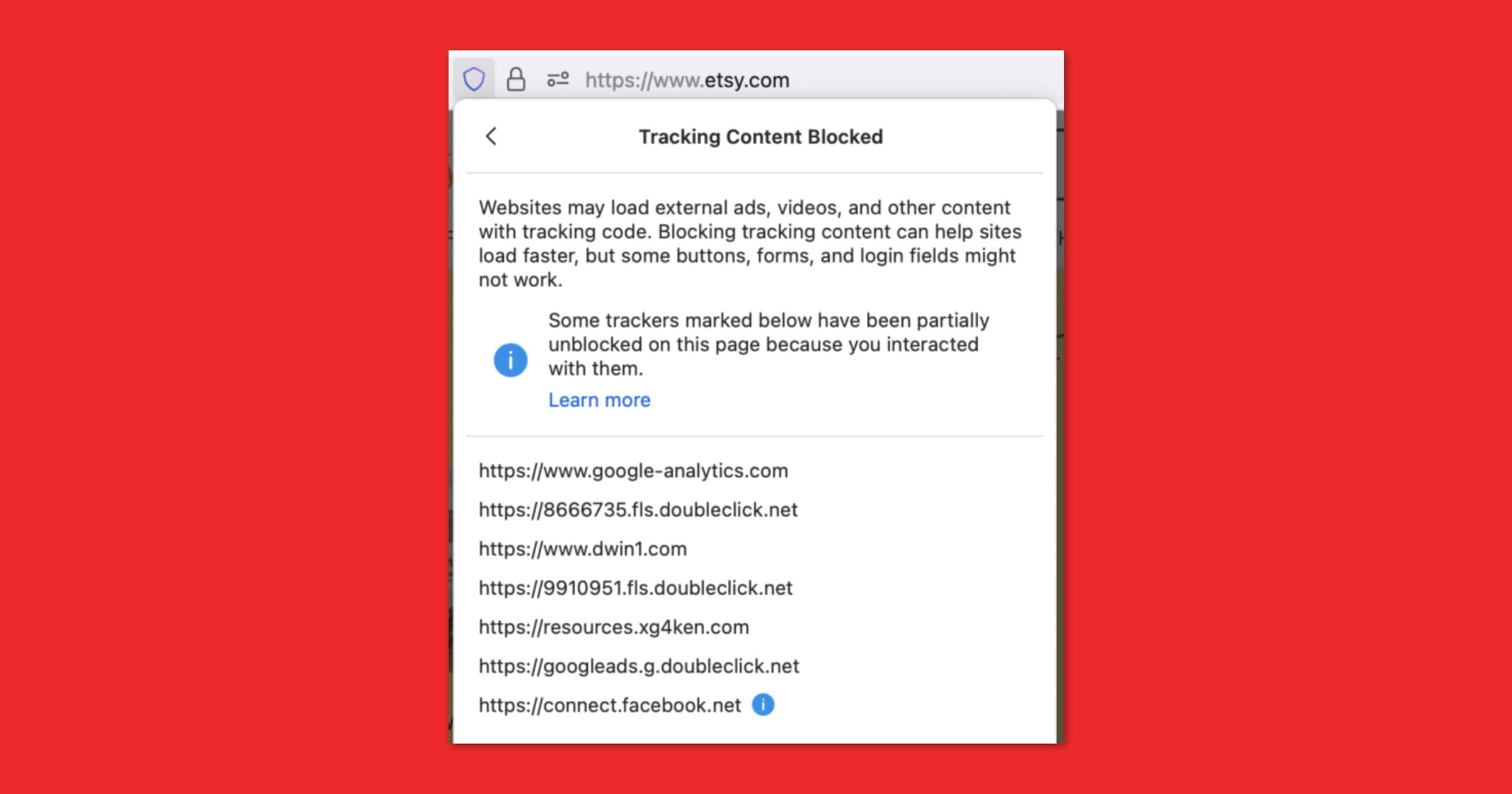
Firefox 90 Update Introduces SmartBlock 2.0 for Tracking Protection
Mozilla released Firefox 90 recently and it comes with an improved version of its tracking protection called SmartBlock 2.0.
The newest version of Mozilla’s built-in SmartBlock privacy feature makes it easier for users to keep their tracking protection settings cranked up, without breaking individual websites. The updated version seems to especially target Facebook login, which is increasingly used around the web as a third-party authentication and login tool.
