The FBI, CISA, and HHS are issuing a joint alert to warn of the threat of ransomware attacks currently affecting U.S. healthcare systems.
Security
NSA Avoids Discussing Back Doors in Commercial Products
The U.S. National Security agency is dodging questions about back doors in commercial products and whether it’s continuing this practice. The article mentions Dual EC, a type of encryption algorithm the NSA tried to get ratified as a global standard. Why? Because they could easily crack it.
Juniper Networks got into hot water over Dual EC two years later. At the end of 2015, the maker of internet switches disclosed that it had detected malicious code in some firewall products. Researchers later determined that hackers had turned the firewalls into their own spy tool here by altering Juniper’s version of Dual EC.
And that’s the reason we oppose these kinds of back doors or “weaknesses on purpose” on Security Friday. If one group can easily crack it, so eventually will other groups.
Researchers Extract Intel CPU Encryption Key
Security researchers have successfully extracted the Intel CPU encryption key used to secure updates to the chip.
The key makes it possible to decrypt the microcode updates Intel provides to fix security vulnerabilities and other types of bugs. Having a decrypted copy of an update may allow hackers to reverse engineer it and learn precisely how to exploit the hole it’s patching. The key may also allow parties other than Intel—say a malicious hacker or a hobbyist—to update chips with their own microcode, although that customized version wouldn’t survive a reboot.
Of course, it’s the “other parties” to worry about. The key can be extracted from any chip that uses Intel’s Goldmont architecture. This is used for low-power chips like the Atom, Celeron, and Pentium brands.
Big Tech CEOs to Speak on Section 230 Law Tomorrow
The CEOs of Facebook, Alphabet, and Twitter will appear before the Senate Commerce Committee tomorrow to speak about Section 230.
Zoom Rolls Out End-to-End Encryption for Video Calls
Starting next week, video conferencing app Zoom is finally adding end-to-end encryption to its platform.
Zoom’s E2EE offering uses public key cryptography. In short, the keys for each Zoom meeting are generated by participants’ machines, not by Zoom’s servers. Encrypted data relayed through Zoom’s servers is indecipherable by Zoom, since Zoom’s servers do not have the necessary decryption key. This key management strategy is similar to that used by most end-to-end encrypted messaging platforms today.
Good to see Zoom doing this; they’ve certainly had misses in the past. Update: The new version is now available for most users.
Link Previews in Chat Apps Could Leak Your IP Address
Security researchers found that link previews in chat apps could expose data like IP addresses if not implemented properly. Or they could be downloading as much as gigabytes of data in the background. They tested a variety of different messaging apps, and iPhone users will be relieved to know that iMessage didn’t experience any of these security leaks.
We think there’s one big takeaway here for developers: Whenever you’re building a new feature, always keep in mind what sort of privacy and security implications it may have, especially if this feature is going to be used by thousands or even millions of people around the world.
Security Friday, Halide Mark II – TMO Daily Observations 2020-10-23
Andrew Orr joins host Kelly Guimont for Security Friday news and updates, and a look at Halide Mark II just in time for iPhonemas Day!
Thousands of Law Enforcement Agencies Use Phone Cracking Tools
Upturn, a non-profit focused on the use of technology by police, used over 110 public records filed with law enforcement departments across the country to figure out how many of them use phone cracking tools, or mobile device forensic tools (MDFTs).
Based on 110 public records requests to state and local law enforcement agencies across the country, our research documents more than 2,000 agencies that have purchased these tools, in all 50 states and the District of Columbia. We found that state and local law enforcement agencies have performed hundreds of thousands of cellphone extractions since 2015, often without a warrant.
Kelly and I will definitely share our thoughts in this week’s Security Friday.
Address Bar Spoofing Bugs Surface on Mobile Browsers
A number of address bar spoofing vulnerabilities have surface on mobile browsers, and Rafay Baloch wrote about them. There was one found in Safari but Apple patched it in September with iOS 13.6. The other bugs mostly concern Opera.
With ever growing sophistication of spear phishing attacks, exploitation of browser-based vulnerabilities such as address bar spoofing may exacerbate the success of spear phishing attacks and hence prove to be very lethal. First and foremost, it is easy to persuade the victim into stealing credentials or distributing malware when the address bar points to a trusted website and giving no indicators forgery, secondly since the vulnerability exploits a specific feature in a browser, it can evade several anti-phishing schemes and solutions.
Security Friday, New iPhone Prepping – TMO Daily Observations 2020-10-16
Andrew Orr joins host Kelly Guimont for Security Friday news, The Week In Data Breaches, and tips for a seamless transfer to a new iPhone.
