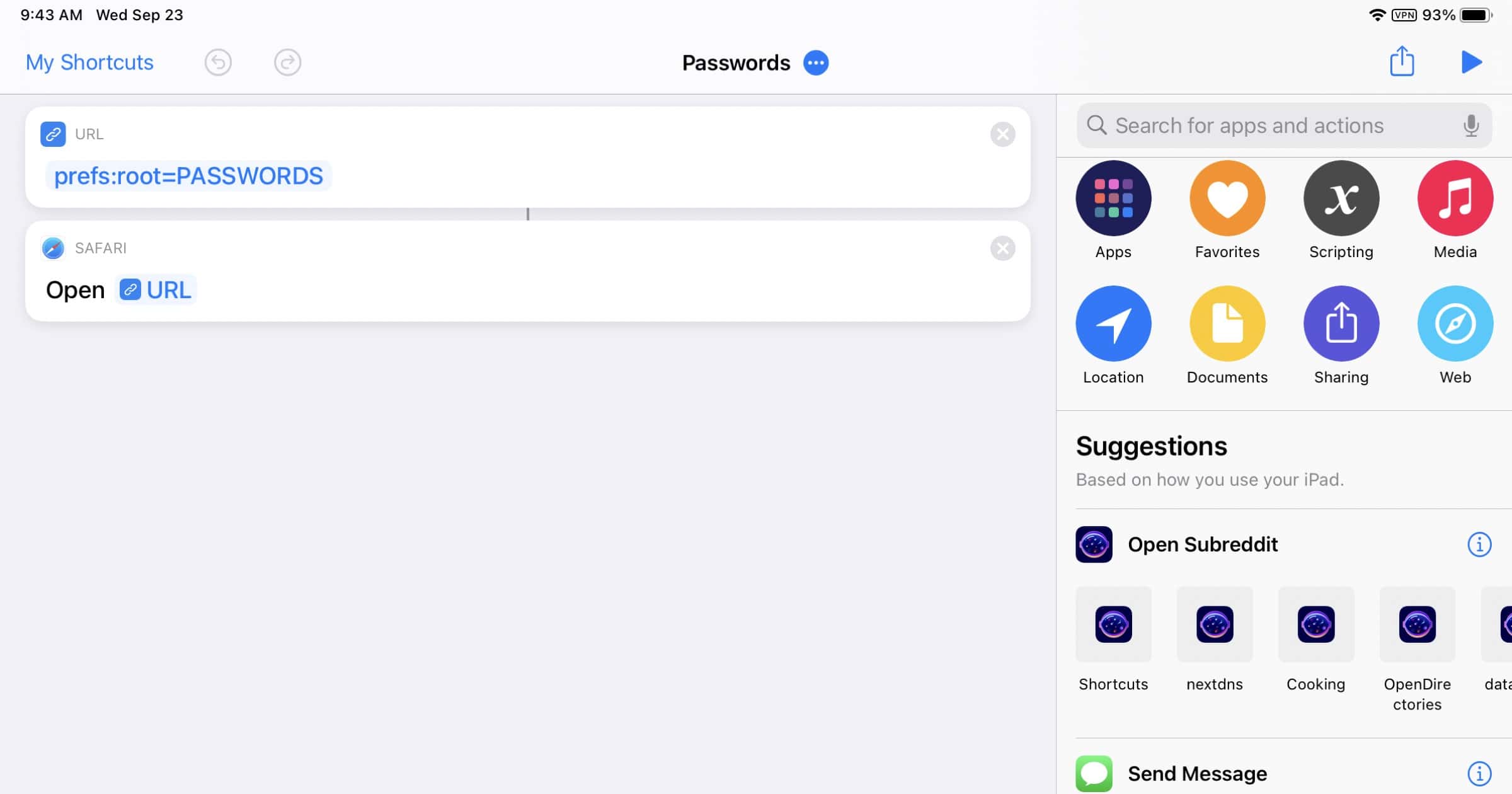
Ricky Mondello works on app and website authentication as well as password management at Apple. They recently created a shortcut that lets you quickly access iCloud Keychain, so instead of opening Settings and scrolling down to tap on Passwords, it’s a one-tap method to directly open the Passwords section. Separately from that, this is also something you can do yourself using the Settings Shortcut Generator. You can quickly jump to a variety of different places within Settings. One that I recently created is jumping to Settings > Privacy > Photos to manage app access to photos.
