After Google announcing a doc accessory for Pixel Tablet, we hear of Apple working on similar tech to use the iPad as a smart home display.
Search: smart home
Watching Watches and Smart Homes - TMO Daily Observations 2022-10-17
TMO Managing Editor Jeff Butts and Ken revisit a recent Piper Sandler survey of teen Apple Watch ownership in light of new data from Counterpoint Research. Then, Jeff does a little smart-home 101, and wonders over Level’s apparent messaging fumbles.
Insteon Smart Home System May Have Shut Down Without Telling Customers
Insteon Smart Home system have shut down but it seems its hundreds of customers who own various Insteon products were not informed.
Matter Smart Home Standard Delays Release Until Fall 2022
The first cross-platform protocol for smart home technology, the Matter smart home standard, is delayed but expected to launch in Fall 2022.
Security Friday: Smart Home Practical Tips – TMO Daily Observations 2022-01-07
Andrew Orr and host Kelly Guimont chat about Security Friday news and updates, including tips on keeping your smart home gear safe and secure.
Smart Home Tips and CES Announcements – TMO Daily Observations 2022-01-04
Jeff Butts joins host Kelly Guimont to discuss smart home CES announcements and a tip for devices that aren’t officially supported by HomeKit.
Eve Launches Two Firsts in the Smart Home Industry
In two smart home categories, Eve is breaking ground with industry firsts. You can automate your blinds with Thread and take Eve Cam outside.
Eve Smart Home Holiday Deals for Last-Minute Shopping
Eve Smart Home accessories make excellent gifts. These last-minute discounts will help you save on your shopping spree.
South Korean Hack Shows Need for Better Smart Home Security
A recent string of hacks on South Korean apartment complexes makes the need for better smart home security crystal clear.
Last-Minute Cyber Monday Smart Home Deals
These Cyber Monday smart home deals are waiting. Get your HomeKit accessories at prices you likely won’t see again for quite some time.
Sleep Technology Meets the Smart Home with ReST
Sleep technology has really taken off, and we even have smart beds now. Let’s see how well the ReST Smart Bed performs for this techie.
New 'BotenaGo' Targets Routers and Smart Home Devices in Devastating Attack
AT&T Alien Labs discovered malware it dubs BotenaGo. It affects millions of routers and Internet of Things devices found with smart homes. The “devastating” part comes from the fact that it uses over 30 separate exploits due to insecure devices.
The BotenaGo malware starts by initializing global infection counters that will be printed to the screen, informing the hacker about total successful infections. It then looks for the ‘dlrs’ folder in which to load shell scripts files. A loaded script will be concatenated as ‘echo -ne %s >> ‘. If the ‘dlrs’ folder is missing, the malware will stop and exit at this point. For the last and most important preparation, the malware calls the function ‘scannerInitExploits’, which initiates the malware attack surface by mapping all offensive functions with its relevant string that represent the targeted system.
Could Apple Make Major Smart Home Moves in 2022?
As we go hurtling towards the holiday season, it’s always exciting to look at what might come next. Dan Moren has written a very astute take at what Apple might do in 2022 for Macworld. His look at the moves the company could make in the smart home market is particularly interesting.
Apple’s had a challenging couple years in the home space. It’s discontinued its full-size HomePod in favor of the smaller HomePod mini, and while it’s ramped up support for the upcoming Matter initiative that aims to interconnect smart home devices across manufacturers, that really won’t kick off in earnest until next year. But word of a “homeOS” project reared its head once again this week, after a mention in an Apple job posting. The term had cropped up earlier this year, ahead of the Worldwide Developers Conference, but nothing more was heard of it until now. It could suggest a more in-depth investment in smart home tech for Apple, and, combined with a recent hire to oversee HomePod software might mean the company is reinvigorating development in that area.
Smart Home Networks And You – TMO Daily Observations 2021-11-09
Jeff Butts and Dave Hamilton join host Kelly Guimont to discuss the latest developments in smart home networking and why it matters to your home.
Smart Home Technology Finally Has a Standard
The Matter standard is doing what we’d hoped for: unifying smart home technology with a standard way for devices to talk to each other.
(Update) 'Flic Twist' is a New Dial for Smart Home Products With Matter Support
Flic Twist is a product to control your smart home. It’s wireless and can be placed anywhere. Pre-orders begin on November 2, 2021.
Jay Z Makes Huge Investment in Smart Home Tech
Rapper, songwriter, businessman Jay-Z has reportedly made a huge investment in smart home tech recently. Through Marcy Venture Partners, Jay-Z sent $110 million into Wyze Labs’ coffers. That brings the smart home device maker’s total funding to date to $146 million. The smart home tech company, founded in 2017 by Amazon veterans, has more than 300 employees. The work Wyze is doing with AI and camera technology will definitely. benefit from the extra cash.
“We are doubling down and investing heavily to build world-class artificial intelligence into our camera products,” Wyze co-founder and Chief Marketing Officer Dave Crosby told GeekWire in a recent piece. “Just in the last year, our AI team has built person detection, vehicle detection, package detection and pet detection into our cameras. “Right now we have AI features in the works that we truly think will be game-changing for any camera, let alone one that costs less than $36.”
Smart Home Cameras, Baby Monitors Affected by Software Bug
A flaw in the ThroughTek “Kalay” network affects millions of IoT devices including smart baby monitors, DVRs, smart cameras, and other products.
this latest vulnerability allows attackers to communicate with devices remotely. As a result, further attacks could include actions that would allow an adversary to remotely control affected devices and could potentially lead to remote code execution.
