Apple used narration from human readers to train its A.I. voices. The real readers did not know that, and weren’t too happy when they found out. TMO writer Nick deCourville joins Ken to talk that over. Plus – an update on the Google Photos breakage, and some security advice for Apple Card holders.
Security
Apple Shares Five Security Steps for Apple Card
Apple has provided more information to Apple Card users that explains several ways a user can further improve the security of their card.
Fixes, a Break, and Not Talking About the NBA - TMO Daily Observations 2023-02-14
Apple hit with many mini updates on Monday. TMO Managing Editor Jeff Butts joins Ken to talk a few points raised by those. Plus – Why it is way too early to talk about Apple going for streaming rights to the NBA.
What Does Security Lockout Mean on iPhone?
Learn what Security Lockout does on iPhone, and what to do if you’ve forgotten your passcode and the Security Lockout prompt appears.
Examining Security Keys with Duane Waddle - TMO Daily Observations 2023-01-24
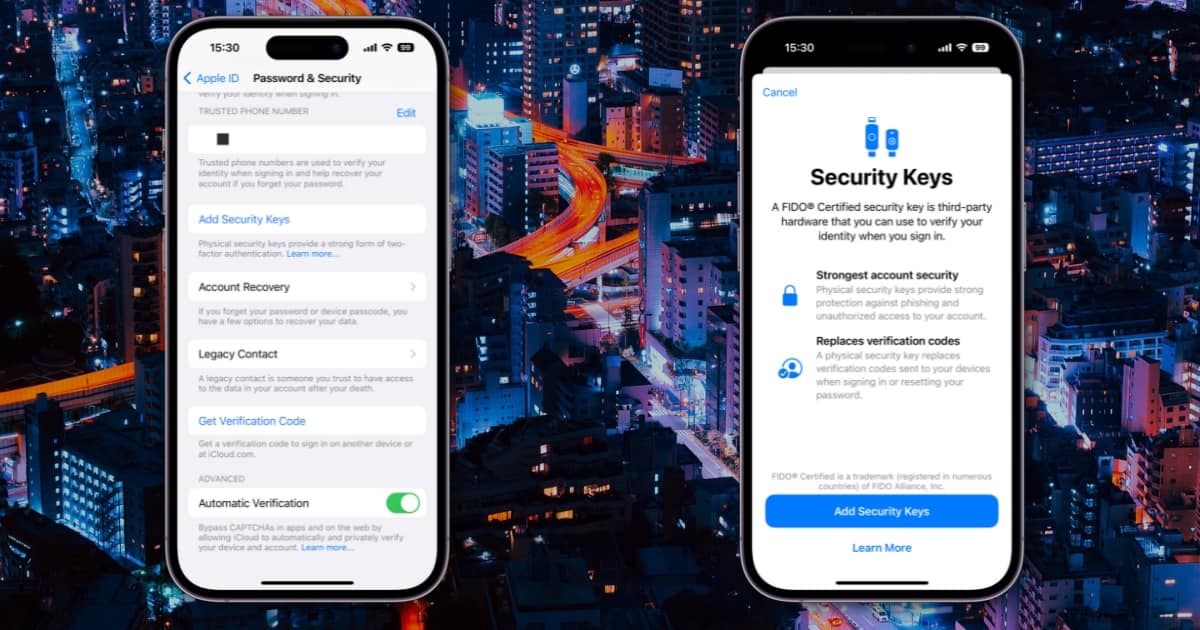
One of the biggest changes introduced in this week’s OS updates from Apple is the across the board option to use physical security keys for iPhone, iPad, and the Mac. Info-sec guy Duane Waddle joins Ken to talk about what they are, their implementation, and possible futures for the tech.
Physical Security Key Support Arrives in iOS 16.3, macOS Ventura 13.2 Beta
With the first beta versions of iOS 16.3, iPadOS 16.3 and macOS Ventura 13.2, Apple is introducing its new Security Key support for testing.
