Hackers have infiltrated a website belonging to the Principality of Sealand, using a web skimmer to steal user data such as payment information.
Security
Intel Stockpiles Legacy Hardware for Security Research at Costa Rica Facility
The Wall Street Journal reports that Intel has a facility in Costa Rica where it stores legacy hardware for security research.
Intel’s issue reflects a wider concern: Legacy technology can introduce cybersecurity weaknesses. Tech makers constantly improve their products to take advantage of speed and power increases, but customers don’t always upgrade at the same pace. This creates a long tail of old products that remain in widespread use, vulnerable to attacks.
Adele's Shuffle Challenge and Apple's Stand on State-Sponsored Spyware, with Jeff Gamet - ACM 562
Bryan Chaffin and Jeff Gamet talk about Adele’s desire that we not shuffle her albums. They also look at Apple’s public stand against state-sponsored spyware.
Security Tips for Holiday Visits – TMO Daily Observations 2021-11-24
Andrew Orr joins host Kelly Guimont to discuss security tips for traveling, and some good things to check when you get to your Turkey Day Destination.
Digital Marketing Agency 'Cronin' Leaks 92 Million Employee, Client Records
Security researcher Jeremiah Fowler in cooperation with the WebsitePlanet research team found an unprotected database from Cronin. It exposed 92 million database records from employees and clients.
The exposed server was named “Cronin-Main” and many of the records contained references to Cronin. These records included internal data such as employee and client information. Also included in the dataset was a “Master Mailing List” with direct physical names, addresses, Salesforce IDs, phone numbers, and references to where the leads came from.
Apple Sues NSO Group Over Endangering iOS Users With Spyware
On Tuesday Apple announced it had filed a lawsuit against NSO Group and its parent company. The goal is to hold it accountable for its spyware.
GoDaddy Breach Leaks 1.2 Million Email Addresses of WordPress Customers
On Monday, web hosting company GoDaddy revealed that it suffered a data breach that was discovered on September 6. It happened by way of a compromised password.
email addresses of up to 1.2 million active and inactive Managed WordPress customers had been exposed in an unauthorized third-party access.
Security Friday: Chip Flaws and Data Breaches – TMO Daily Observations 2021-11-19
Andrew Orr and host Kelly Guimont discuss the abundance of security news this week including some hardware issues and This Week in Data Breaches.
Rule Approved: Banks Must Report Cyber Attacks Within 36 Hours
U.S. regulators have approved a rule to require banks to report major cyber incidents within 36 hours.