Due to how the Kalay protocol is integrated by original equipment manufacturers (“OEMs”) and resellers before devices reach consumers, Mandiant is unable to determine a complete list of products and companies affected by the discovered vulnerability.
Smart Home Connectivity Standard ‘Matter’ Delayed to 2022
Matter, a connection standard for smart home devices backed by Apple, Amazon, Google, and others, has delayed its rollout until 2022.
Plume Manages Over One Billion Client Devices, as COVID-19 Inspires Huge Smart Home Growth
Over one billion unique client devices globally have been managed by Plume’s cloud controllers following huge growth in smart home devices.
Apple Supports Alliance to Unify Smart Home Devices
Apple, Amazon, and Google are supporting an industry alliance to make it easier for smart home devices from different brands work together.
An iCloud Issue, Home Automation, NFC Tags, and a Smart Home Friction Point, with Jeff Gamet - ACM 545
Bryan Chaffin and Jeff Gamet dig deep into smart home tech and home automation, starting with an iCloud account issue Jeff had with a new HomePod mini. They also discuss NFC tags, a home automation friction point Bryan has experienced, and other aspects of smart homes.
CES 2021: New Masks, Smart Home Gear – TMO Daily Observations 2021-01-14
John F Braun joins host Kelly Guimont to discuss CES coverage, including some new variations on masks and announced smart home gear.
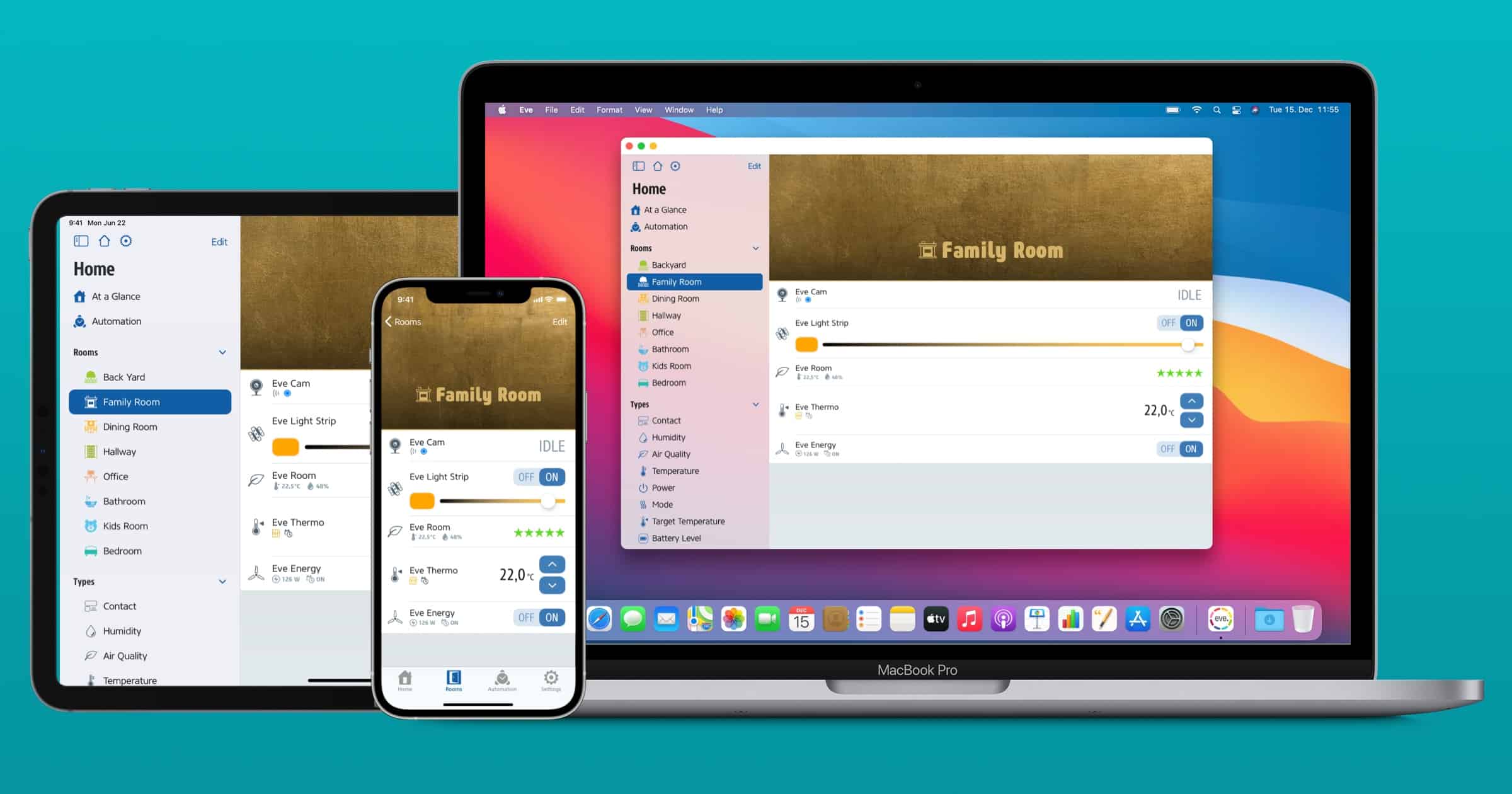
Smart Home App ‘Eve’ Supports M1 Macs With Version 5 Update
Eve for HomeKit version 5 is now available and supports M1 Macs as well as the screen resolutions of the new iPhone 12 product line.