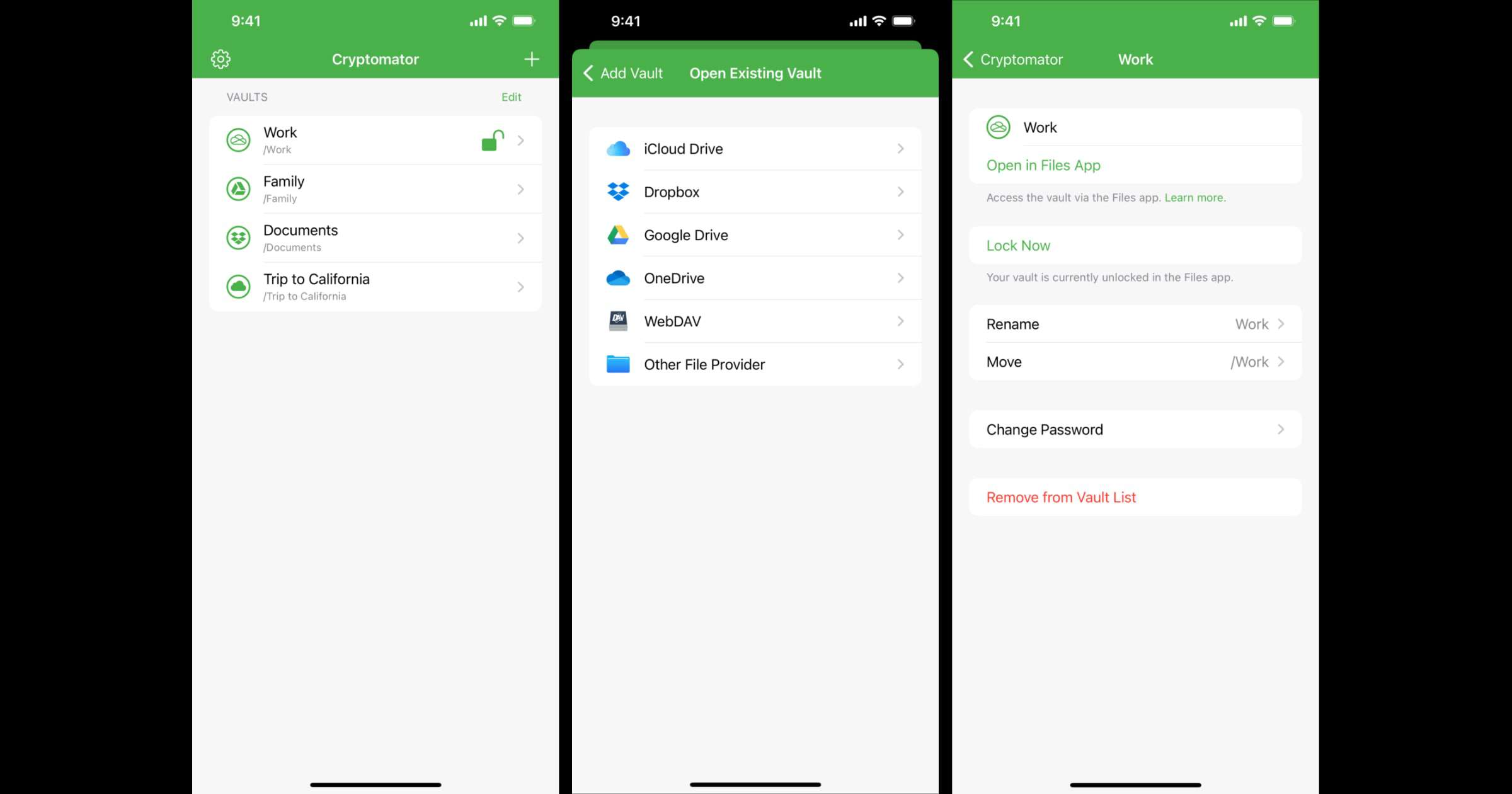
The team behind Cryptomator has rewritten the app in Swift, and with version 2.0 the app is completely integrated into the Files app. This means that your vaults are directly accessible from there. For example, you can now save and edit a Word document directly in an encrypted vault via the Files app. In addition, features like thumbnails, grid view, swiping through images, and drag & drop are possible with the new app. To summarize, Cryptomator gives you end-to-end encryption for your files. You can store them in Google Drive, iCloud Drive, Dropbox, and more. You can also store them offline in the Files app or on a hard drive.
privacy
Universal Control, App Privacy, and ArtSabers, with Jeff Gamet - ACM 564
Bryan Chaffin and Jeff Gamet geek out over ArtSabers and UltraSabers, two companies making light sabers! They also talk about Universal Control and how they would use it when Apple gets around to releasing it. And they look at the ever-changing world of app privacy.