Security
1Password Partners With Privacy for Virtual Credit Cards
Password generator 1Password is teaming up with Privacy.com to let customers generate virtual credit cards right in the browser.
Bing Data Leak Exposes Search Queries, Location Data, More
The Wizcase security team discovered a Microsoft Bing data leak due to an unsecured server, leaking data like GPS coordinates and searches.
How the United States is Ensuring Votes are Secure
Max Eddy writes an examination of election engineering and how the U.S. can ensure voting security. The part I think is fascinating is the work of Sam Curry, CSO of cybersecurity company Cybereason. His team has been simulating election attacks to figure out how best to protect our elections.
He’s observed numerous strategies and has advice on how best to protect an election. The people playing the role of defenders, usually given the role of law enforcement, “must create open lines of communication between government departments and also media sources and social media companies,” said Curry. Knowing who to call and when to call them and having a reliable back-up system in case one fails (or is intentionally sabotaged) are all critical.
Safari 14 is out and it’s not Just for macOS Big Sur
Safari 14 will be included but it’s not limited to Big Sur. Mac users running macOS Mojave and macOS Catalina can also get the update.
CISA Believes China Hacked US Government Systems
According to the Cybersecurity and Infrastructure Security Agency, Chinese-affiliated hackers have compromised U.S. government computer systems.
“This beaconing is a result of cyber threat actors successfully completing cyber operations that are often designed around emergent vulnerabilities and reliant on existing exploitation tools,” the advisory states. “CISA observed activity from a Federal Government IP address beaconing out to the threat actors’ [command and control] server.”
Get we just get it together for 10 seconds, please?
Gaming Company Razer Leaked 100,000 Users’ Data
In August, security researcher Volodymyr Diachenko found a server owned by Razer that exposed the data of over 100,000 users. It took the company over three weeks to get around to fixing the issue.
The cluster contained records of customer orders and included information such as item purchased, customer email, customer (physical) address, phone number, and so forth—basically, everything you’d expect to see from a credit card transaction, although not the credit card numbers themselves. The Elasticseach cluster was not only exposed to the public, it was indexed by public search engines.
Apple Announces New CryptoKit APIs and Other Updates
Apple shared an update to its developer page to announce updates to CryptoKit, like new APIs and support for PEM and DER formats.
Reboot Your iPhone Weekly as a Security Measure
Adrian Kingsley-Hughes has a tip for iPhone owners: Reboot it at least once a week as a security measure.
Not only does this clean the systems RAM and get it ready to do more work, it also helps protect against remote exploits by making it harder for hackers to keep control of your iPhone — hacks don’t survive reboots.
A good, practical, and easy tip for Apple users.
Prison Phone Service ‘Telmate’ Leaks Data of Inmates
Telmate, owned by Global Tel Link, makes an app for prisoners to send messages and calls to friends and family. It exposed a database of private messages, call logs, and personal information numbers in the tens of millions. Why? The database wasn’t secured with a password.
Comparitech security researcher Bob Diachenko on August 13, 2020 discovered the unsecured database and immediately reported it to Global Tel Link, the company that owns and operates Telmate. The company, to its credit, responded within two hours and secured the database an hour later, but it’s possible that other unauthorized parties accessed it prior to Diachenko’s disclosure.
Security Friday News, iOS 14 Privacy – TMO Daily Observations 2020-09-04
Andrew Orr and Bryan Chaffin join host Kelly Guimont to discuss Security Friday news, and what privacy will look like in iOS 14.
Former Apple Employee Jon Callas Joins EFF as Technology Projects Director
Jon Callas, formerly of Apple, PGP Corp, Blackphone, and Silent Circle, has joined the EFF as its Technology Projects Director.