Image credit: ArsTechnica
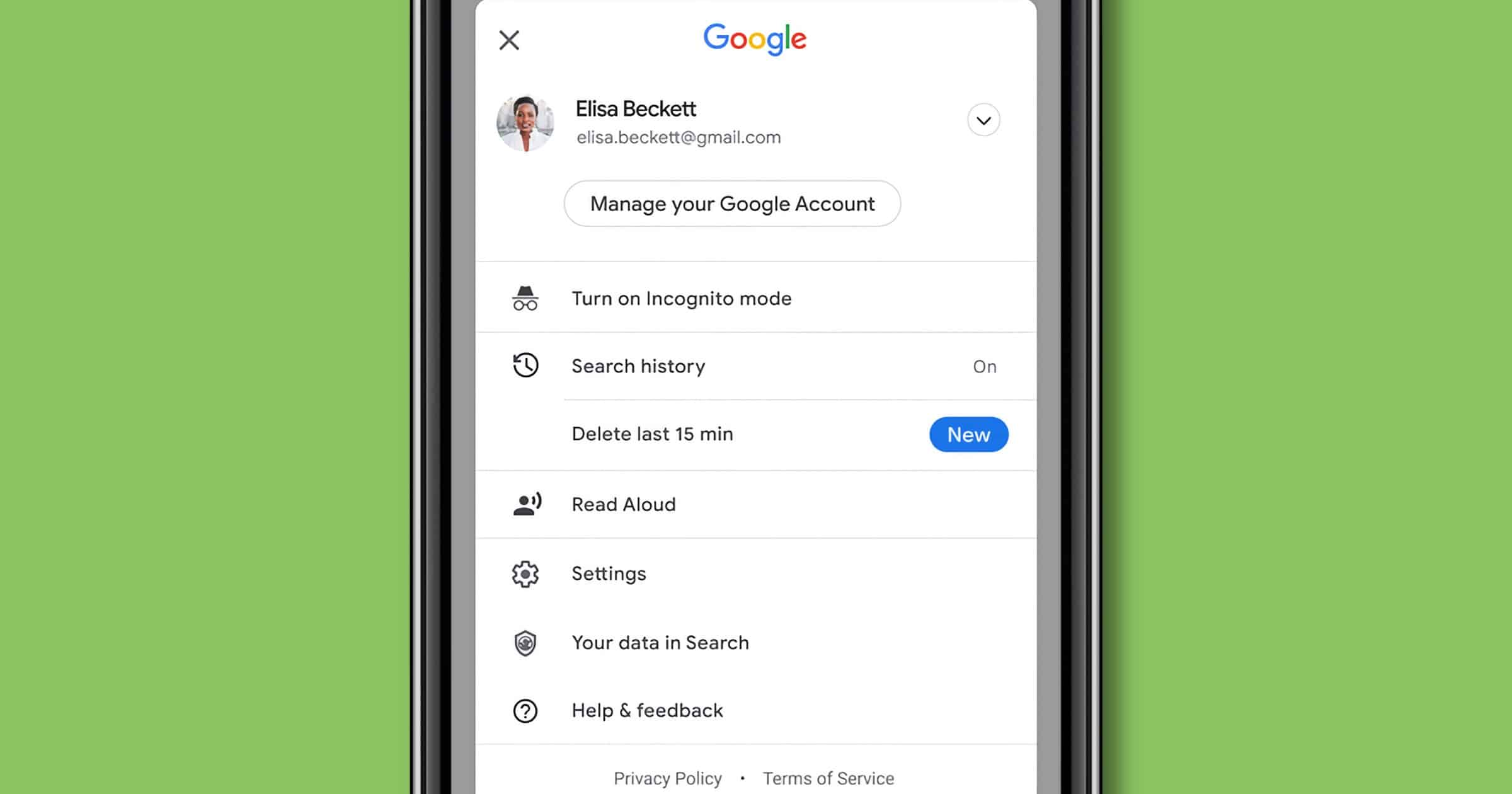
Google Adds Tool to Quickly Delete Your Last 15 Minutes of Searches
Google is adding new protections for your search history like quick deletion, requiring verification to access the My Activity section, and more.
You can also try out a new way to quickly delete your last 15 minutes of saved Search history with the single tap of a button. This feature is available in the Google app for iOS, and is coming to the Android Google app later this year.
You could also just turn disable your search history altogether, too.
‘SolarWinds’ Hackers Used iOS Zero Day Against Government Officials
The Russian hackers behind the SolarWinds attack used an iOS zero day to steal credentials from Western European governments.