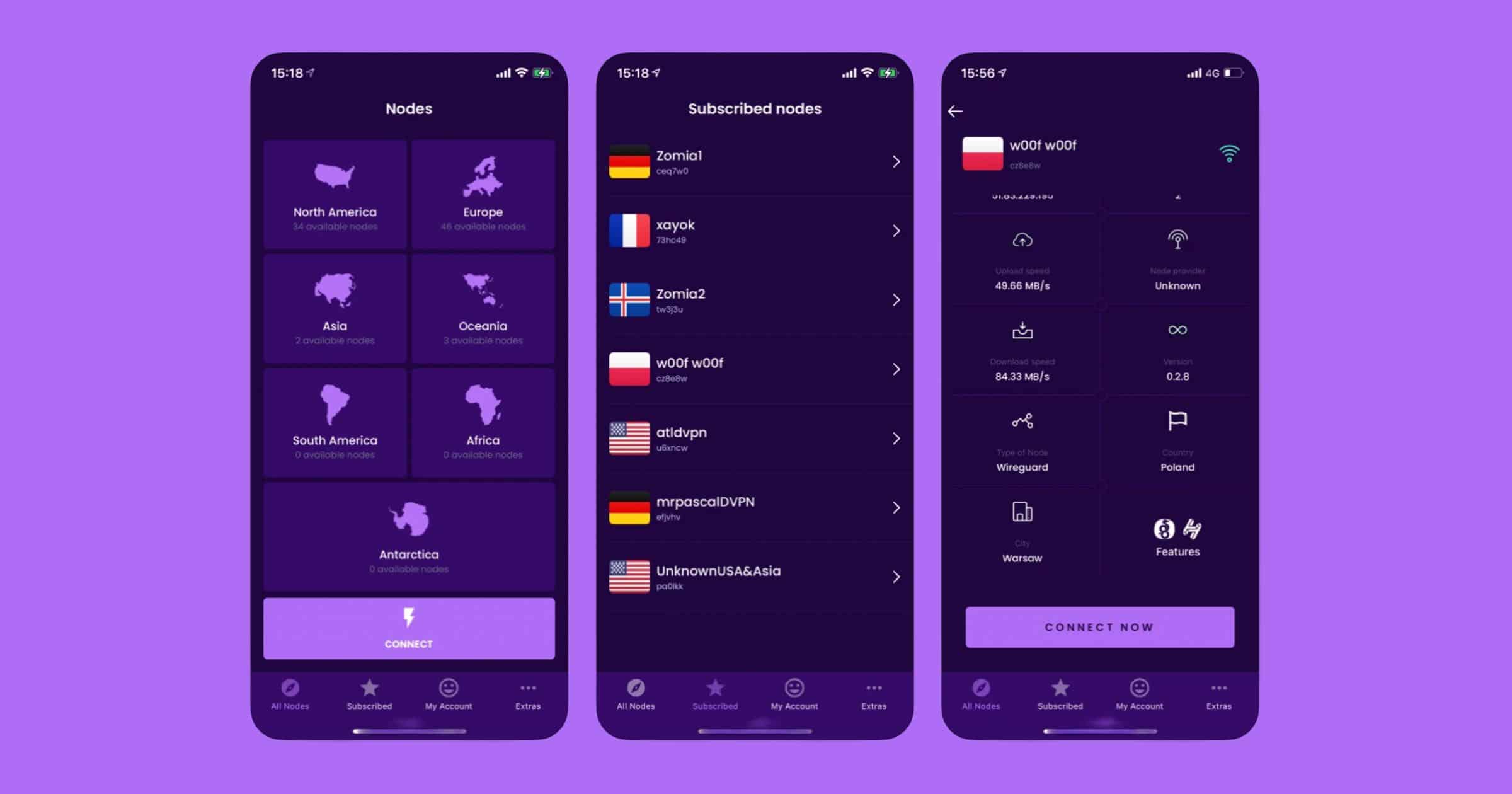
New VPN Called 'Exidio dVPN' Runs on Sentinel's Node Network
Exidio is a new decentralized VPN application that uses the Sentinel blockchain, which itself is part of the Cosmos ecosystem. “Exidio dVPN is rewriting the true definition of what it means to be a VPN. This is made possible by the Sentinel blockchain where all the global, distributed nodes are sharing their available and unused bandwidth. So as long as the Sentinel blockchain stays active, the network of nodes that offer bandwidth to the network remain active.” Exidio claims that traffic is end-to-end encrypted with proven no data logging.
Apple Removes Mention of CSAM Detection on Child Safety Page, Code Remains in iOS
Apple has removed any mention of its controversial CSAM detection plans in iCloud Photos, although the code remains in iOS.