Deepfake Detection, In-Depth Exposure Tracking – TMO Daily Observations 2020-09-03
Bryan Chaffin and Charlotte Henry join host Kelly Guimont to discuss Microsoft’s Deepfake Detector, and digging into exposure tracing in iOS.
ProtonDrive’s End-to-End Encryption Security Revealed
ProtonDrive (from the makers of ProtonMail and ProtonVPN) is in the final stages of development before it gets a beta launch later in 2020. The team revealed its end-to-end encryption security in a blog post.
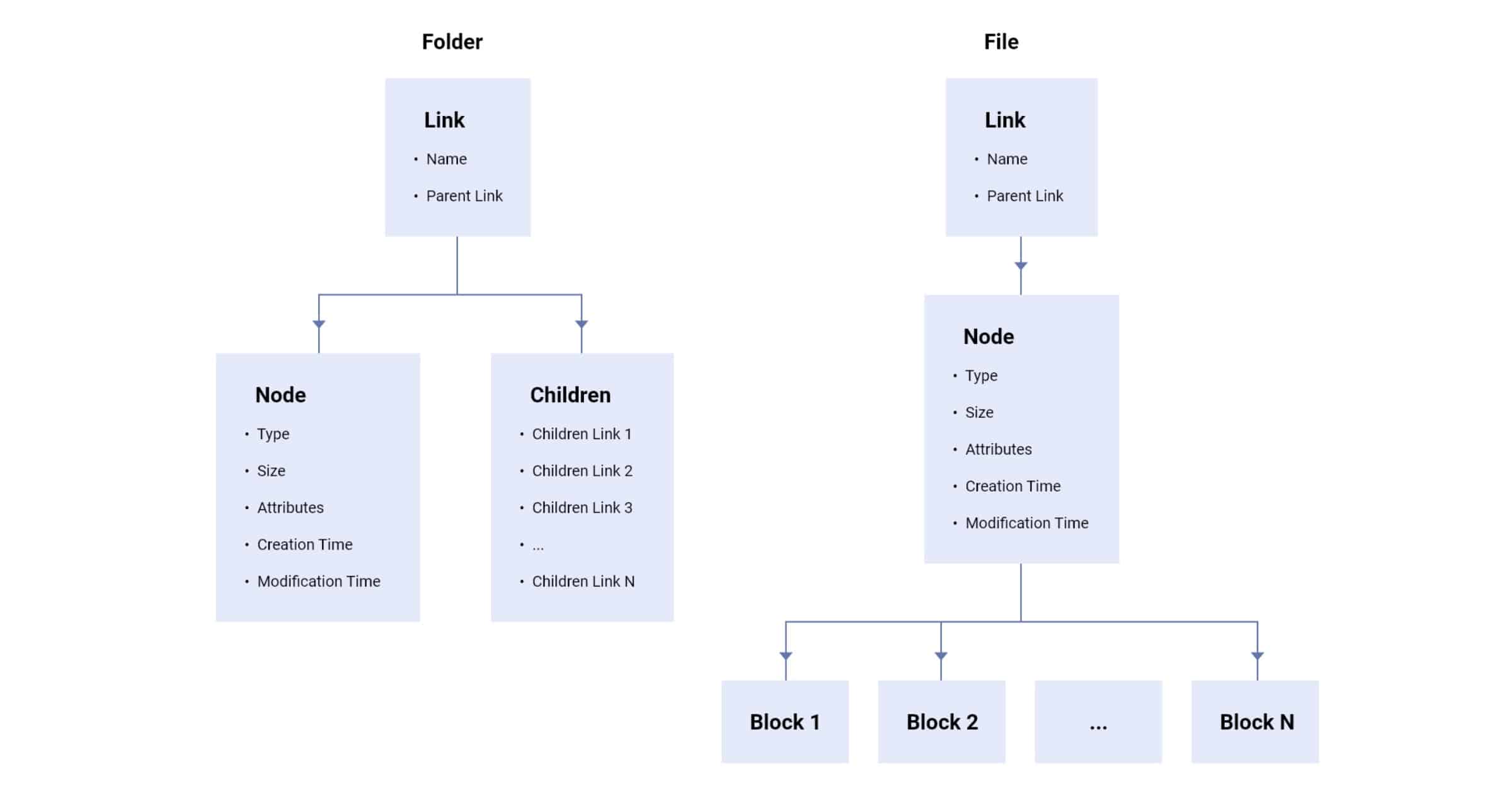
Files and folders are arranged in a tree structure. Therefore, there is a recurring pattern where a file or folder’s asymmetric key is locked with a passphrase, which in turn is encrypted with the asymmetric key of their parent folder. All passphrases are signed with the address key of the user, without which a malicious server could forge the contents of the tree.