Attacks targeting CVE-2021-1879, as the zero-day is tracked, redirected users to domains that installed malicious payloads on fully updated iPhones. The attacks coincided with a campaign by the same hackers who delivered malware to Windows users, the researchers said.
Google published a blog post about zero-days here, and you can read coverage from Ars Technica at the link below.
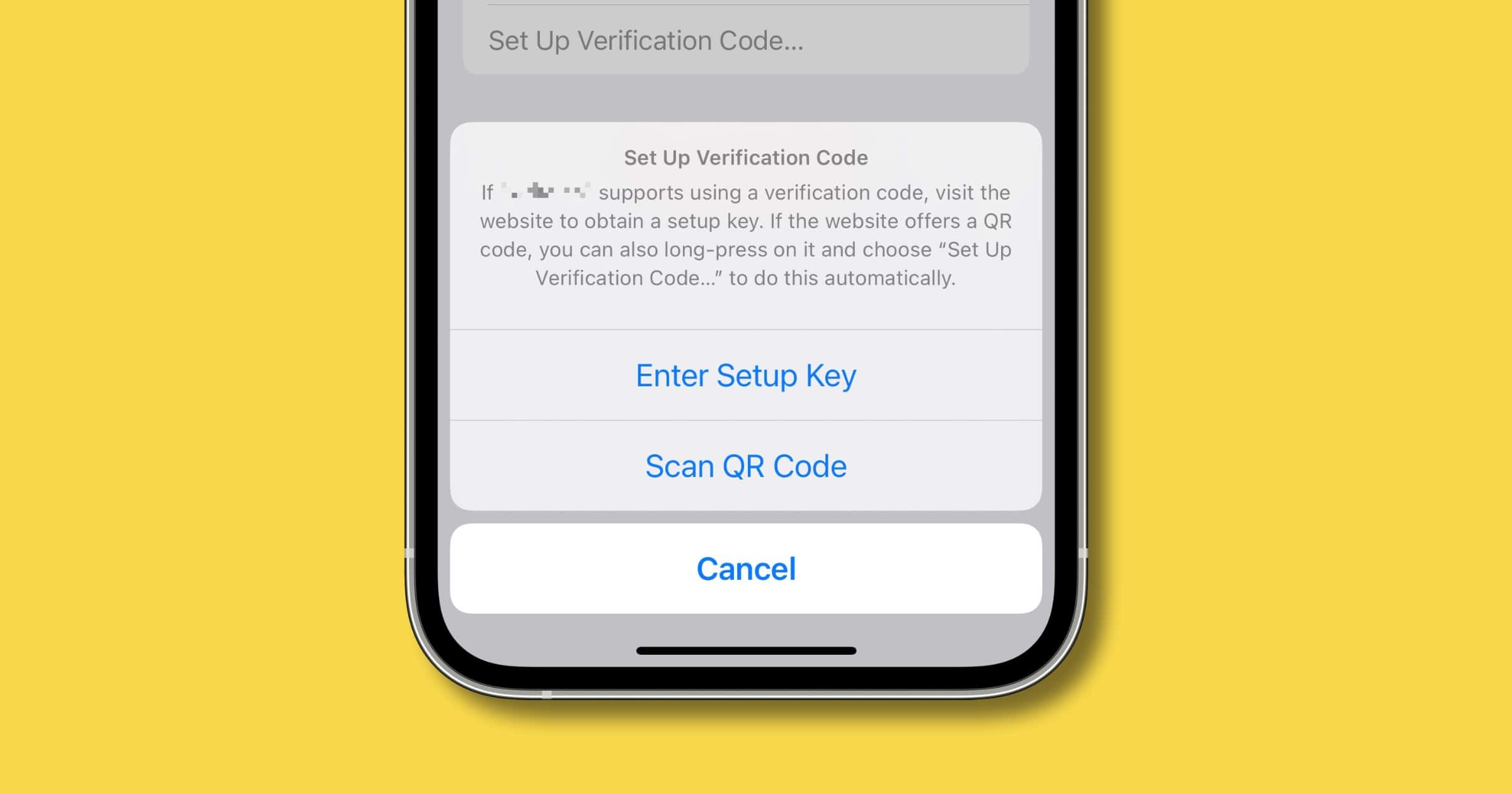
iOS 15: How to Add Two-Factor Authentication Codes to Passwords
A welcome feature in iOS 15 is the ability to add two-factor authentication codes to your passwords. Here’s how to set it up.
Security Friday: News on Data Privacy and a Practical PDF Tip – TMO Daily Observations 2021-07-09
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and updates, including data privacy and how to encrypt a pdf on your Mac.