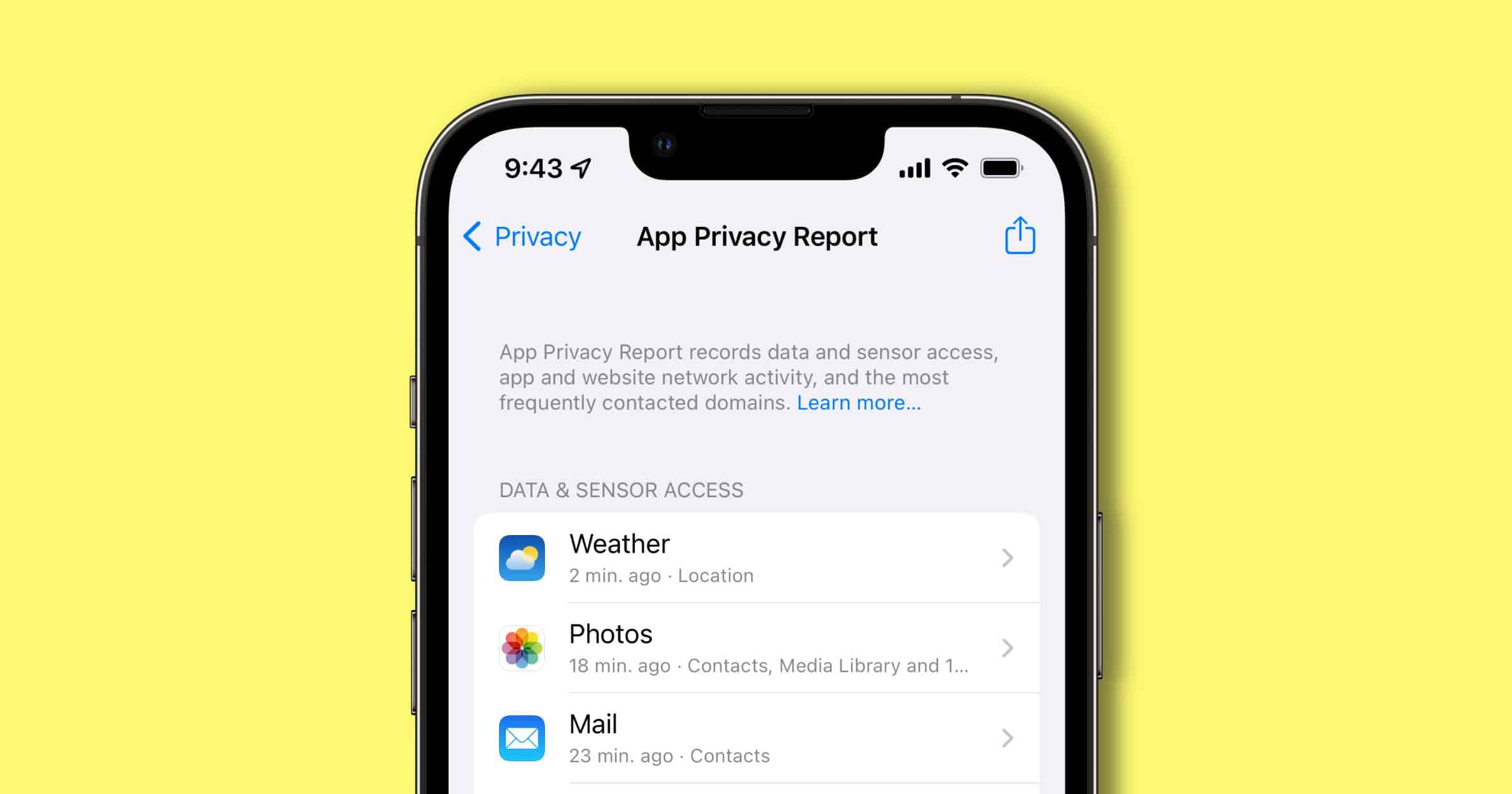
iOS 15.2 Update Finally Introduces the App Privacy Report
Apple released iOS 15.2 on Monday, and one of the changes you’ll see is App Privacy Report. You can install the update through Settings.
