Andrew Orr joins host Kelly Guimont to discuss some good Security Friday news, an update on previous news, and a gift idea for everyone.
Security
Money Laundering Through Twitch Nets Hackers $10 Million
A report on Thursday claims that hackers were able to launder US$10 million on Twitch through the platform’s Bits currency.
Fake Job Ads, ID Stealing Quizzes – TMO Daily Observations 2021-11-03
Jeff Butts and Andrew Orr join host Kelly Guimont to discuss quizzes and job ads that are definitely too good to be true.
Phlebotomy Training Specialists Exposes Student Data in Breach
Led by Noam Rotem and Ran Locar, vpnMentor’s research team discovered a data breach from Phlebotomy Training Specialists.
Unfortunately, the company was storing the complete records of 10,000s of students nationwide on a single, open cloud account. In this case, Phlebotomy Training Specialists was using an Amazon Web Services (AWS) S3 bucket to store data it collected from students, staff members, and people applying to its courses. S3 buckets are an increasingly popular enterprise cloud storage solution. However, users must set up their security protocols manually to protect the data stored therein.
Cybersecurity Agency CISA Gives Federal Agencies 6 Months to Patch Security Flaws
The Cybersecurity and Infrastructure Security Agency will require all federal agencies to patch security flaws in their systems.
Beware of Fake Job Ads That Can Steal Your Identity
Fake job ads are on the rise, a report says on Tuesday. Scammers use peoples’ Social Security Numbers to sign up for unemployment benefits.
That means scammers may need help from their victims — and sometimes they go to elaborate lengths to mislead them. Some fraudsters recreate companies’ hiring websites. One fake job application site uses Spirit Airlines’ photos, text, font and color code. The phony site asks applicants to upload a copy of both sides of their driver’s license at the outset of the process and sends them an email seeking more information from a web address that resembles Spirit’s, with an extra “i” (spiiritairline.com).
'Shrootless' macOS Bug Could Bypass System Integrity Protection
Microsoft reported a macOS vulnerability it calls Shrootless. It could let an attacker bypass SIP and perform arbitrary operations on the device. It has been patched by Apple with the most recent Mac updates this week.
We found that the vulnerability lies in how Apple-signed packages with post-install scripts are installed. A malicious actor could create a specially crafted file that would hijack the installation process. After bypassing SIP’s restrictions, the attacker could then install a malicious kernel driver (rootkit), overwrite system files, or install persistent, undetectable malware, among others.
Security Friday: Bug Bounties, Updates, and Tools for "Good Guys" – TMO Daily Observations 2021-10-29
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and updates including who can get into your phone now, and a massive bug bounty.
Kandji Announces 'Passport' for Secure Mac Authentication
Kandji has announced the release of Passport, an authentication product that creates a seamless, one-password sign-in experience for users.
Kandji Passport validates the credentials a user provides during Mac login against an organization’s cloud-based identity provider (IdP), so users need to remember just one password for both their Mac computers and the organization’s single sign-on (SSO) provider. Passport provides a native Mac login experience while streamlining device configuration, management, and security tasks for IT admins.
(Update) Medical AI Company 'Deep6' Leaks 68 GB Trove of Patient Records
Security researcher Jeremiah Fowler together with the WebsitePlanet research team found an unprotected database belonging to Deep6. The records appear to contain data of those based in the United States.
Update: Deep6 reached out and said the news is misleading, saying “In August, a security researcher accessed a test environment that contained dummy data from MIT’s Medical Information Mart of Intensive Care (MIMIC) system, an industry standard source for de-identified health-related test data. To confirm, no real patient data or records were included in this ephemeral test environment, and it was completely isolated from our production systems.”
Meanwhile, according to WebsitePlanet, Mr. Fowler said, “I sent 3 follow up emails on Aug 11, Aug 12, Aug 23. No one has ever replied since the first message on Aug 10th. I validated that the doctor’s names were real individuals by searching obscure names (see screenshot). This is highly unusual in my experience to use real individuals’ data in a ‘dummy environment’ under any circumstances. Because no one replied, we added our disclaimer that we are highlighting that no patient data appeared in plain text, the records were “medical related”, and we never implied any wrongdoing or risk.”