The rule, dubbed the Computer-Security Incident Notification Requirements for Banking Organizations and Their Bank Service Providers, was cemented by the Office of the Comptroller of the Currency, Board of Governors of the Federal Reserve System and the Federal Deposit Insurance Corporation. There is currently no specific window that banks must repot such incident to the agencies in question.
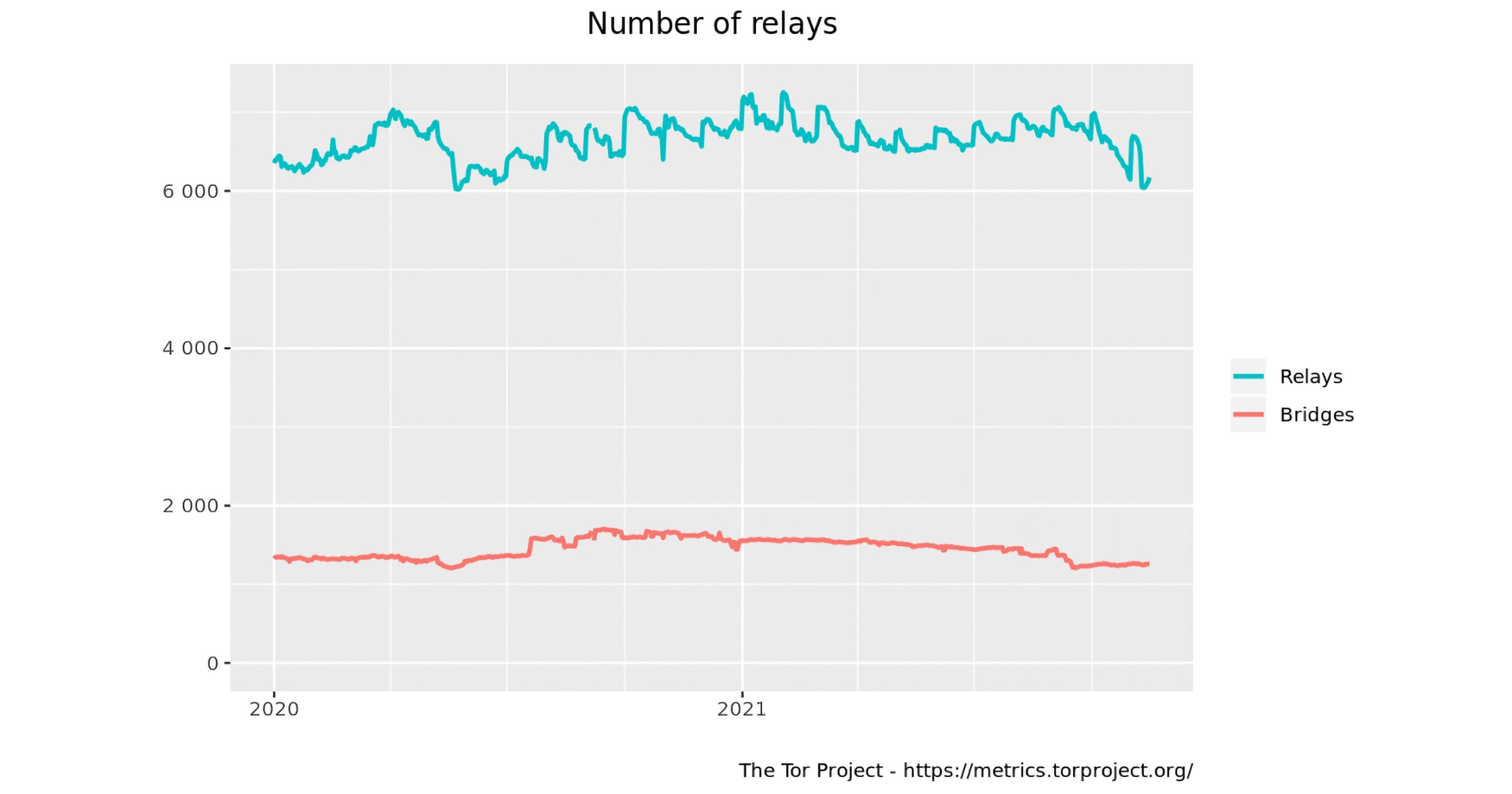
Tor Project Offers Rewards for More Servers During Decline
The Tor Project has seen a decline in relays and bridge servers, and offers rewards for people to help increase the network.
Rewards include the likes of hoodies, t-shirts, and stickers and are meant to provide some sort of meaningful gift to those who help keep the Tor anonymity network alive and resilient to censorship.
More specifically, the rewards will be provided to those who run Tor “bridges,” which serve as entry points into the Tor network for users located in countries that block access to Tor servers.
Data Breach of California Pizza Kitchen Leaks 100,000 Social Security Numbers
TechCrunch reports that California Pizza Kitchen suffered a data breach in September. The SSNs of over 100,000 employees were leaked as a result.
While CPK didn’t confirm how many people are impacted by the breach, a notification from the Maine attorney general’s office reported a total of 103,767 current and former employees — including eight Maine residents — are affected. CPK employed around 14,000 people as of 2017, suggesting the bulk of those affected are former employees.
Intel Chip Flaw Lets Attackers Install Malicious Firmware to Bypass Security
A flaw found within certain Intel chips lets an attacker with physical access to the install malicious firmware onto the system.
Teen in Canada Arrested Over $36.5 Million Crypto Theft
Bloomberg reports on a theft involving a Canadian teen stealing US$36.5 million in cryptocurrency from a victim in the U.S.
Police said the victim was targeted through a cell phone scam known as SIM swapping, in which a scammer hijacks a wireless customer’s phone number to intercept two-factor authentication requests and gain access to the victim’s accounts.
The arrest was the result of a joint investigation with the Federal Bureau of Investigation and the U.S. Secret Service Electronic Crimes Task Force, the Hamilton Police Service said in a statement. The investigation was launched last year in March.
If you haven’t already done so it’s a good idea to lock your SIM card with a PIN.
New 'CyberD TV' Aims to Train General Public in Cybersecurity
There’s a new streaming service in town and it’s called CyberD TV. It aims to help the public stay safe online with cybersecurity training.