Barnes & Noble Hack Revealed in Emails to Customers
A Barnes & Noble hack occurred on Saturday, October 10, customers learned in an email from the retailer. Data that was accessible included email addresses, billing/shipping addresses, and telephone number. Financial data like credit cards were safely encrypted.
According to Barnes & Noble’s Nook Twitter account, a “system failure” was responsible for the service interruption for Nook owners. The firm said it was “working urgently to get all NOOK services back to full operation. Unfortunately it has taken longer than anticipated, and we sincerely apologize for this inconvenience and frustration.”
Report: Some Robinhood Accounts Were Hacked
Bloomberg reports that some Robinhood users had their accounts hacked and investments liquidated. But Robinhood said that the company itself wasn’t hacked.
A limited number of customers appear to have had their Robinhood account targeted by cyber criminals because of their personal email account (that which is associated with their Robinhood account) being compromised outside of Robinhood. We’re actively working with those impacted to secure their accounts.
Apple’s Internal Networks Were Hacked for Three Months
But don’t worry, they were hacked by good guys working under Apple’s bug bounty program. Sam Curry, Brett Buerhaus, Ben Sadeghipour, Samual Erb, and Tanner Barnes found a total of 55 vulnerabilities.
During our engagement, we found a variety of vulnerabilities in core portions of their infrastructure that would’ve allowed an attacker to fully compromise both customer and employee applications, launch a worm capable of automatically taking over a victim’s iCloud account, retrieve source code for internal Apple projects, fully compromise an industrial control warehouse software used by Apple, and take over the sessions of Apple employees with the capability of accessing management tools and sensitive resources.
When I first saw the news I was aghast to learn that Apple only paid them US$55,000, but the blog post was updated to add that the team so far has gotten 32 payments totaling US$288,500. Still doesn’t seem enough to me. Apple needs to work on its internal security.
Apple Wants to Store Your ID Digitally. What Could Go Wrong?
William Gallagher writes how Apple is working on methods to store your ID digitally in Wallet, like credit cards. But I found this part concerning:
This all presumes that we are able to present our ID. There are situations, such as when we’re incapacitated, when we need to be identified yet we cannot personally do anything about that. In this case, Apple proposes that under the right circumstances, our devices could “automatically transmit the user’s identity credential.”
Apple gives the example of a first responder, “such as police officer, firefighter, etc,” who could legitimately possess a device that would automatically request ID like this.
I bet law enforcement would love a Stingray-like device that can automatically harvest IDs when they walk through a protest.
Organizations Using Both Mac and Non-Mac Devices Consider Apple Devices Safest Out The Box
More than three-quarters of organizations that use both Mac and non-Mac devices consider Apple’s offerings as the most secure out of the box.
CleverFiles Releases Disk Drill 4 Mac Data Recovery Software
CleverFiles released Disk Drill 4 on Tuesday, which Andrew will be reviewing in the next few weeks. It’s data recovery software
More Details on the Mac T2 Security Chip Jailbreak
Catalin Cimpanu shares more details of the T2 chip jailbreak I wrote about last week.
The attack requires combining two other exploits that were initially designed for jailbreaking iOS devices — namely Checkm8 and Blackbird. This works because of some shared hardware and software features between T2 chips and iPhones and their underlying hardware.
Unfortunately, since this is a hardware-related issue, all T2 chips are to be considered unpatchable. The only way users can deal with the aftermath of an attack is to reinstall BridgeOS, the operating system that runs on T2 chips.
Security Friday, Widgets, and You – TMO Daily Observations 2020-10-02
Andrew Orr joins host Kelly Guimont for Security Friday news and updates, and a discussion about iOS 14’s widgets and what they can/can’t do.
Apple’s T2 Security Chip Jailbroken by Checkra1n
The latest update of checkra1n adds support for bridgeOS, which runs on the T-series of chips. These are responsible for the Touch Bar, managing encrypted data in its Secure Element, and controlling Mac camera access.
The ability to exploit the T2 processor could also allow you to bypass the anti-repair mechanism built into the Touch Bar. Further, it may allow hackers to get rid of the password or unlock MDM-locked systems.
As far as the OS goes, we could also add secure boot certificates like Microsoft’s secure boot signing or a self-signed Linux certificate.
