Along with bug fixes, iOS 15.0.2 released on Monday patches a zero-day exploit that Apple believes may have been actively used.
Security
Secure Your Stuff Friday: Twitch and Licenses – TMO Daily Observations 2021-10-08
Andrew Orr and Kelly Guimont talk about the latest Security Friday headlines including Twitch and a new standard for ID on phones.
ISO Approves and Publishes Standard for Mobile Driver's License
The International Organization for Standardization has approved and published ISO/IEC 18013-5 for mobile driver’s licenses and mobile IDs.
Anonymous Hacker Shares Twitch Source Code and Payout Data
An anonymous hacker shares data claimed to be Twitch source code. That’s right, not just Twitch data but Twitch itself, its source code and user payout data.
The user posted a 125GB torrent link to 4chan on Wednesday, stating that the leak was intended to “foster more disruption and competition in the online video streaming space” because “their community is a disgusting toxic cesspool”.
VGC can verify that the files mentioned on 4chan are publicly available to download as described by the anonymous hacker.
I have to chuckle about the part where they go on 4chan to complain about toxic websites. Update: Twitch has confirmed the incident.
Proposed Bill Would Require Disclosures of Ransomware Payments
Under the Ransom Disclosure Act, victims of ransomware who pay their attackers would have to report the payment within 48 hours.
Researcher Discloses Telegram Bug After Disappointing Response From Company
A security researcher has shared a bug with Telegram’s auto-delete feature. But the company has seemingly ignored him.
The researcher contacted Telegram in early March. And after a series of emails and text correspondence between the researcher and Telegram spanning months, the company reached out to Dmitrii in September, finally confirming the existence of the bug and collaborating with the researcher during beta testing.
Since then, the researcher claims he has been ghosted by Telegram, which has given no response and no reward.
SMS Routing Company 'Syniverse' Admits it was Hacked in 2016
Syniverse provides backbone services to wireless carriers like AT&T, Verizon, T-Mobile, and several other carriers. It discovered the breach in May 2021 but it began in May of 2016.