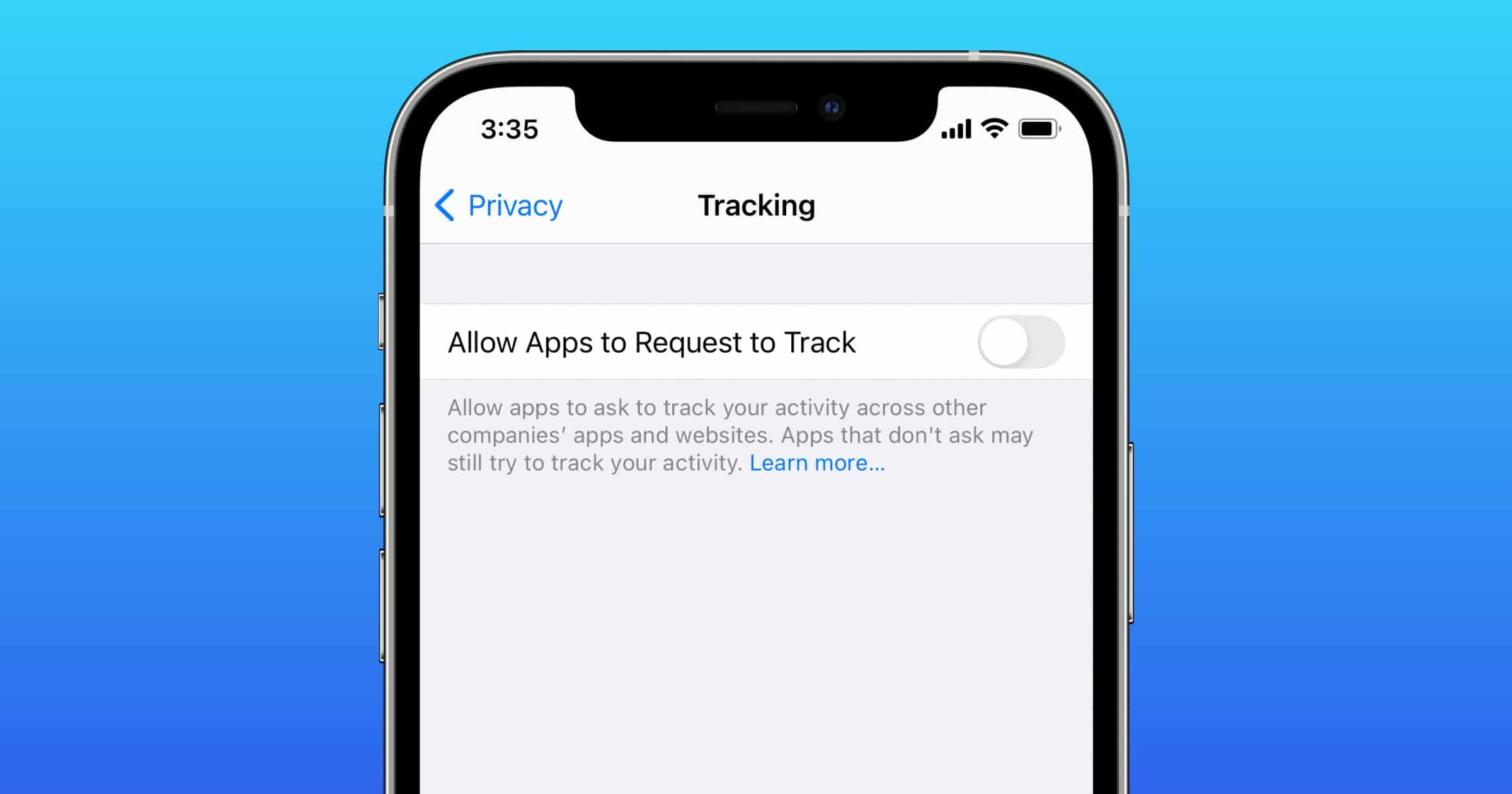
Poland Probes Apple's App Tracking Transparency Privacy Feature
Poland’s Office of Competition and Consumer Protection (UOKiK) is investigating Apple over its private feature App Tracking Transparency (ATT).
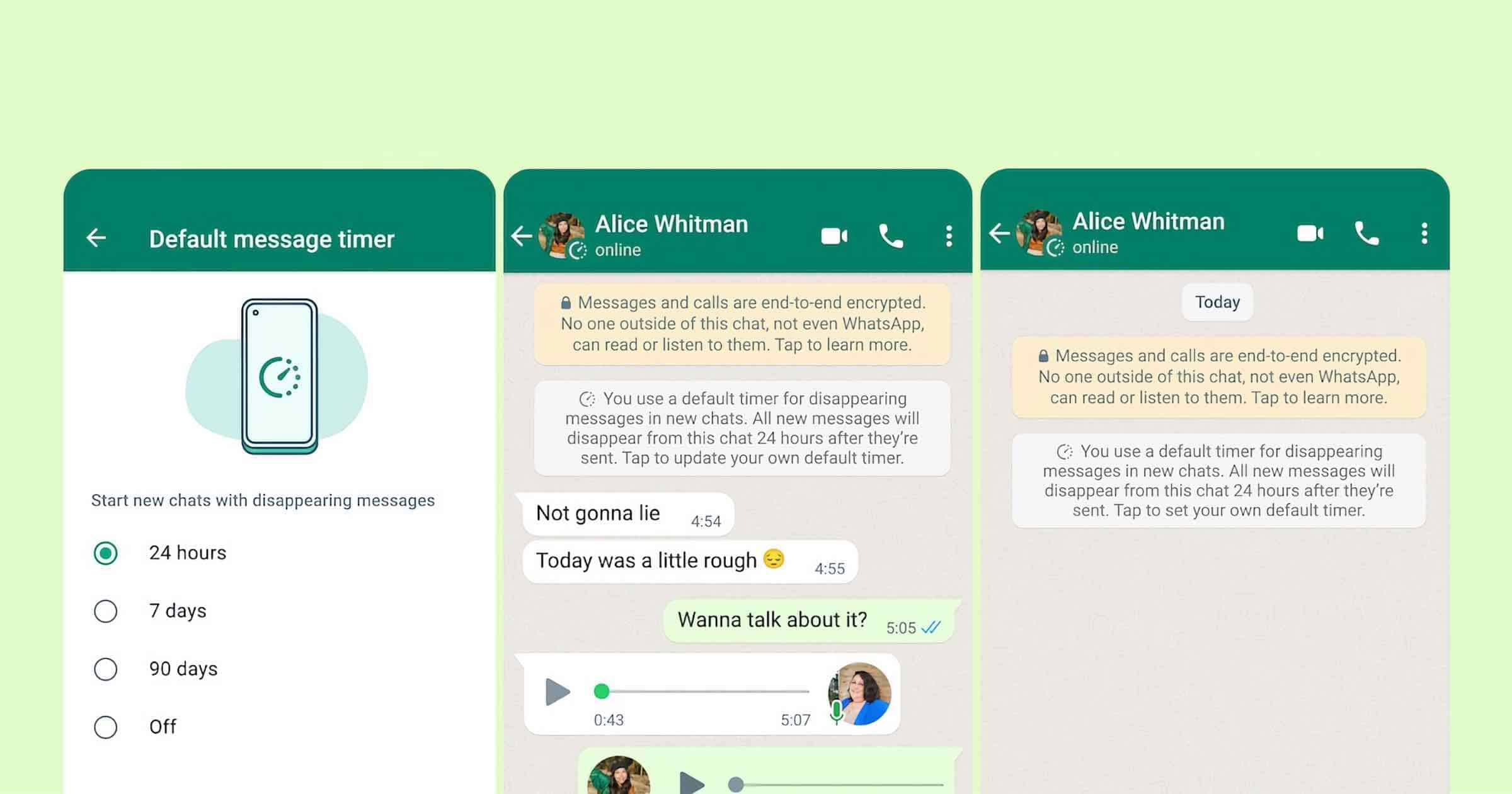
WhatsApp Users Can Enable Disappearing Messages by Default
WhatsApp is now letting users turn on disappearing messages for all chats by default.
Prior to Monday’s update, users had to manually enable ephemerality for each new chat with another individual. WhatsApp is additionally also giving users the option to have their messages disappear after 24 hours or 90 days, in addition to the seven-day period it originally introduced the feature with last year.
Verizon Automatically Tracks Your Data in New Update
In a new program called Verizon Custom Experience, the company is automatically opting customers in to track their data. But you can opt out.
A new program innocuously titled the “Verizon Custom Experience” is sold to users as a way for the company to “personalize our communications with you, give you more relevant product and service recommendations, and develop plans, services and offers that are more appealing to you.” To accomplish this, all a Verizon subscriber needs to do is… allow the company access to all the websites you visit, apps you use, as well as see everyone you happen to call and text.
Hundreds of Tor Servers From 'KAX17' Threaten to Deanonymize Users
Security researcher ‘Nusenu’ has uncovered hundreds of Tor servers belonging to an entity tracked as KAX17.