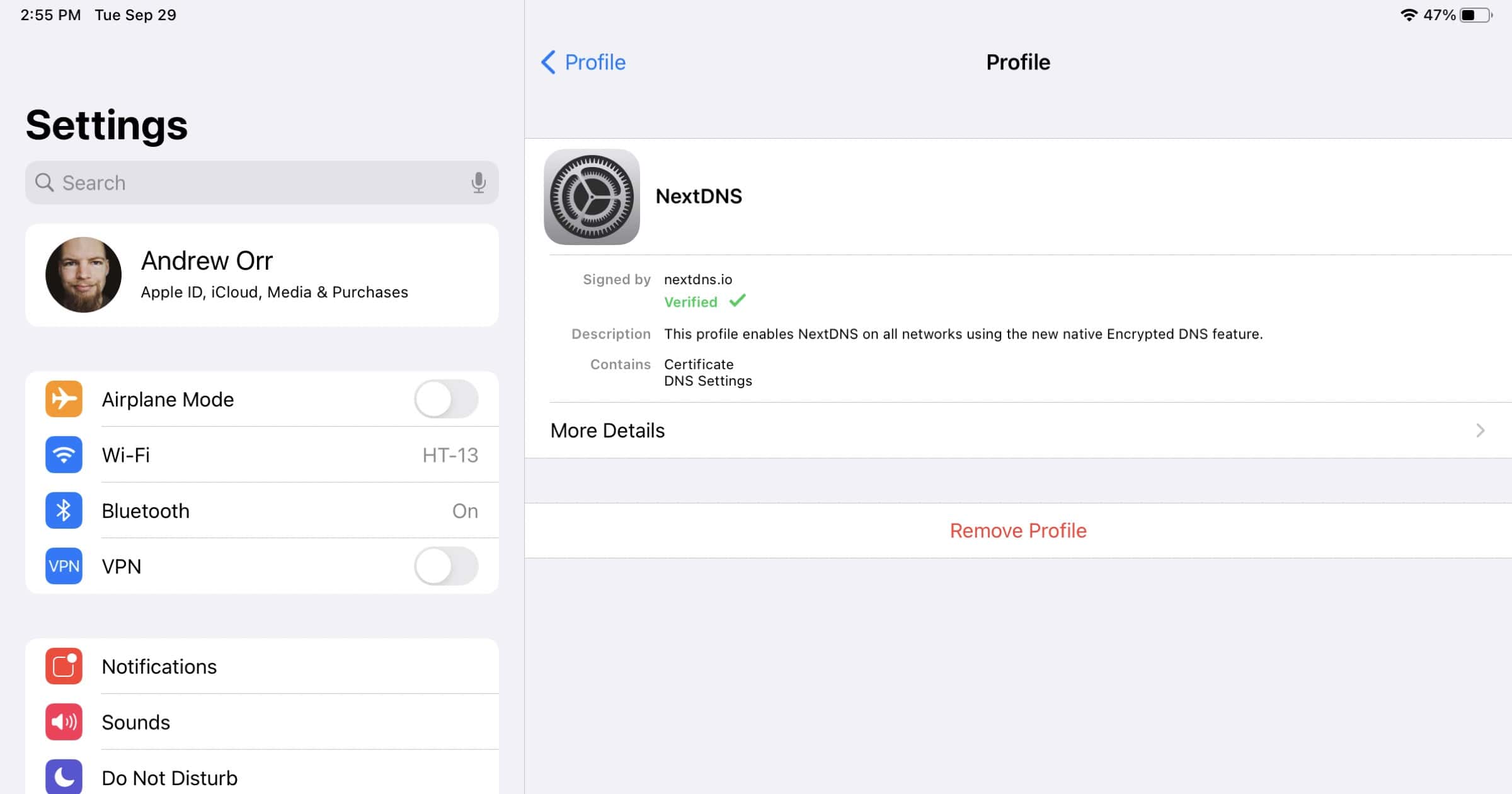
NextDNS Lets You Create Configuration Files for iOS 14 Encrypted DNS
NextDNS released a new tool on Tuesday that lets you generate a configuration profile to let you use iOS 14 encrypted DNS without needing the NextDNS app.
Can iOS 14 Widgets Steal Your Keyboard Info?
After claims that iOS 14 widgets are up to no good, can they access your keyboard and act as keyloggers? First, as the developer of Widgetsmith says:
Leaving for a moment that I don’t think that is technically possible for a widget to read the keyboard. Widgetsmith was built from the ground up with complete privacy in mind and collects essentially no data about its users.
After using the app I wrote about this morning, Sticky Widgets, I’d say yes they can access your keyboard, because if not then Sticky Widgets would be unusable and you couldn’t type anything into them. Can they access the keyboard without user consent? Most likely not, as the quote continues: “Widgets use SwiftUI views to display their content. WidgetKit renders the views on your behalf in a separate process. As a result, your widget extension is not continually active, even if the widget is onscreen.”
Security Friday, Keychain Tips, Settings Shortcuts – TMO Daily Observations 2020-09-25
Andrew Orr joins host Kelly Guimont to discuss Security Friday news, tips for secure payment options, and some new shortcuts.
‘Blacklight’ Tool Reveals Website Trackers
A tool called Blacklight has been making waves in the news recently. When you enter a website address into the page it scans it to reveal user-tracking technology.