Syniverse repeatedly declined to answer specific questions from Motherboard about the scale of the breach and what specific data was affected, but according to a person who works at a telephone carrier, whoever hacked Syniverse could have had access to metadata such as length and cost, caller and receiver’s numbers, the location of the parties in the call, as well as the content of SMS text messages.
Security Friday: Privacy Not Included – TMO Daily Observations 2021-10-01
Andrew Orr joins host Kelly Guimont to discuss Security Friday news including Mozilla’s product guide and an AirTag attack.
Researchers Hack Apple Pay to Steal Money With Visa
Apple claims that the problem lies with Visa’s network, while Visa says the payments are secure and “attacks of this type were impractical outside of a lab.”
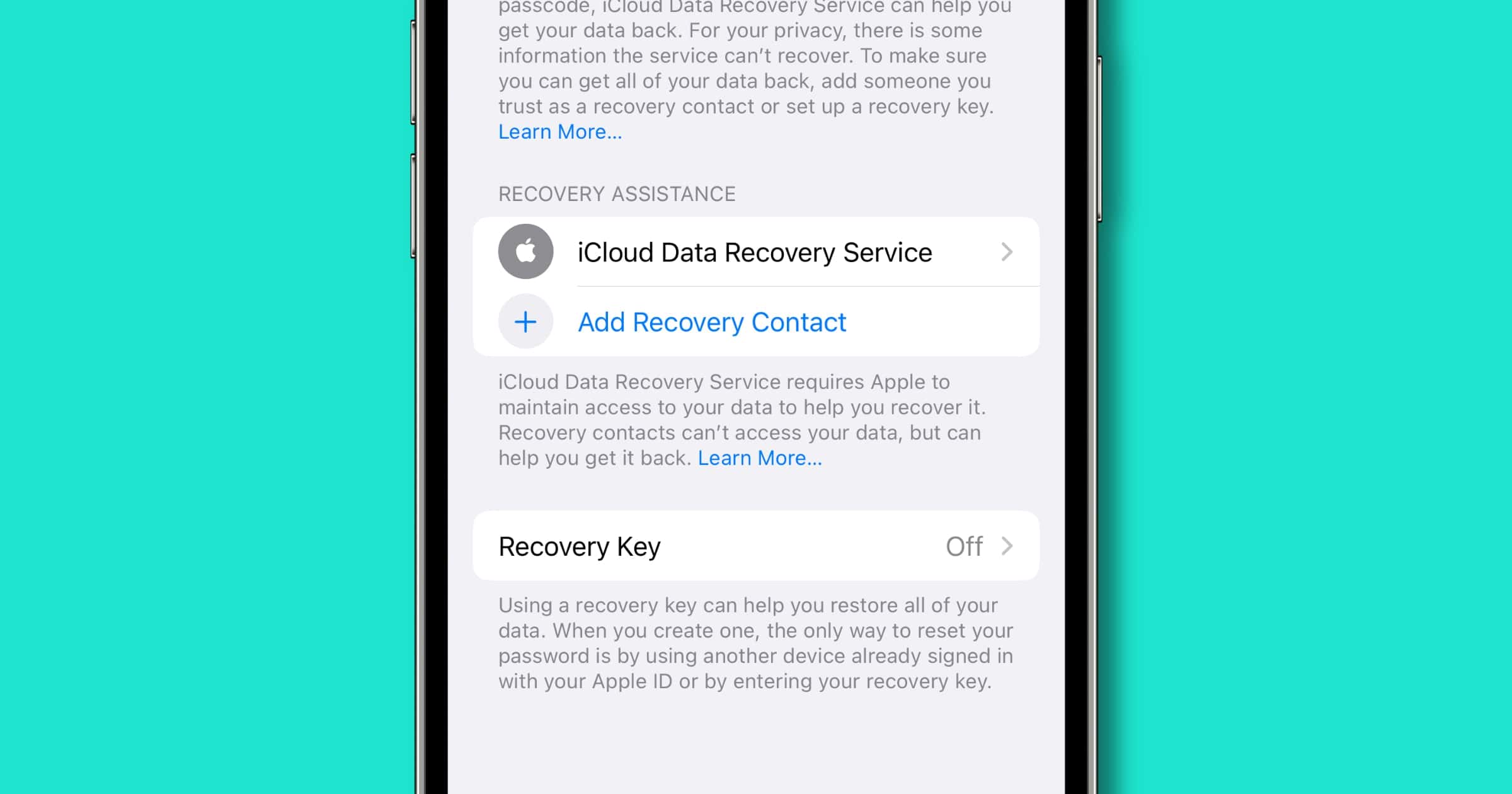
iOS 15: Here's How to Set Up an iCloud Data Recovery Contact
In recent versions of its operating systems, Apple has added a way to set up an iCloud Data Recovery contact.
Twitch Adds Verification Tool as a Way to Fight Bots
Starting today, Twitch will let streamers require their viewers to verify their phone number via SMS before they can start chatting.
Twitch’s approach so far has been to offer streamers more control over who can and can’t chat. Streamers already have the option to make their chats subscriber-only, or slow down their chat so moderators can approve messages. There’s also the option to force all chatters to verify their email on Twitch. That hasn’t been enough, though.
'FinSpy' Spyware is Adept at Hiding Itself With a Four-Layer Method
FinSpy, a well-known piece of spyware from German company FinFisher, is good at hiding. Researchers at Kaspersky have reverse-engineered the malware.
In addition to a four-layer obfuscation method, the spyware also now employs a UEFI (Unified Extensible Firmware Interface) bootkit for infecting its targets, and it also encrypts the malware in memory, according to the researchers. The Kaspersky team’s research began in 2019, and they are finally sharing their findings today at Kaspersky’s online Security Analyst Summit.
AirTag Zero Day Found That Could Steal Your iCloud Password
A security researcher found a zero-day bug with AirTag that could let an attacker potentially steal your Apple ID.
Apple’s “Lost Mode” allows a user to mark their Airtag as missing if they have misplaced it. This generates a unique https://found.apple.com page, which contains the Airtag’s serial number, and the phone number and personal message of the Airtag owner.
