So far, Andrew found two websites that don’t let you hide your email using Sign In with Apple. And this doesn’t appear to be against guidelines.
privacy
Facebook Bought Giphy. What Does That Mean for Privacy?
Facebook announced today that it’s acquiring Giphy for an alleged sum of US$400 million.
Facebook characterized the acquisition—reportedly worth $400 million—as a way to help its millions of users “better express themselves.” […] Facebook says it will not collect information specific to individual people using Giphy’s API, but it will get valuable data about usage patterns across the web.
I definitely don’t believe them when they say that won’t collect individual data. That is Facebook’s raison d’être. This is exactly like its usage of the Onavo VPN spyware: Collect data on how people use GIFs everywhere, especially on competitor’s platforms. Mark Zuckerberg is furiously trying to beat Snapchat into submission. They rejected him once and he’s been out for blood ever since. GIFs may sound like a stretch when it comes to data collection, but keep in mind that web beacons exist.
Senate Vote Lets FBI View Your Browsing History Without Warrant
As part of a reauthorization of the Patriot Act, the Senate voted to let the FBI access Americans’ web browsing history without a warrant. I could say a lot of bad things about this, but this is the part that disappoints me the most:
Sens. Ron Wyden (D-OR) and Steve Daines (R-MT) attempted to remove the expanded powers from the bill with a bipartisan amendment.
But in a shock upset, the privacy-preserving amendment fell short by a single vote after several senators who would have voted “Yes” failed to show up to the session, including Bernie Sanders. 9 Democratic senators also voted “No,” causing the amendment to fall short of the 60-vote threshold it needed to pass.
Just one vote.
Your Financial Transaction Data is the Holy Grail for Advertisers
Over the past decade, our financial transaction data has become one of the most sought-after data sets. Credit card processors like American Express, Mastercard, and Visa are at the center of it.
All of this is happening under a veil of secrecy. Credit card companies may acknowledge that they make money from analyzing transactions, but they are vague about what data they actually share […] Even Apple, which prohibits Goldman Sachs from using its card data for marketing purposes, couldn’t get the same concessions out of Mastercard, its card network.
Here’s a link to the study mentioned in the article, where MIT researchers successfully de-anonymized financial data that these companies claim had privacy protections.
France Claims Apple is Undermining its COVID App Efforts
On Tuesday the French government accused Apple of undermining its efforts with its contact tracing app “StopCovid.”
Apple’s iPhones normally block access to Bluetooth unless the user is actively running an app. French officials want Apple to change the settings to let their app access Bluetooth in the background, so it is always on. So far, they say, Apple has refused.
O, the French minister, said he could not explain the reasoning behind Apple’s decision on Bluetooth. “We consider that oversight of the healthcare system, fighting the coronavirus, is a matter for governments and not necessarily for big American companies,” he said.
As we pointed out on our Daily Observations podcast, most people aren’t going to care about the privacy aspects of these apps. But they will care about battery life, and apps like these constantly using Bluetooth in the background will undoubtedly be a factor, Bluetooth Low Energy or not.
You Can Now Use Sign In with Apple on Squarespace
You can now use Sign In with Apple on Squarespace, the latest company to support Apple’s private sign in service.
France Says iOS Prevents Contact Tracing Apps From Running in the Background
France wants Apple to roll back an iOS privacy feature that limits apps constantly using Bluetooth in the background.
eBay Now Supports Sign In with Apple
eBay recently updated its iOS app to version 6.0.0 and the major feature it adds is Apple’s private Sign In with Apple option.
Zoom: Don’t Want to Get Routed Through Chinese Servers? Fork Over Your Cash
One of Zoom’s controversies is how it routes some of its network traffic through China’s servers. If you’re privacy conscious, you can opt out of specific data center regions starting April 18. But this is only for paying customers.
This feature gives our customers more control over their data and their interaction with our global network when using Zoom’s industry-leading video communication services.
I can’t say I agree. It’s not about making privacy a paid feature, it’s that Zoom is exploiting its own insecurity to create a paid feature. Next step: Making end-to-end encryption a paid feature, and leaving free users to fend for themselves.