Apple’s Notarization Security Accidentally Approved ‘OSX.Shlayer’ Malware
Security researchers say they have found OSX.Shlayer malware disguised as an Adobe Flash installer and contained code notarized by Apple.
Safari Web Share API Bug Lets Local Files be Stolen
Security firm REDTEAM.PL found a bug within Safari’s Web Share API that let them steal local files and Safari browsing history.
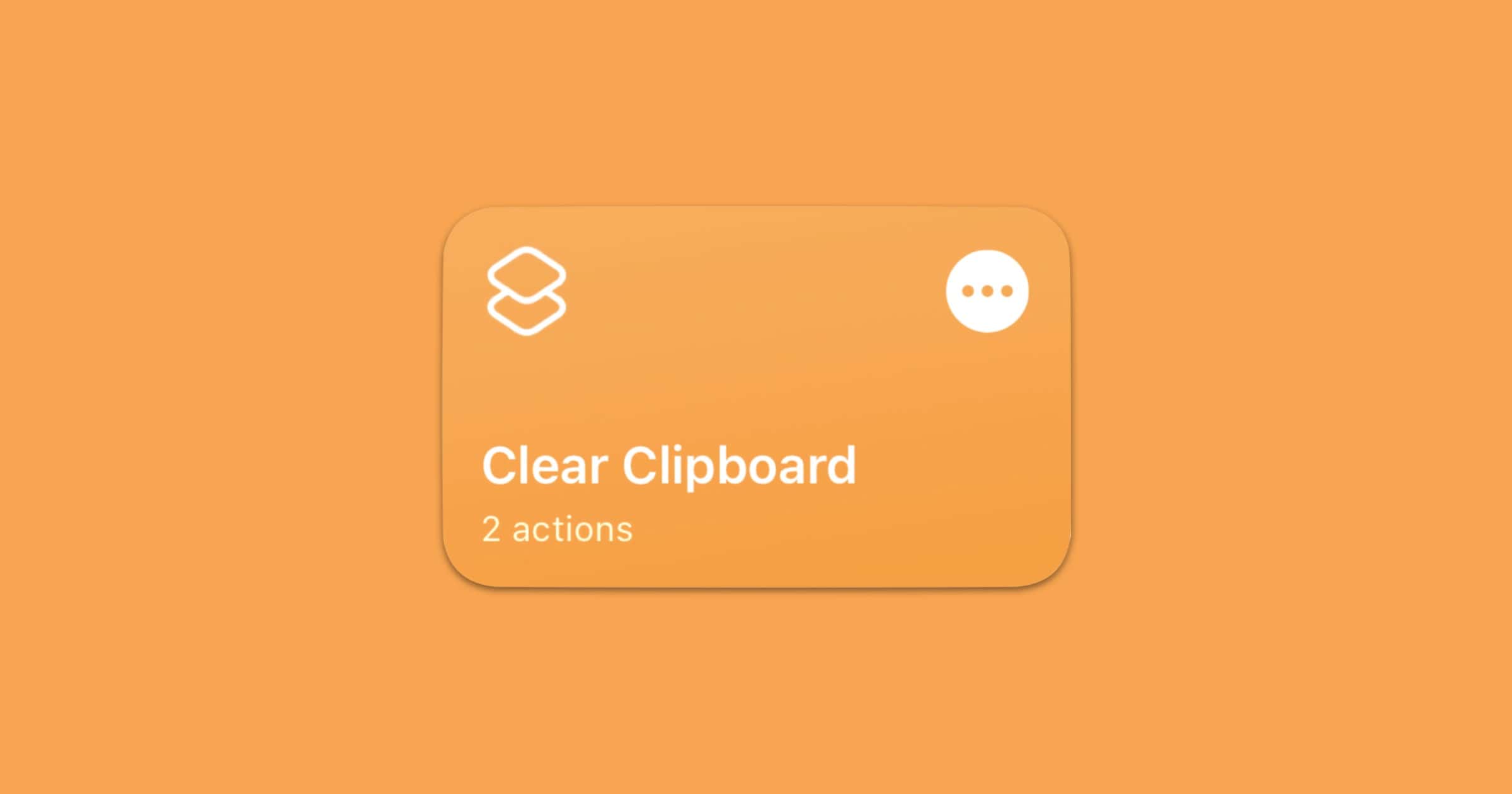
This ‘Clear Clipboard’ Shortcut Empties Your Clipboard Automatically
Redditor u/SpamSencer created a Clear Clipboard shortcut that does exactly what the name says: It automatically clears your clipboard. With iOS 14 Apple introduced a feature that shows when an app accesses the clipboard, like TikTok and Microsoft. You could even set it up as an automation so that whenever you open any app of your choosing, the shortcut will run (an iOS 14 feature). You’ll just have to painstakingly tap on every app you have installed if you choose to automate it.
Security Friday, Encrypted Email – TMO Daily Observations 2020-08-21
Andrew Orr and Jeff Butts join host Kelly Guimont to discuss Security Friday news and how to encrypt email on iOS devices.
‘Deep Social’ Data Leak Exposes 235 Million Profiles of Instagram, TikTok, YouTube
A database containing almost 235 million social media profiles of users from Instagram, TikTok, and YouTube has been exposed because it wasn’t password-protected.
Evidence suggests that much of the data originally came from a now-defunct company: Deep Social. The names of the Instagram datasets (accounts-deepsocial-90 and accounts-deepsocial-91) hint at the data’s origin. Based on this, [security researcher Bob] Diachenko first contacted Deep Social using the email address listed on its website to disclose the exposure. The administrators of Deep Social forwarded the disclosure to Social Data. The CTO of Social Data acknowledged the exposure, and the servers hosting the data were taken down about three hours later.
