Andrew Orr and Kelly Guimont discuss Security Friday updates, including some suggested beverage pairings for each topic.
Security
Intuit Warns Customers of Tax Phishing Emails
Intuit has released security warnings for customers about tax phishing emails some people have received, and tips to spot them.
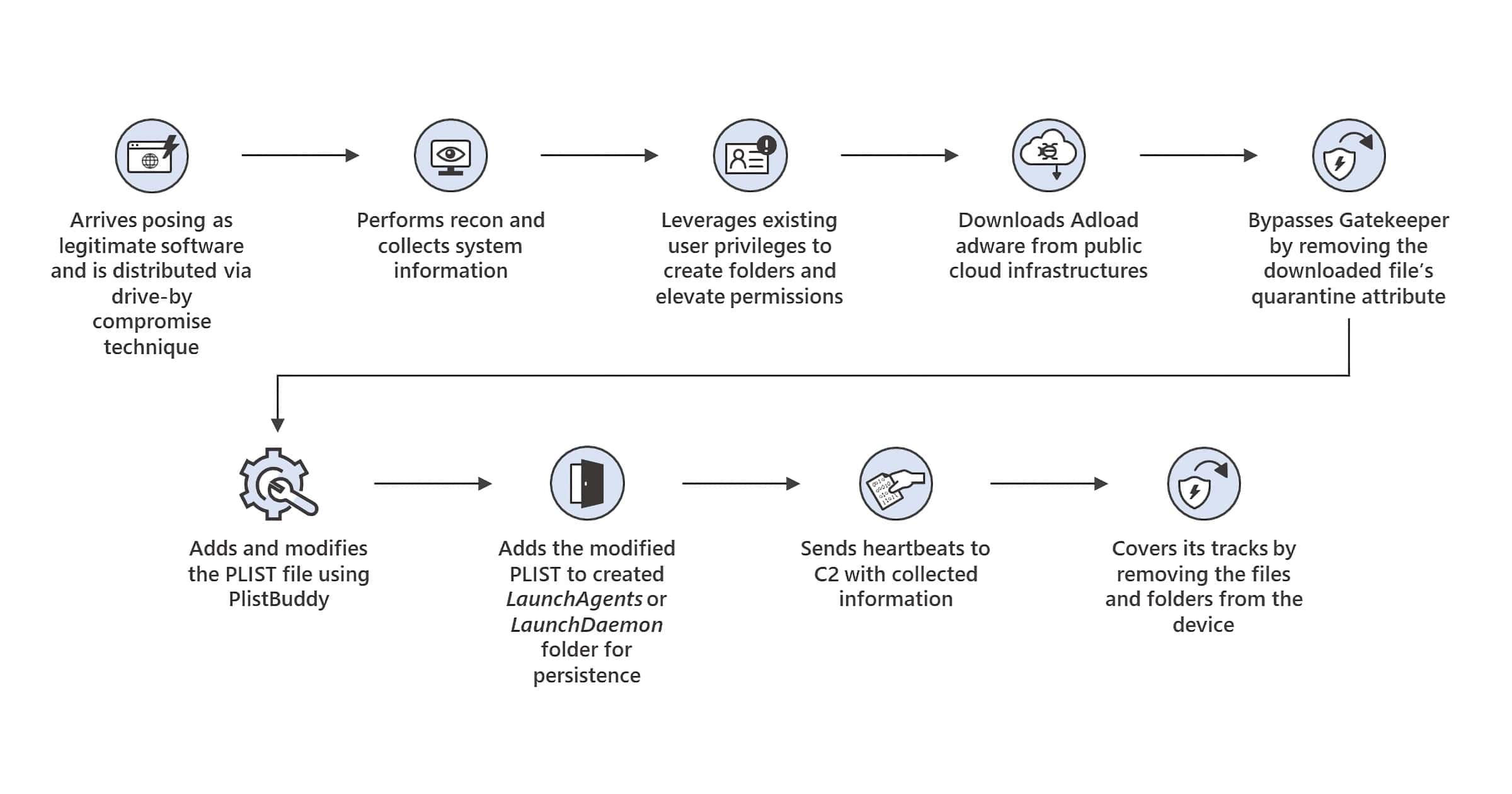
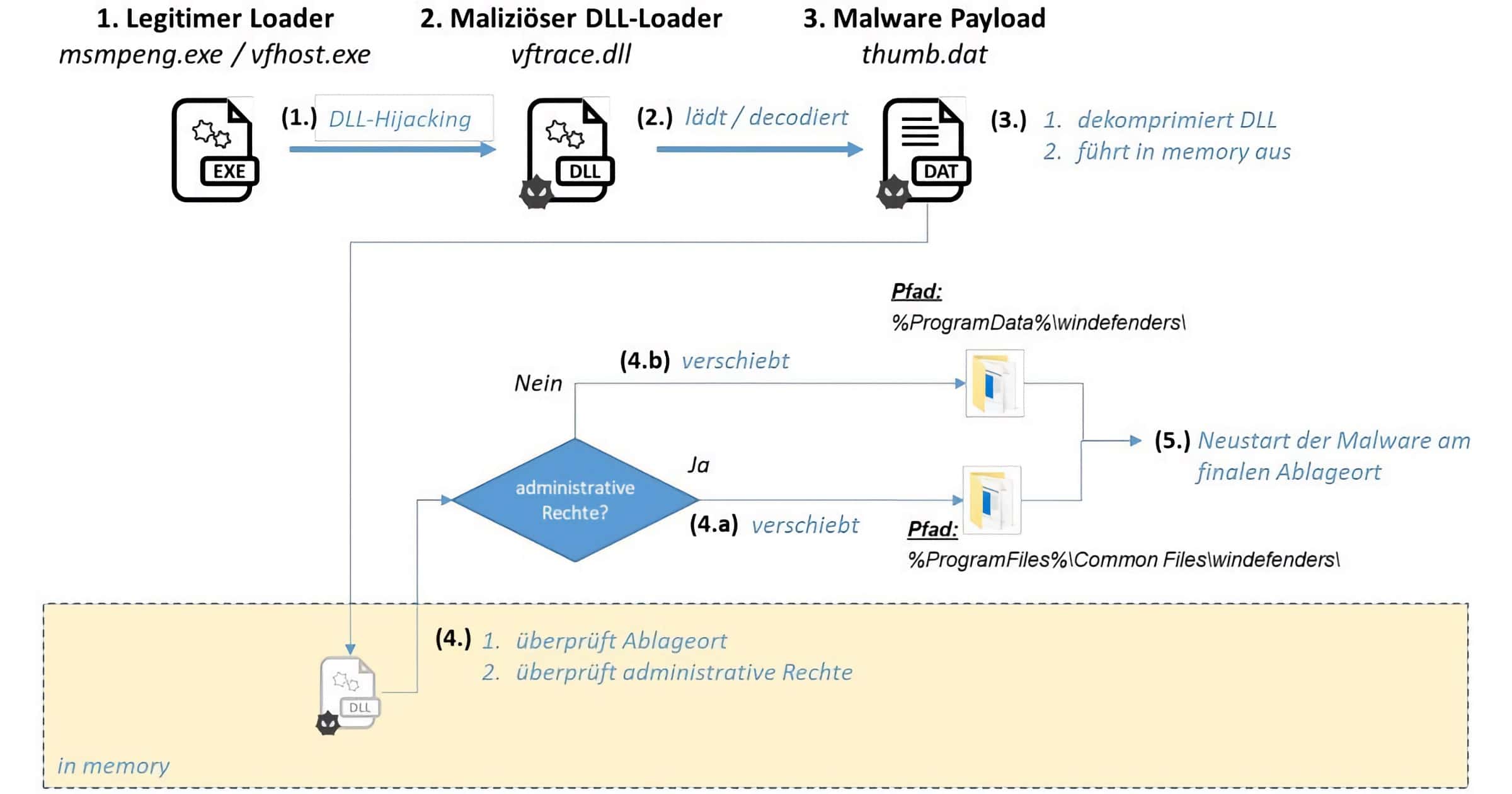
'UpdateAgent' Mac Trojan Can Steal Data and Inject Adware
UpdateAgent is the name of a Mac trojan that Microsoft has been tracking since October, although it first appeared in September 2020.
Intel Expands Bug Bounty Program With Project Circuit Breaker
Project Circuit Breaker is an expansion of Intel’s bug bounty program that hosts targeted time-boxed events on specific new platforms.
Here's How to Blur Your House on Apple Maps and Google Maps
Did you know you can blur your house on Apple Maps and Google Maps? This capability is open to everyone, here’s what you can do.
Civicom Data Leak Affects Over 100,000 Files
Video conference company Civicom has had a data leak, found by the Website Planet Security team. Over 100,000 files were included.
Treasury Considers ID.Me Alternatives Over Privacy Concerns
The Treasury Department is looking into ID.me alternatives for accessing the IRS website over privacy concerns.