Grouping these servers under the KAX17 umbrella, Nusenu says this threat actor has constantly added servers with no contact details to the Tor network in industrial quantities, operating servers in the realm of hundreds at any given point.
KAX17’s focus on Tor entry and middle relays led Nusenu to believe that the group, which he described as “non-amateur level and persistent,” is trying to collect information on users connecting to the Tor network and attempting to map their routes inside it.
Twitter Now Bans Posting Images of People Without Their Consent
TechCrunch shares an update to Twitter’s private information safety policy regarding images posted on its platform. It bans sharing images and videos of private people without their consent.
This doesn’t mean that Twitter will require consent from all individuals in a photo or video before its posted. But if a person depicted wants the media taken down, Twitter will take it down.
'Libreddit' is a New Frontend Client for Reddit Designed for Privacy
Libreddit is a new frontend for Reddit, written in Rust, that aims to preserve privacy. The developer shared the service on r/Privacy. “Reddit tracks a lot of data but Libreddit logs nothing and uses no JavaScript by default so client-side monitoring isn’t possible. There are 35 community-hosted instances that can be used to access Libreddit; one can spread their traffic across multiple for even more privacy. 7 of our instances are .onion hidden services so you can browse Libreddit using Tor.” Official Instance: https://libreddit.spike.codes. If this gets too slow due to traffic, use another instance.
