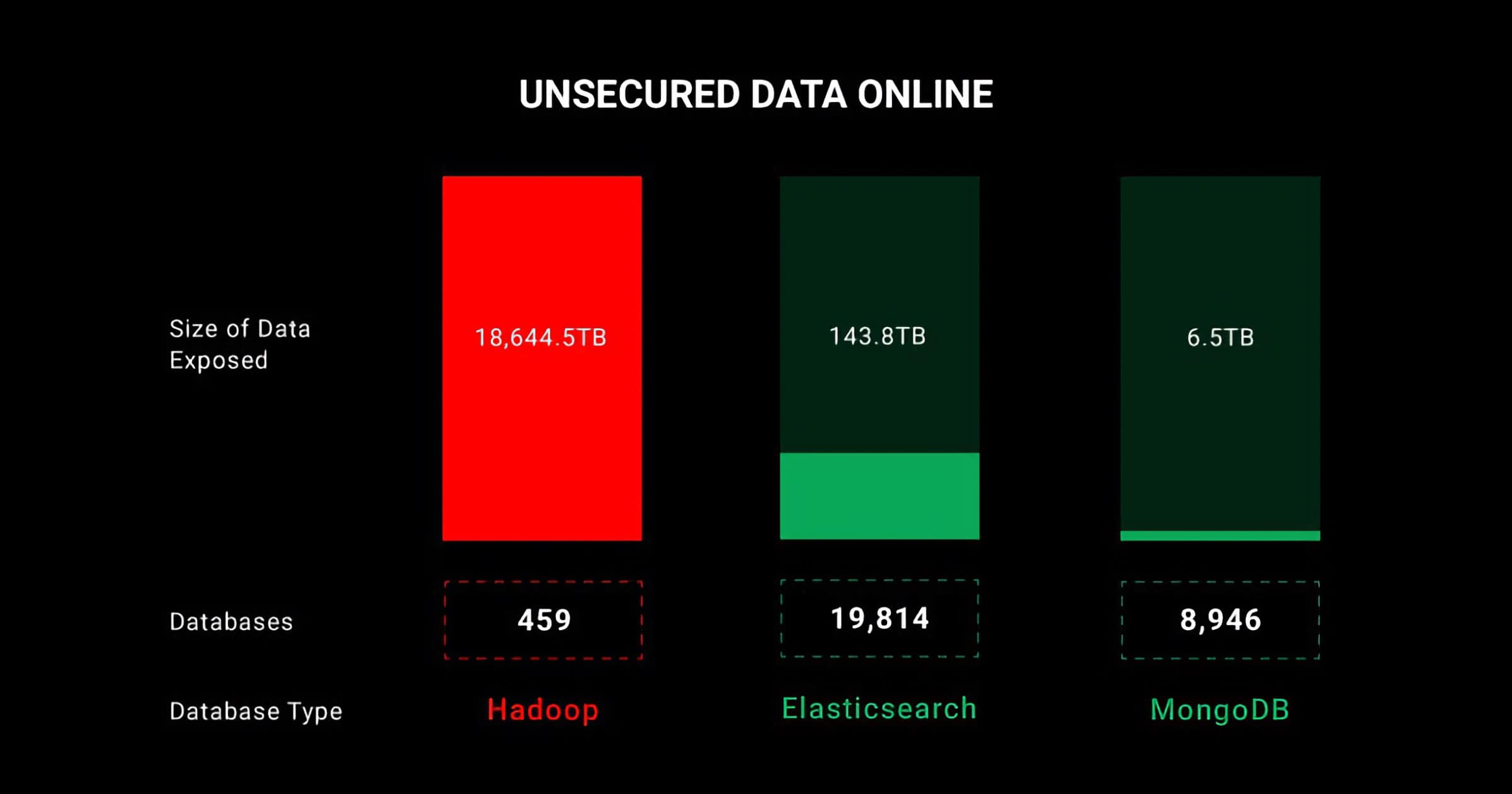
Security researchers at SafetyDetectives found an insecure ElasticSearch database that potentially uncovers over 200,000 fake Amazon reviewers.