US Issues Joint Advisory Warning Companies of Iranian Ransomware
In a joint advisory issued on Wednesday, the U.S. is warning that Iranian state-backed hackers are targeting infrastructure companies with ransomware.
The Iranian government-sponsored APT actors are actively targeting a broad range of victims across multiple U.S. critical infrastructure sectors, including the Transportation Sector and the Healthcare and Public Health Sector, as well as Australian organizations. FBI, CISA, ACSC, and NCSC assess the actors are focused on exploiting known vulnerabilities rather than targeting specific sectors.
GitHub Fixes NPM Bugs That Leaked Private Package Names
GitHub has fixed several flaws with npm packages that leaked private names and let attackers publish new versions of a package they didn’t have rights to.
The data leak was identified by GitHub on October 26th and by the 29th, all records containing private package names were deleted from the npm’s replication database. Although, GitHub does warn that despite this, the replicate.npmjs.com service is consumed by third parties who may, therefore, continue to retain a copy or “may have replicated the data elsewhere.”
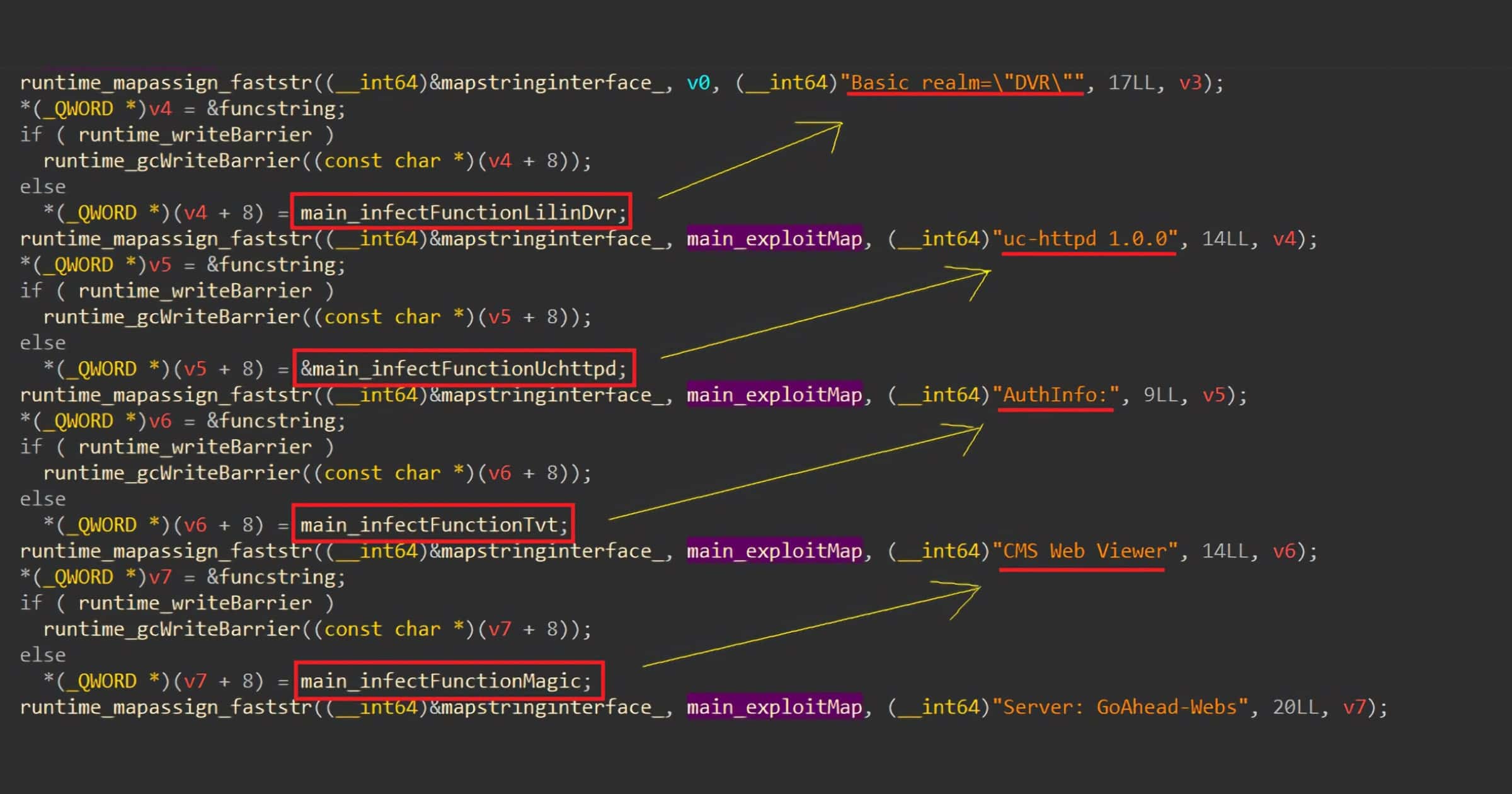
New 'BotenaGo' Targets Routers and Smart Home Devices in Devastating Attack
AT&T Alien Labs discovered malware it dubs BotenaGo. It affects millions of routers and Internet of Things devices found with smart homes. The “devastating” part comes from the fact that it uses over 30 separate exploits due to insecure devices.