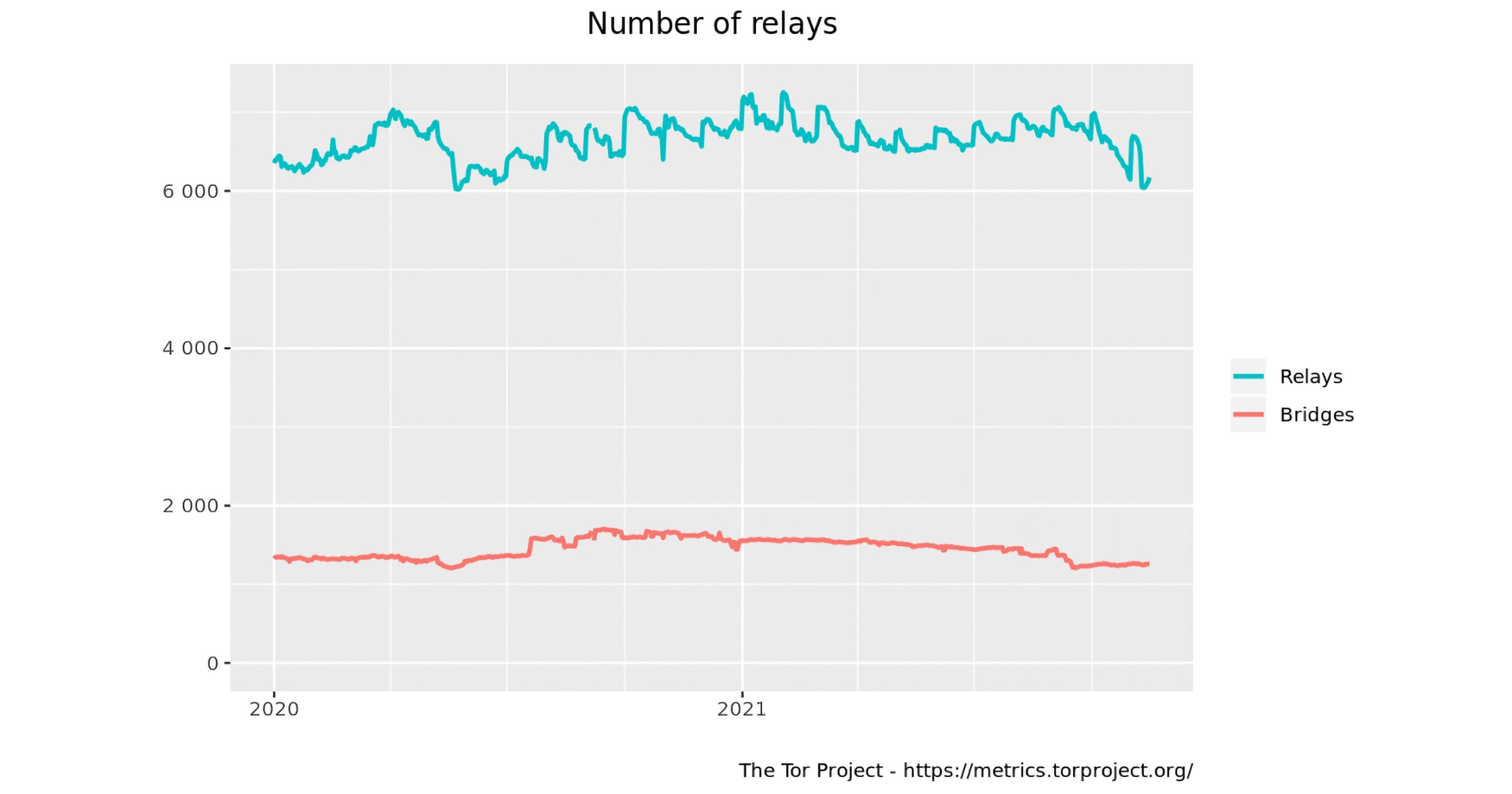
Tor Project Offers Rewards for More Servers During Decline
The Tor Project has seen a decline in relays and bridge servers, and offers rewards for people to help increase the network.
Rewards include the likes of hoodies, t-shirts, and stickers and are meant to provide some sort of meaningful gift to those who help keep the Tor anonymity network alive and resilient to censorship.
More specifically, the rewards will be provided to those who run Tor “bridges,” which serve as entry points into the Tor network for users located in countries that block access to Tor servers.
Musicians Call for Concert Venues to Drop Amazon Palm Scanning Technology
Musicians and activist groups are calling on Red Rocks Amphitheatre to stop its rollout of Amazon’s palm scanning tech.
The letter contributors are worried Amazon might send palm data to government agencies hoping to track activists and marginalized people, particularly in light of its past collaborations with police. They’re also concerned thieves might steal info from the cloud, and see AEG as inconsistent after it condemned the use of facial recognition in 2019.
Contract Lawyers Latest Sector to Face Remote Surveillance Programs
As WP reports, businesses are increasingly using surveillance software to monitor what their employees do on computers. Contract lawyers are the latest group to face this.
The monitoring is a symptom of “these pervasive employer attitudes that take advantage of these technologies to continue these really vicious cycles … that treat employees as commodities,” she said. “The irony in this situation is that it’s attorneys, who traditionally advocate for employee rights or justice when they’re made aware of intrusions like these.”
Proctoring Apps For Schools is Mass Surveillance for Kids
In an op-ed for Teen Vogue, writers from Fight For The Future argue that test proctoring apps that many schools use is mass surveillance of minors.
Remote proctoring software is, essentially, spyware that students are forced to install, typically as a browser plug-in or a computer program. Invasive features like keystroke logging, screen recording, network traffic monitoring, and video and audio recording are common. Many of the programs also collect tons of biometric data through eye-movement tracking and facial recognition.
Peloton Latest to Complain That Apple Privacy Hurts Ability to Target Users
Peloton recently held an earnings call and mentioned that Apple’s privacy features with iOS have negatively affected its ad revenue.
Facebook Moves to Cancel its Facial Recognition System
Facebook announced it will cancel its facial recognition system responsible for cataloging its billion-strong user base.