Backblaze Announces Disaster Recovery Solution for Backups
Backblaze has announced “Backblaze Instant Recovery in Any Cloud” on Tuesday. It’s aimed at ransomware attacks so affected companies can recover faster.
1Password Adds Email Aliases Powered by Fastmail Called 'Masked Email'
1Password has teamed up with Fastmail to give users a way to create email aliases when signing up for accounts.
Security Friday: Bad, Real Bad, and Good News – TMO Daily Observations 2021-09-23
Andrew Orr joins host Kelly Guimont for a round of Security Friday news, including ransomware, hacking, and a way to protect your Apple Card.
Inside Story: How the Mafia is Getting Involved in Cybercrime
On Monday, police in Europe announced the arrests of over 100 people connected to the Mafia. They were using hackers to support efforts in traditional crime.
The authorities said that the organized crime groups employed hackers who were using phishing, social engineering attacks, and SIM swapping, as well as sending malware to victims with the goal of taking over their bank accounts and stealing their money.
This operation highlights a new trend: traditional organized crime groups, such as the Italian Mafia and Camorra, are now dabbling in cybercrime to support their traditional offline activities, according to Italian and Spanish police investigators involved in the crackdown who spoke with Motherboard.
macOS Finder Bug Lets Certain Files Run Arbitrary Commands
Researcher Park Minchan reported a bug within macOS Finder that lets certain files execute commands. It affects all versions of macOS up to Big Sur.
A vulnerability in the way macOS processes inetloc files causes it to run commands embedded inside, the commands it runs can be local to the macOS allowing the execution of arbitrary commands by the user without any warning / prompts.
Originally, inetloc files are shortcuts to an Internet location, such as an RSS feed or a telnet location; and contain the server address and possibly a username and password for SSH and telnet connections; can be created by typing a URL in a text editor and dragging the text to the Desktop.
70% of People use the Same Password for Multiple Websites
A report of a survey (n=1,041) reveals that 70% of respondents said they reuse the same password for multiple websites.