Security Friday: Instagram, Packet Loss, and Fortnite – TMO Daily Observations 2020-08-14
Andrew Orr and Bryan Chaffin join host Kelly Guimont to discuss Security (read: Facebook) news, Apple Card id protection, and Fortnite. Extended edition brought to you by intellectual laziness.
pCloud Update Lets Users Decide Where Files are Stored
pCloud is an encrypted cloud storage service, and a recent update gave users the ability to decide in which server their files are stored.
All pCloud users will be able to choose the server location where their files are stored. This will give users greater control over the security of their files. Once the choice of where to store the data is made during registration – in the US or Europe – it is practically impossible to transfer them without the user’s knowledge or permission. Currently, the option to select the server location is available only to newly registered users.
Apple Card Customers Should Use Mastercard ID Theft Protection
There are a couple of benefits you can receive if you’re an Apple Card customer. One benefit is Mastercard ID Theft Protection.
Security Friday - Intel, LastPass, Clario – TMO Daily Observations 2020-08-07
Andrew Orr and Jeff Butts join host Kelly Guimont to discuss Security Friday news, and a new headphone option coming with iOS 14.
‘Have I Been Pwned’ Database Now Open Source
Troy Hunt is making his Have I Been Pwned database open source. He says it’s already a community project with companies like Cloudflare providing free services to HIBP.
The single most important objective of that process was to seek a more sustainable future for HIBP and that desire hasn’t changed; the project cannot be solely dependent on me. Yet that’s where we are today and if I disappear, HIBP quickly withers and dies.