Blacklight works by visiting each website with a headless browser, running custom software built by The Markup. This software monitors which scripts on that website are potentially surveilling the user by performing seven different tests, each investigating a specific, known method of surveillance.
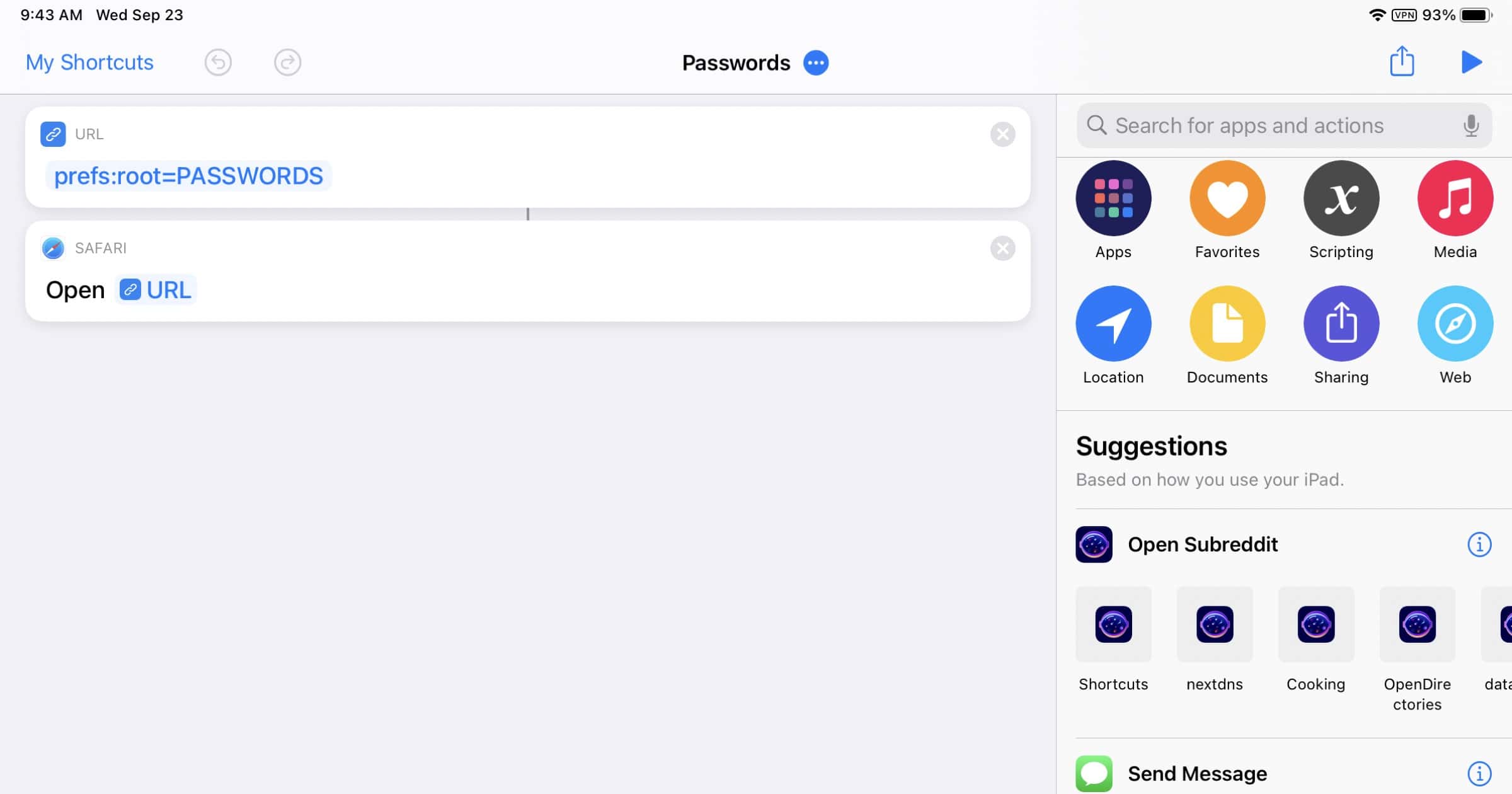
Quickly Access iCloud Keychain With This Apple Engineer’s Shortcut
Ricky Mondello works on app and website authentication as well as password management at Apple. They recently created a shortcut that lets you quickly access iCloud Keychain, so instead of opening Settings and scrolling down to tap on Passwords, it’s a one-tap method to directly open the Passwords section. Separately from that, this is also something you can do yourself using the Settings Shortcut Generator. You can quickly jump to a variety of different places within Settings. One that I recently created is jumping to Settings > Privacy > Photos to manage app access to photos.