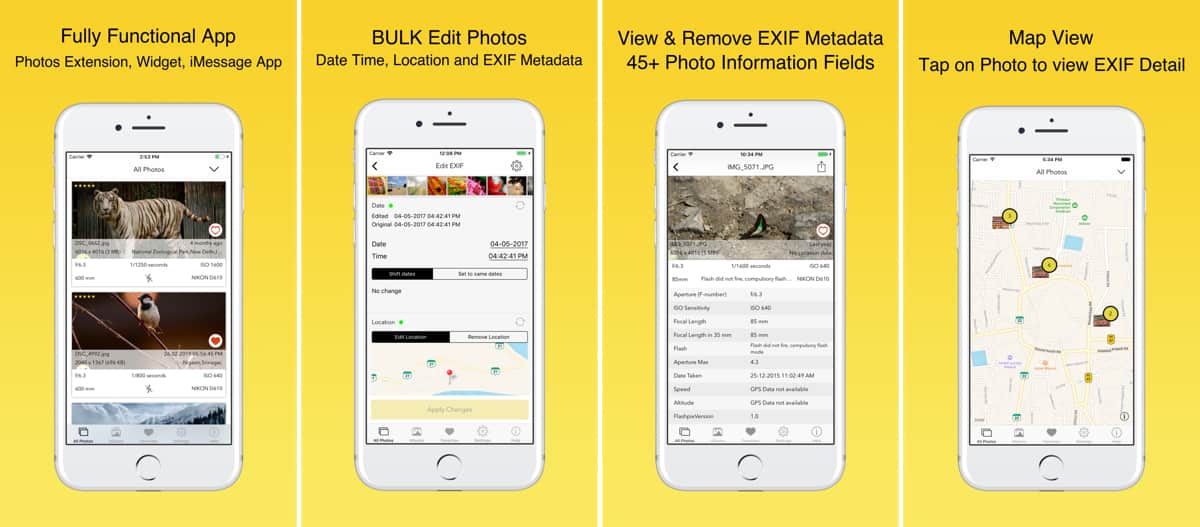
App Sale: EXIF Viewer by Fluntro is Currently Free
Normally US$2.99, EXIF Viewer by Fluntro is free right now. As the name suggests it lets you view the EXIF metadata of photos, which can include location, time stamp, device model, and more. You can delete the metadata using the app as well, which is useful if you don’t want websites like Facebook to read your location from the photo. Most importantly you can bulk edit metadata if you’re working with multiple photos.
DuckDuckGo Publishes List of Privacy Tools for Remote Work
Earlier this month I wrote an article covering five private Zoom alternatives. Today DuckDuckGo published a similar list, although it’s not focused on Zoom. I think it’s a good list.
As a remote-first Internet privacy company, we firmly believe that working outside of a traditional office setting should not compromise your privacy. To that end, we’ve rounded up some useful privacy-respecting tools and important settings that you can confidently utilize while working remotely.
Zoom Meetings Aren’t Encrypted End-to-End, Despite Marketing
Along with recent news that Zoom sent your data to Facebook (although it stopped) now we learn that its video calls don’t use end-to-end encryption, despite the company marketing it as such.
…But despite this misleading marketing, the service actually does not support end-to-end encryption for video and audio content, at least as the term is commonly understood. Instead it offers what is usually called transport encryption, explained further below.
It just keeps getting worse for Zoom. It’s unfortunate the company has chosen such tactics, because it really is one of the better video calling apps out there.
7 Private Alternatives to Apple Apps and Services
Andrew found seven Apple alternatives to use if you don’t want your data shared with the FBI, including Bitwarden, Cryptomator, and more.
Why is Zoom Sending Our Data to Facebook?
As people are required to work from home, apps like Zoom help us with video conferencing. But why is the iOS app sending our data to Facebook?
Upon downloading and opening the app, Zoom connects to Facebook’s Graph API, according to Motherboard’s analysis of the app’s network activity. The Graph API is the main way developers get data in or out of Facebook. The Zoom app notifies Facebook when the user opens the app, details on the user’s device such as the model, the time zone and city they are connecting from, which phone carrier they are using, and a unique advertiser identifier created by the user’s device which companies can use to target a user with advertisements.