Our technology will no longer automatically recognize if people’s faces appear in Memories, photos or videos. People will no longer be able to turn on face recognition for suggested tagging or see a suggested tag with their name in photos and videos they may appear in. We’ll still encourage people to tag posts manually, to help you and your friends know who is in a photo or video. This change will also impact Automatic Alt Text (AAT), a technology used to create image descriptions for people who are blind or visually impaired. AAT currently identifies people in about 4% of photos.
The above quote is probably the only useful part of the self-congratulatory update.
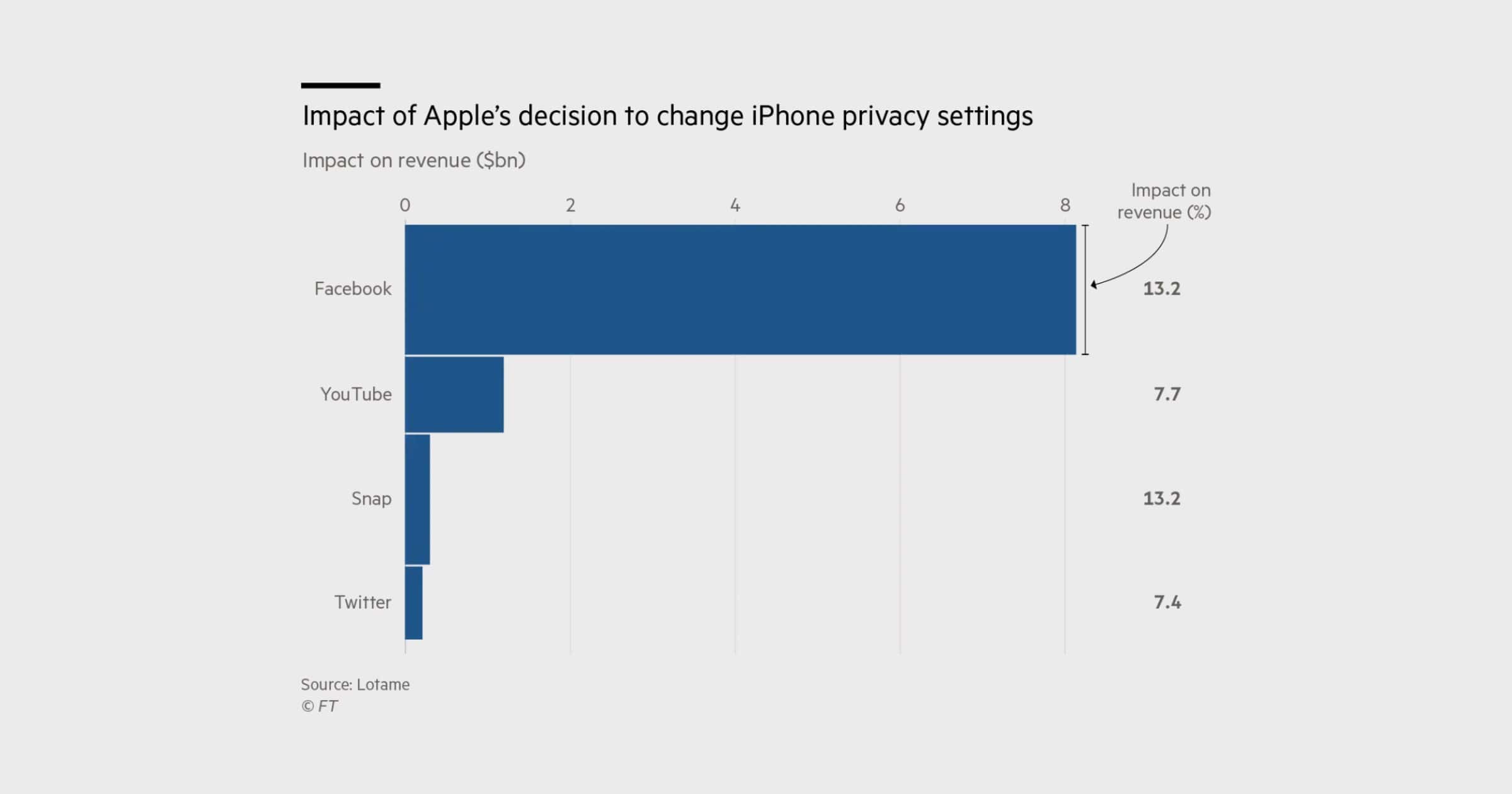
Privacy Features Cause Social Media Companies to Lose $10 Billion in Ad Revenue
User consent, through tools like Apple’s App Tracking Transparency, isn’t good for business. Some companies lost US$10 billion as a result.
Blockchains Aren't as Private as You Think, But They Could Be
Cybersecurity expert Mashael Al Sabah was recently featured on MIT’s Business Lab podcast. She talks about privacy issues with blockchain technology and how they can be fixed. You can listen to the podcast with the link below (direct link on Apple Podcasts), and.or read the podcast transcript.