CEO Blake Hall this week said that the company also used one-to-many technology, which compares selfies taken by users as part of the verification process against a larger database. The company said it maintained an internal database of selfies taken by users and compared new selfies against it using Amazon’s controversial Rekognition technology. As of January 25, 20.9 million users’ selfies had been verified against that database, the company said.
Microsoft Stopped an Insane 3.47 Tbps DDoS Attack
Microsoft’s Azure cloud division shared that it stopped a 3.47 Tbps DDoS attack, and two other attacks that were over 2.5 Tbps.
Security Friday: Not Entirely Bad News – TMO Daily Observations 2022-01-28
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and updates, including fixes and a tip for passwords on iOS.
'OSX.DazzleSpy' is a Fully-Featured macOS Implant for Espionage
OSX.DazzleSpy is a new macOS implant targeting Hong Kong pro-democracy websites. It affects the Safari browser on macOS.
Facebook Rolls Out End-to-End Encrypted Chats for Everyone
End-to-end encrypted chats are now available for all users of Facebook Messenger, the company announced. This includes group chats and calls.
Last year, we announced that we began testing end-to-end encryption for group chats, including voice and video calls. We’re excited to announce that this feature is available to everyone. Now you can choose to connect with your friends and family in a private and secure way.
These secure chats remain opt-in only, instead of encrypted by default like actual private messaging apps.
Researchers Create First Silk-Based Physical Unclonable Function
Researchers from the Gwangju Institute of Science and Technology in South Korea developed a silk-based physical unclonable function (PUF).
An NFT on OpenSea Can Steal Your IP Address
An NFT found on the OpenSea marketplace can steal visitors’ IP addresses, according to a repot from Motherboard.
Of course, websites often collect and store visitors’ IP addresses in virtue of how the sites function. OpenSea itself likely collects the IP addresses of visitors, like plenty of other sites, apps, or services. But here, an outside third party—the NFT seller—is able to gather information themselves on the people viewing the NFT, potentially without them knowing.
Successor to 'Shrootless' Bug Attacks Mac SIP Feature
Researchers at Perception Point write about CVE-2022-22583, a successor to Shrootless that could let attackers bypass Mac SIP.
MultiChain Hack Still Affecting Customers a Week Later
The Multichain hack is still affecting crypto users a week later, despite promises from the company that it had been contained.
China Hacking Group 'APT27' Attack German Companies
A China-based hacking group known as APT27 has been targeting German companies in areas such as technology and pharmaceuticals.
Apple Safety Guide: What You Need to Know About Device Access
An Apple safety guide has appeared to give customers information on how to protect themselves if their personal safety is at risk.
A Crypto Wallet Crack Recovered $2 Million in Tokens
The Verge had a fascinating story out yesterday about a crypto wallet crack that helped two friends get their tokens back. It’s a long-ish read but not overly technical.
Reich gave up and wrote off the money in his mind. He was willing to take the loss — until the price started to rise again. From a low of around $12,000, the value of their tokens started to skyrocket. By the end of 2020, it would be worth more than $400,000, rising briefly to over $3 million. It would be hard to get into the wallet without the PIN — but it wasn’t impossible. And with potentially millions on the line, Reich and his friend vowed to find a way inside.
'AccessPress' Themes and Plugins for WordPress Contains Backdoor
JetPack discovered a backdoor found within AccessPress themes and plugins. Every theme and most plugins contain this malware.
Merck Wins Court Dispute Over 'NotPetya' Attack
Merck wins a court dispute with insurance companies for US$1.4 billion in losses due to the NotPetya attack. This was a cyberattack in 2017.
Security Friday: This Week in (Sad) Data Breaches – TMO Daily Observations 2022-01-21
Andrew Orr joins host Kelly Guimont to discuss a Safari data leak, encrypted messaging, and as always, a new data breach.
Red Cross Data Breach Affects 515,000 Vulnerable People
A contractor for The International Committee of the Red Cross (ICRC) suffered a data breach, as revealed on Wednesday.
IRS and ID.me Makes Video Selfies a Requirement in 2022
The IRS is requiring people create an account with ID.me to access and submit taxes. One of the verification methods is a video selfie
NSO Targets: A List of People Infected With Pegasus Spyware
Omer Benjakob has put together a helpful list of NSO targets that includes every individual believed to have been infected with the group’s Pegasus spyware.
So far, targets have been found across the world: from India and Uganda to Mexico and the West Bank, with high-profile victims including U.S. officials and a New York Times journalist. Now, for the first time, Haaretz has assembled a list of confirmed cases involving Pegasus spyware.