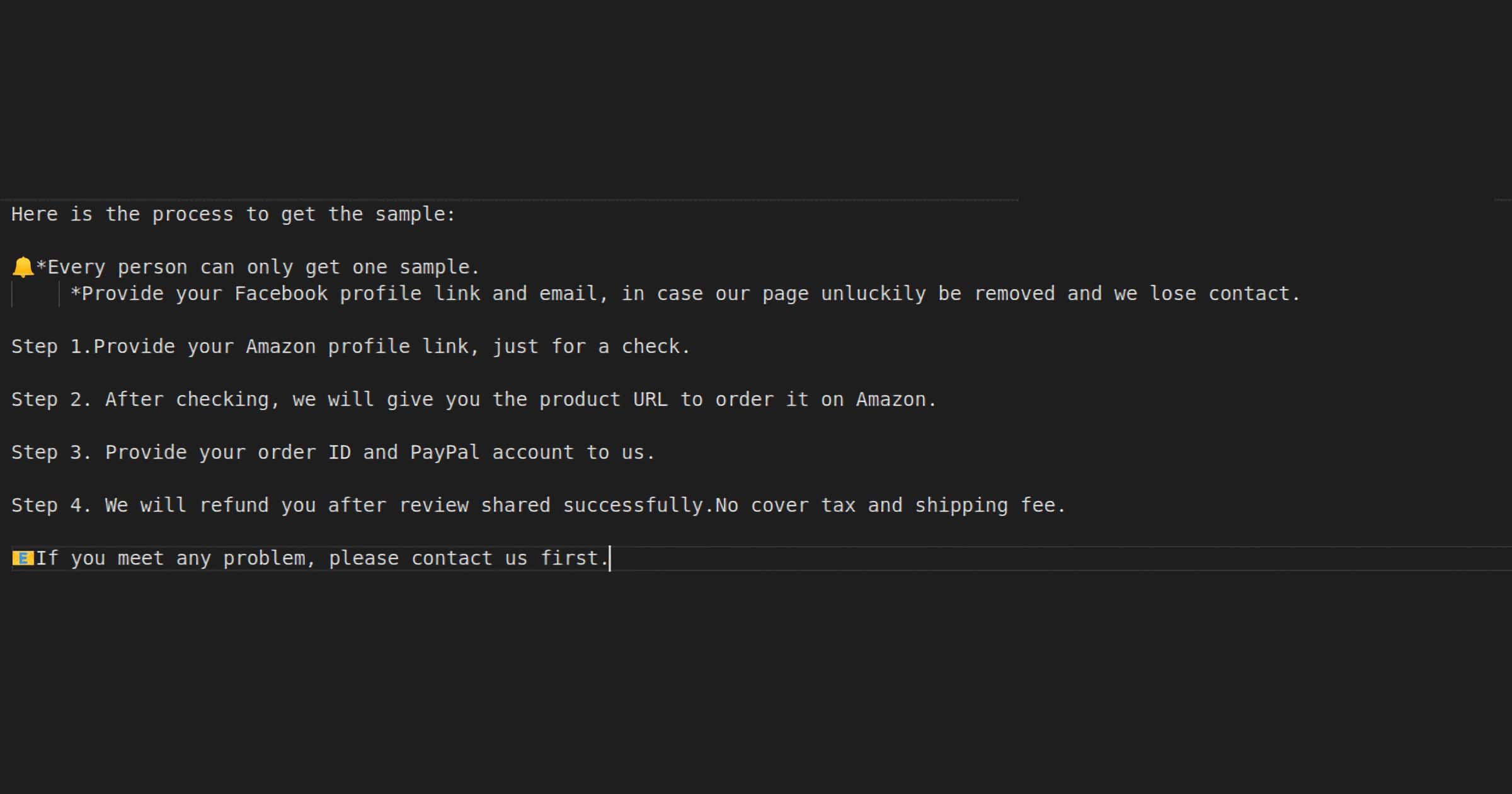
These Amazon vendors send to reviewers a list of items/products for which they would like a 5-star review. The people providing the ‘fake reviews’ will then buy the products, leaving a 5-star review on Amazon a few days after receiving their merchandise.
Upon completion, the provider of the fake review will send a message to the vendor containing a link to their Amazon profile, along with their PayPal details.