Dental Data Breach Affects 125,000 Patients in 10 States
North American Dental Management suffered a data breach between March 31 and April 1, 2021. It happened as the result of phishing. This group provides administrative and technical support services for Professional Dental Alliance (PDA) offices.
PDA said that it had not found any evidence of any actual misuse of personal information and that its investigation of the matter indicates that the attack was limited to email credential harvesting.
The threat actor did not access PDA’s patient electronic dental record or dental images; however, the Alliance found that some sensitive personal information may have been present in the compromised email accounts.
The breach was reported to the DHS’s Office for Civil Rights, impacting 125,760 patients in Connecticut, Florida, Georgia, Illinois, Indiana, Massachusetts, Michigan, New York, Texas and Tennessee.
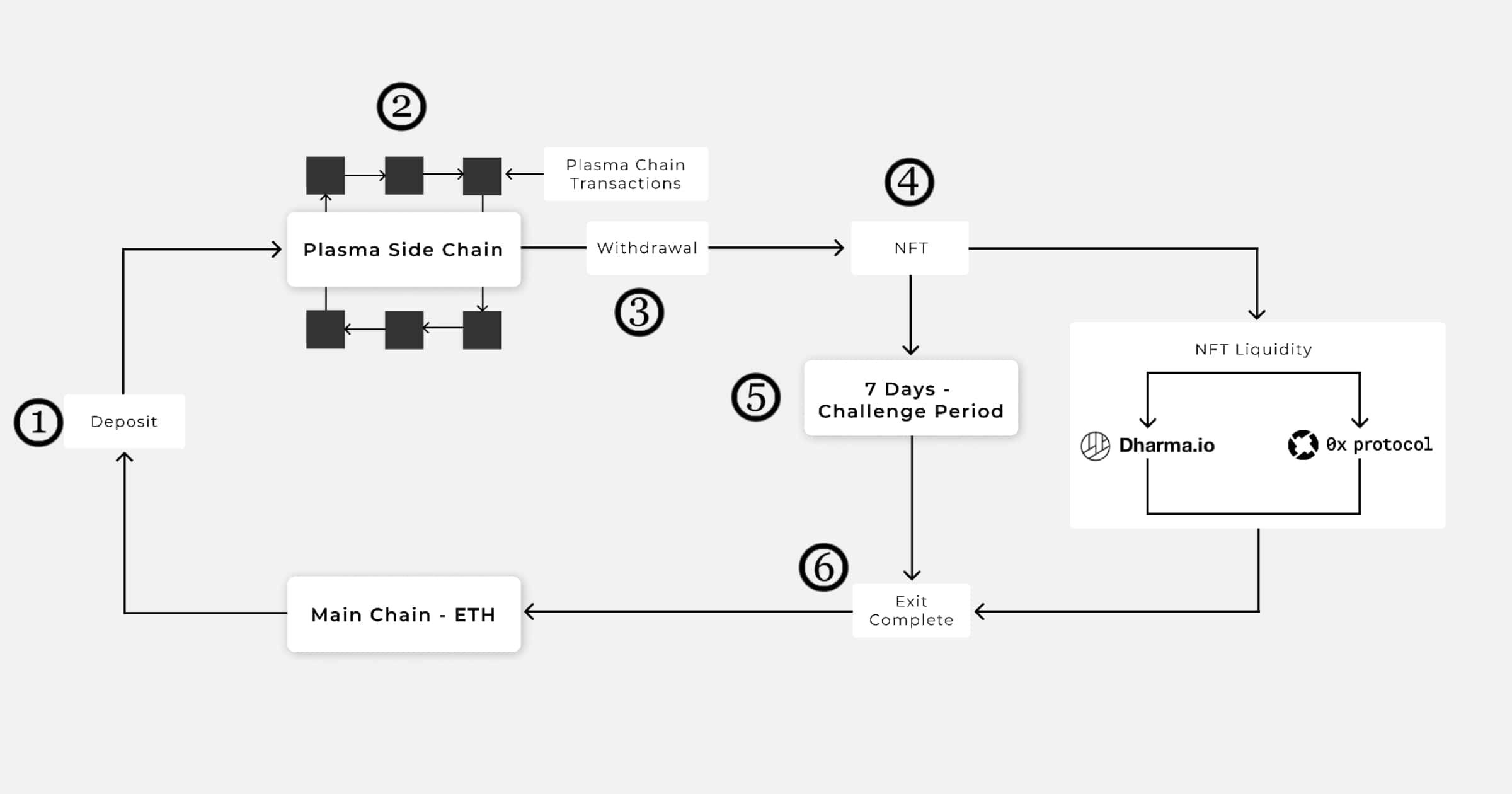
Polygon Blockchain Fixes Double Spend Bug Reported From Bug Bounty
Security researcher Gerhard Wagner found a double-spend bug in Polygon’s Plasma bridge. The company awarded Mr. Wagner a record US$2 million for reporting this critical vulnerability.