The numbers above from our recent survey of 1,041 adults age 18 or older in the US say it all. A full 70% of the respondents admitted they use the same password for more than one thing—sometimes (25%), most of the time (24%), or all of the time (21%). If you don’t know why that’s bad, read on: When someone gets your password for just one service, they have your password for everything. Since most online accounts assign your email address as a username, it doesn’t take Mr. Robot to crack that code.
One of our recurring tips for Security Friday is to use a password manager. This helps you easily create unique, secure passwords for anything.
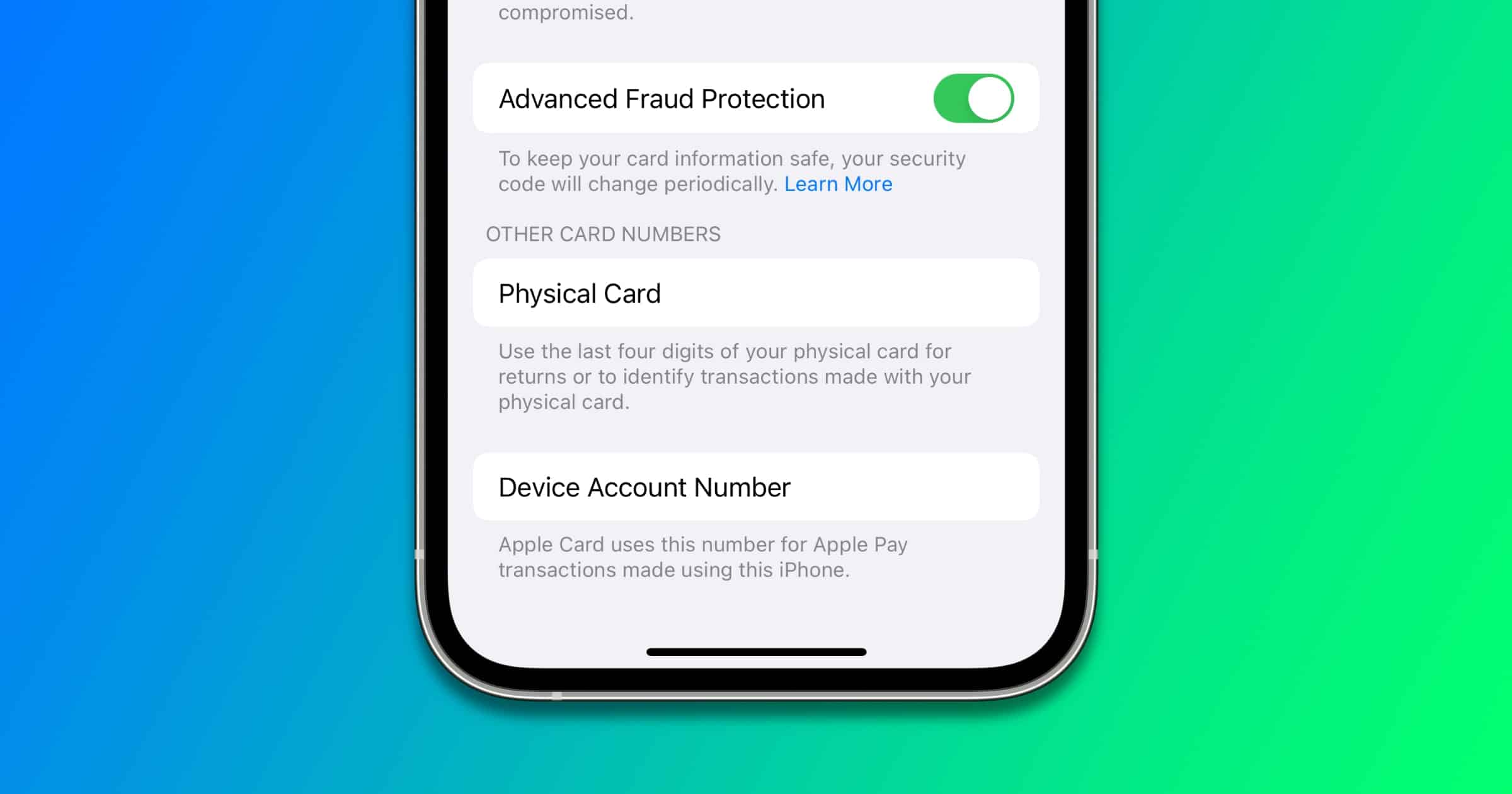
New Apple Card Security Feature Lets You Change Your CVV
Apple is enabling an Advanced Fraud Protection feature for Apple Card customers. It lets you regularly change your CVV.
Alaska Health Service Attacked by Nation-State Cyber Attacker
The Department of Health and Social Service (DHSS) disclosed that it was the victim of a sophisticated cyberattack from a nation-state level actor.
Citing an investigation conducted together with security firm Mandiant, DHSS officials said the attackers gained access to the department’s internal network through a vulnerability in one of its websites and “spread from there.”
Officials said they believe to have expelled the attacker from their network; however, there is still an investigation taking place into what the attackers might have accessed.
Grain Cooperative 'New Cooperative Inc' Hit with BlackMatter Ransomware Attack
Cyber gang BlackMatter has attacked Iowa-based grain cooperative New Cooperative Inc with ransomware, successfully shutting down its systems.
The attack occurred on or around Friday, according to Allan Liska, senior threat analyst at the cybersecurity firm Recorded Future Inc. The ransomware gang, which goes by the name BlackMatter, is demanding a $5.9 million ransom, Liska said.
New Cooperative confirmed that they had been attacked and said they had contacted law enforcement and were working with data security experts to investigate and remediate the situation.
Security Friday: Phishin and Strippin – TMO Daily Observations 2021-09-17
Andrew Orr and Kelly Guimont discuss Security Friday news and updates, including new phishing scams and sketchy wifi networks.