More End-to-End Encryption and Giving the Gift of Will Smith - TMO Daily Observations 2022-12-09
Dreamlight Valley resident and TMO Managing Editor Jeff Butts joins Ken today to discuss Apple’s Advanced Data Protection for iCloud. What is it, who needs it, and how does one activate it? Plus – Will Smith is promoting Apple TV+. Too soon?
How To Turn On Apple’s Advanced Data Protection for iCloud
Apple’s Advanced Data Protection for iCloud greatly improves your data security. Here’s how to turn the feature on.
Apple Announces Powerful New User and Data Security Features
Coming soon to an iPhone, iPad or Mac near you, Apple has announced three new user and data security features.
Eufy Doesn't Patch Potential Security Issue Affecting Its Video Doorbells, Instead Adds Disclaimer
Eufy is choosing not to fix a potential security issue with its camera products yet, but is offering more transparency into data storage.
Our Security and Smartphone Futures - TMO Daily Observations 2022-11-30
Mac Geek Gab co-host Dave Hamilton is really excited about Rapid Security Response coming in iOS 16.2. Ken is as well, though he seems argumentative about it anyway. Also – societal norms around smartphones are still being hammered out, in Dave’s estimation. He’ll drive a conversation about those.
Eufy Says Its Security Camera Footage Is Local-Only, But That’s Not Always True
A security researcher revealed that Eufy misleads customers, sending videos from its so-called local-only camera products to the cloud.
Apple Issues Rapid Security Response Update for iOS 16.2 Beta 3, But It’s Only a Test
Apple recently issued a Rapid Security Response to iOS 16.2 beta 3. However, it contains no security fixes, simply a test of the new feature.
Latest iOS 16.1 Update Patches Zero-Day Vulnerability
Apple acknowledged that iOS 16.1 and iPadOS 16.1 include a fix for a zero-day vulnerability that might have been actively exploited already.
Hospital Web Tracker Leak May Have Sent 3 Million Patients’ Info to Big Tech Companies
A hospital network’s web tracker leak may have transmitted personal details for millions of patients to Google, Meta and others.
Security Researcher Uncovers Yet Another iOS VPN Flaw
Hot on the heels of one recently-discussed iOS VPN flaw, a security researcher finds many Apple apps communicating outside the VPN tunnel.
New macOS Archive Utility Vulnerability Allows Malware to Bypass Gatekeeper Security, But An Update Patches the Hole
Thanks to a recently-published vulnerability in macOS Archive Utility, we see yet again the importance of regularly running Software Update.
Apple's Upcoming Lockdown Mode Feature May Also Pose Privacy Risk for iPhone Users
Apple’s Lockdown Mode coming in with iOS 16 can make iPhone users enabling the feature easy to fingerprint and identify.
Your iOS VPN Isn’t As Secure As You Think, Research Shows
Two years after a VPN provider advised Apple of a bug in iOS preventing the service from being secure, the problem still exists.
Apple Details Lockdown Mode With Groundbreaking Security Capability
Apple announced Lockdown Mode in its major operating systems, featuring groundbreaking security protection for users targeted by spyware.
Apple Launches Rapid Security Response, A New Feature for Applying Security Updates on the Fly
Apple has launched Rapid Security Response, a new feature that allows automatic application of security fixes to iOS and macOS.
Apple and Other Tech Giants Announce Commitment to a Future Without Passwords
A recent announcement boosts Apple’s commitment to a future without passwords. What this will actually do for security remains to be seen.
Bluetooth and Display Fixes Highlight macOS Monterey 12.3.1 Update
Thursday saw a number of important software updates from Apple. Among them, macOS Monterey 12.3.1 arrived to fix several issues.
Update to Google Chrome Browser Fixes High-Severity Issues
Google released a new version of its Chrome browser for macOS to address high-severity security issues that could be exploited by hackers.