The BotenaGo malware starts by initializing global infection counters that will be printed to the screen, informing the hacker about total successful infections. It then looks for the ‘dlrs’ folder in which to load shell scripts files. A loaded script will be concatenated as ‘echo -ne %s >> ‘. If the ‘dlrs’ folder is missing, the malware will stop and exit at this point. For the last and most important preparation, the malware calls the function ‘scannerInitExploits’, which initiates the malware attack surface by mapping all offensive functions with its relevant string that represent the targeted system.
Researchers Uncover Serious Flaws Within DRAM Chips
ETH Zurich reports that researchers from the Vrije Universiteit Amsterdam and Qualcomm Technologies found flaws within DRAM chips. The article I’m linking to is more of an announcement; ETH Zurich tells me the full results will be presented at IEEE in 2022.
It means that by repeatedly activating – or “hammering” – a memory row (the “aggressor”), an attacker can induce bit errors in a neighbouring row, also called the “victim” row. That bit error can then, in principle, be exploited to gain access to restricted areas inside the computer system – without relying on any software vulnerability.
FBI Says Data Was Not Compromised After Hackers Took Over Email Server
Hackers took over an FBI server over the weekend, sending thousands of fake cyberattack warnings. The agency says no personal information or data was affected.
The agency said it has fixed the software vulnerability that allowed the attack.
The fake emails originated from an FBI-operated server, which was dedicated to pushing notifications to the Law Enforcement Enterprise Portal (LEEP), which the FBI uses to communicate with state and local agencies. The compromised server was not part of the FBI’s corporate email service, the FBI added.
Security Friday: News and Precise Locations – TMO Daily Observations 2021-11-12
Andrew Orr and Jeff Butts join host Kelly Guimont to discuss security news, This Week in Data Breaches, and new uses for Precise Location data.
Newly Discovered 'OSX.CDDS' Implant Targets Visitors to Hong Kong Websites
Google’s Threat Analysis Group discovered a new macOS implant that security researcher Patrick Wardle dubbed OSX.CDDS. It targets “visitors to Hong Kong websites for a media outlet and a prominent pro-democracy labor and political group.”
Notable features for this backdoor include: victim device fingerprinting, screen capture, file download/upload, executing terminal commands, audio recording, keylogging.
How Thieves are Stealing Apple ID Credentials for Stolen iPhones
A report from India Today shares the story of how thieves tricked an Apple user to steal his credentials in order to unlock the iPhone they stole.
Vedant narrated his ordeal on Twitter and urged users to be aware of the types of attacks that can be used to extract sensitive information from users. He revealed that the first thing he did after losing his phone was log in to the Find My app with his Apple ID using his MacBook and try to get the phone’s exact location through the Find My app.
Classic phishing attack.
Robinhood Data Breach Leaked Email Addresses From Social Engineering
Robinhood suffered a data breach recently through a social engineering attack on a customer support agent.
At this time, we understand that the unauthorized party obtained a list of email addresses for approximately five million people, and full names for a different group of approximately two million people.
A Drone Tried to Attack a Pennsylvania Power Station in 2020
Wired published a fascinating story of a unknown person who used a drone to attempt to short circuit a power substation last year.
The operator of the Pennsylvania drone appears to have attempted a less brute-force approach. But efforts to hide the operator’s identity may have contributed to their failure to connect with the intended target. By removing the camera, the joint bulletin says, they had to rely on line-of-sight navigation, rather than being able to take a drone’s eye view.