In total, it is possible to create 14×16 = 224 different encodings for the same raw path. A malicious user can leverage the issue to create alternative exits for the same burn transaction and perform double spends on the Polygon network.
Elcomsoft Can Now Download iCloud Data With Trusted Device Authentication
Elcomsoft has announced an update to its Phone Breaker, a forensic tool used to extract data from iPhones. A trusted iOS device can now be used to authenticate into iCloud. This will let the tool decrypt data protected by end-to-end encryption.
By using a trusted device, experts benefit from unrestricted access to all kinds of information stored in the user’s iCloud account including cloud backups produced by all Apple devices sharing the same Apple ID, photos, synchronized data, as well as end-to-end encrypted data such as the user’s passwords, browsing history, and health information.
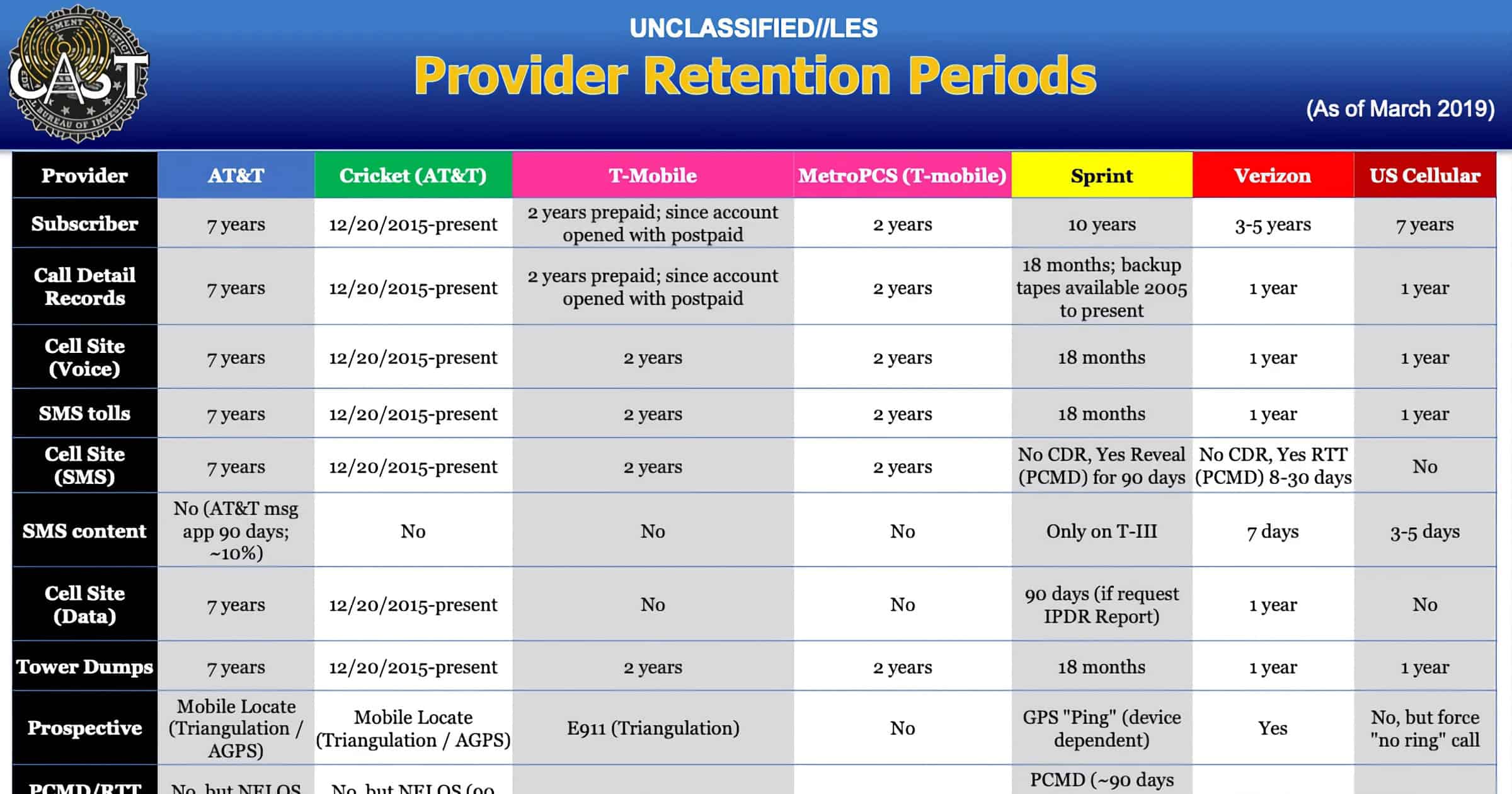
FBI Document Reveals Guide to Get Location Data From Carriers
An internal document for the FBI reveals how the agency obtains phone location data from carriers like AT&T, Verizon, and others.
Security Friday: News and Apple Watch Tips – TMO Daily Observations 2021-10-22
Andrew Orr joins host Kelly Guimont to discuss Security Friday news and updates on ransomware and hacking, and share how your Watch can make you safer.
'REvil' Ransomware Group Taken Down Through Multi-Country Effort