I’ll add this to my #DeleteFBSDK endeavors.
The FBI is Collecting Your Data Through its ‘FitTest’ App
The FBI has been promoting its fitness app called FitTest to help people exercise at home. It’s also collecting your data.
…an FBI spokesperson reiterated the app’s privacy statement, adding that “the app does not gather or save any personal information other than what you select for your profile.”
But the app’s privacy statement makes room for some tracking: When FitTest accesses pages from the official FBI website, it says, “fbi.gov’s privacy policy applies.” The fbi.gov privacy policy states that “individuals using this computer system are subject to having all of their activities monitored and recorded.”
I can’t wait for the FBIPhone and FBIMessage apps.
KeepSolid VPN Unlimited Adds DNS Firewall for Customers
KeepSolid’s VPN Unlimited added a new feature for its customers. This DNS firewall can block domains associated with malware, porn, drugs and alcohol, gambling, games, and more.
This benefit of KeepSolid DNS Firewall is closely connected with the previous one. If you don’t open a malicious website, you won’t get infected with malware. Better prevent than cure, agree? And there is really much to avoid, as malware attacks are exponentially increasing over time.
Great news for KeepSolid customers. And if you’re not a customer, I recommend reading my roundup of DNS services to use.
Lawyers: Turn off Alexa and Google Home Before Confidential Meetings
Lawyers who are working from home are encouraged to turn off devices like Amazon Alexa and Google Home because these products may eavesdrop.
“Perhaps we’re being slightly paranoid, but we need to have a lot of trust in these organizations and these devices,” Hancock said. “We’d rather not take those risks.”
The firm worries about the devices being compromised, less so with name-brand products like Alexa, but more so for cheap knock-off devices, he added.
It’s definitely not just cheap knock-offs.
Should We Ban Targeted Advertising?
Gilad Edelman asks an important question at Wired: Why don’t we just ban targeted advertising?
The solution to our privacy problems, suggested Hansson, was actually quite simple. If companies couldn’t use our data to target ads, they would have no reason to gobble it up in the first place, and no opportunity to do mischief with it later. From that fact flowed a straightforward fix: “Ban the right of companies to use personal data for advertising targeting.”
Instead of, or in addition to, banning or restricting targeted advertising, I think we should go a step further and restrict data collection, which is what these companies use for these ads in the first place. When any startup without a track record can enter the business of collecting and selling our personal information, that’s a problem.
Google: “We Don’t Sell Your Data, We Just Monetize It”
One way to avoid the California Consumer Privacy Act is to claim that you don’t sell data. This is what Google has seemingly done.
Google monetizes what it observes about people in two major ways: It uses data to build individual profiles with demographics and interests, then lets advertisers target groups of people based on those traits. It shares data with advertisers directly and asks them to bid on individual ads.
As I tweeted yesterday, there is no difference between selling “access” to data and selling data “directly.” In both scenarios, people are products for advertisers. Although I’m sure lawsuits have been won and lost on lesser technicalities.
Social Media Platform ‘MeWe’ Launches Dual-Camera Videos
MeWe, which presents itself as a privacy social network, launched dual-camera videos and a new feature called MeWe Stories.
This Safari Extension Can Clean Links With Trackers
A Safari extension called Clean Links can automatically remove tracking parameters from URLs. Blocked trackers include UTM by Google Analytics, FBCLID by Facebook, and others. It is a random app from GitHub outside of the App Store. I uploaded it to VirusTotal and it didn’t show anything weird. But the creator also makes the source code available.
To install Clean Links you can either download the latest prebuild extension from the releases tab, or you can clone the repository and build it yourself.
I also use a shortcut that can accomplish the same thing on iOS and iPadOS.
iPhone Patent Reveals ‘Gaze-Dependent Display Encryption’
A new patent reveals “gaze-dependent display encryption” whereby the display would show real data to its owner and fake data to anyone else.
Proton Apps Receive Alternative Routing to Stop Censorship
Proton apps will get new alternative routing as a way to block attempts at censorship, whether it’s by governments, ISPs, or network admins.