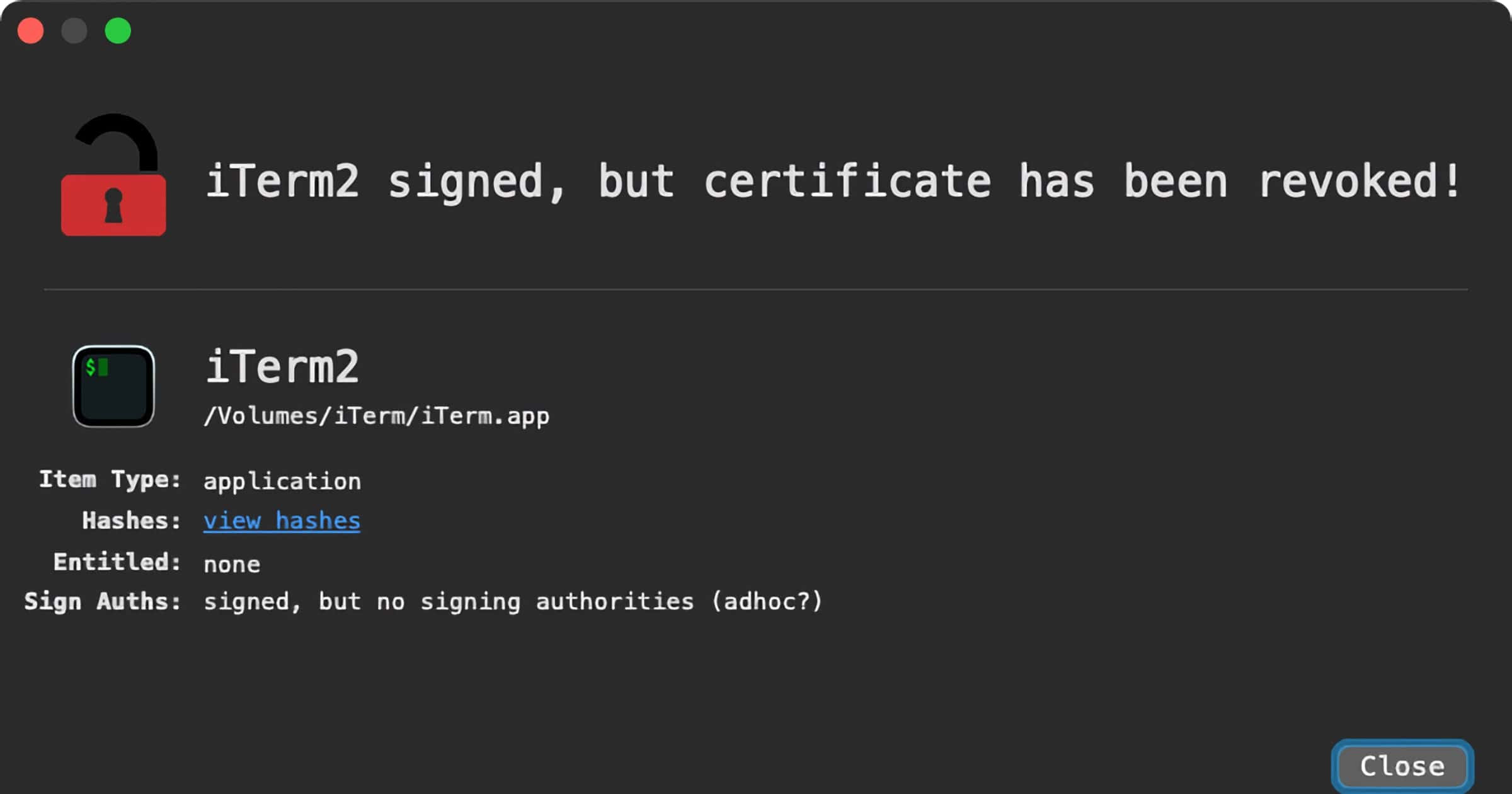
'OSX.ZuRu' Malware Spreads From Trojanized Apps via Sponsored Search Results
The latest Mac malware to be discovered is called OSX.ZuRu. It spreads via infected apps from sponsored search results.
The legitimate and the malicious iTerm2 application bundles contain a massive number of files, including several Mach-O binaries. Moreover, the malicious version appears largely benign (as is the case with most applications that have been surreptitiously trojanized). As such, it takes us a minute to uncover the malicious component.