The FBI, working with Cyber Command, the Secret Service, and other countries, took down REvil.
According to three people familiar with the matter, law enforcement and intelligence cyber specialists were able to hack REvil’s computer network infrastructure, obtaining control of at least some of their servers. After websites that the hacker group used to conduct business went offline in July, the main spokesman for the group, who calls himself “Unknown,” vanished from the internet.
US Bans Export of Hacking Tools to Authoritarian Regimes
The Commerce Department’s Bureau of Industry and Security (BIS) announced new rules for hacking tools and their export to other countries.
Ransomware Attack on Sinclair Broadcasting Linked to Russian Group 'Evil Corp'
Last weekend, Sinclair Broadcast Group found itself the victim of a ransomware attack, and sources claim Russian group Evil Corp. was behind it.
Missouri Governor Pursues Journalist Who Read Website Code
Missouri Governor Mike Parson wants to prosecute a journalist who discovered the government’s website was leaking Social Security Numbers.
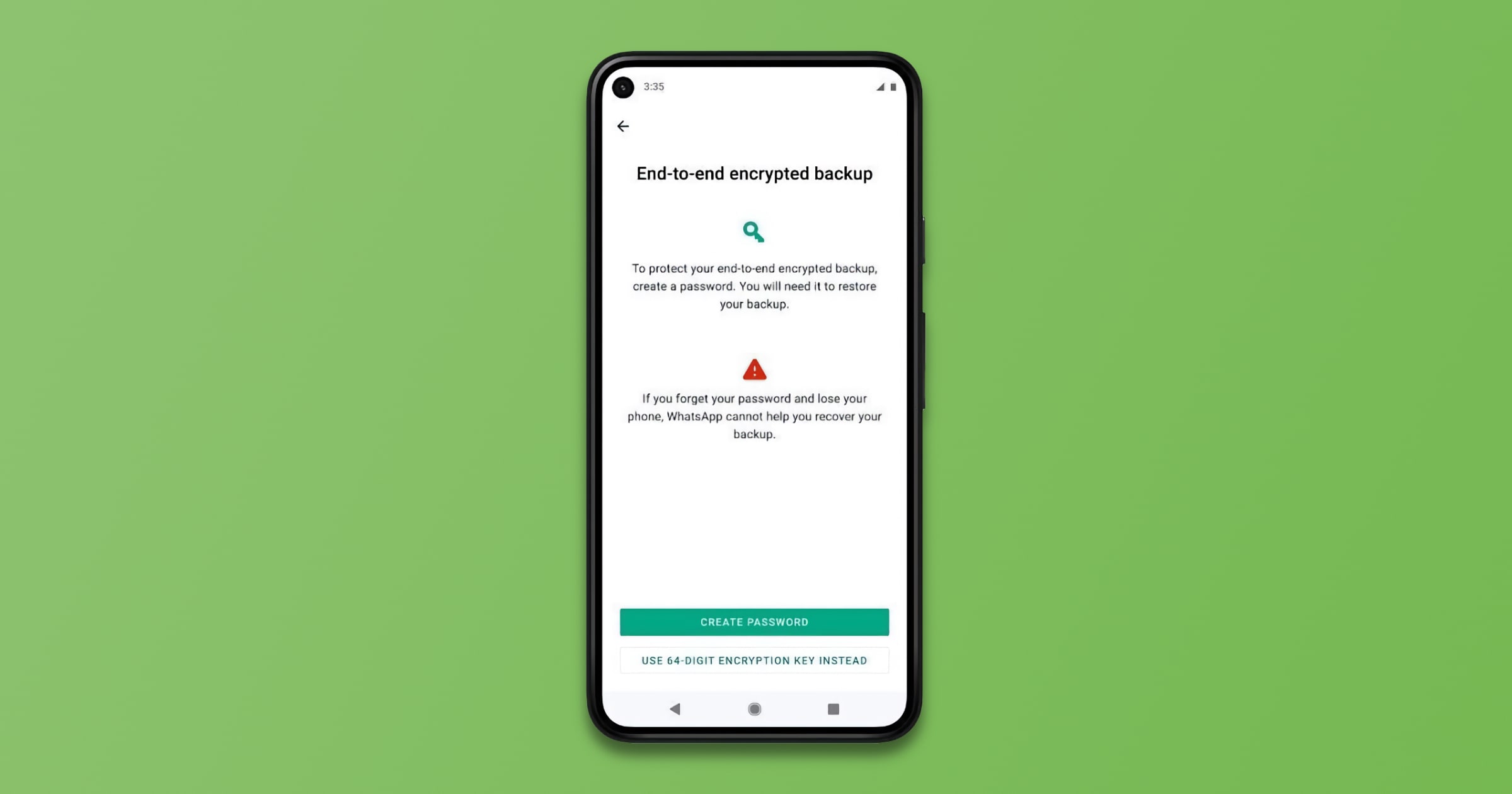
WhatsApp Rolls Out Support for End-To-End Encrypted Backups
WhatsApp is rolling out support for end-to-end encrypted backups for Google Drive and iCloud. Here’s how to enable the feature.
Make sure you’ve got the latest version of WhatsApp.