A lot of people think that they are completely anonymous when they use Bitcoin, and this gives them a false sense of security. In our research, what we did is that we crawled social media, like there’s popular forum for Bitcoin users called Bitcointalk.org, and we crawled Twitter as well for Bitcoin addresses that users attributed to themselves. In some forums, people share their Bitcoin addressees along with their profile information. So, now you have the public profile information, which includes usernames, emails, age, gender, city.
Apple and China and Apps – TMO Daily Observations 2021-10-27
Charlotte Henry joins host Kelly Guimont to discuss the iOS App Store in China, and the sudden disappearance of particular apps.
Minors Can Now Request Photo Removal From Google Search
Google says that minors, or their parents, can now request their photos be removed from Google Search as a new privacy feature.
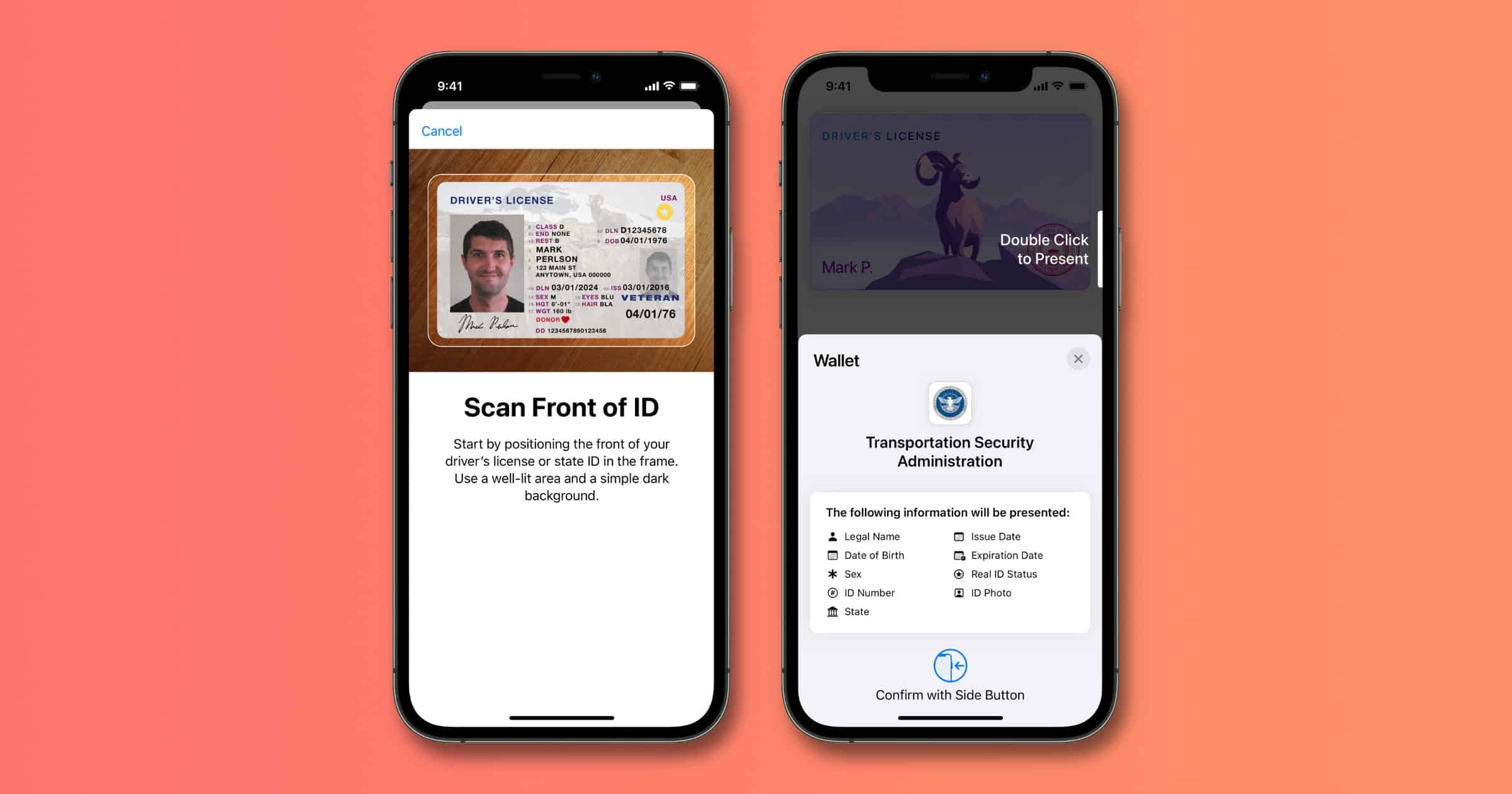
ISO Approves and Publishes Standard for Mobile Driver's License
The International Organization for Standardization has approved and published ISO/IEC 18013-5 for mobile driver’s licenses and mobile IDs.
ATT Might Mean Apple Wants to Challenge Facebook and Google in Online Ads
The App Tracking Transparency privacy feature might indicate that Apple is looking to mount a challenge in online advertising.