Open Settings.
Tap Chats > Chat Backup > End-to-end Encrypted Backup.
Click Continue, then follow the prompts to create your password or 64-digit encryption key.
Hit Done, and wait for your end-to-end encrypted backup to be prepared. You may need to connect to a power source.
NFT Marketplace 'OpenSea' Has Serious Security Flaws
OpenSea, one of the biggest marketplaces for NFTs, has security flaws that leave user wallets open to attack.
The researchers stated that the vulnerability allowed hackers to steal users’ entire crypto wallets. As said, OpenSea has been the biggest marketplace for buying, selling, and trading NFTs and other digital collectibles.
CheckPoint came across the vulnerability for the first time following reports of stolen crypto wallets triggered by airdropped NFTs. The Check Point researchers later discovered critical security issues “that, if exploited, could have led hackers to hijack user accounts and steal entire crypto wallets of users, by sending malicious NFTs”.
W3C, Yubico Offer Web Authentication Course for Developers
Yubico, along with the World Wide Web Consortium (W3C) are partnering to create an Introduction to Web Authentication course for developers.
Customer Accounts of 'Visible' Phone Carrier Hacked, Unauthorized Purchases Made
Visible, a carrier owned by Verizon, suffered what some believed was a data breach on Wednesday, with some customer accounts hacked.