The latest move in modernizing the U.S. government sees the new Bureau for Cyberspace and Digital Policy open its doors for the first time.
government
New Malware Coming Through Email Posing as IRS
A new phishing scam posing at the IRS is making the rounds through email. Infamous botnet Emotet is behind many of the attacks.
FBI Launches Virtual Asset Exploitation Team
The U.S. Federal Bureau of Investigation is launching the Virtual Asset Exploitation Team (VAXU) to investigate crypto-crime.
Missouri Backs Away From 'View Source' Hacking Prosecution
A Cole County prosecutor has declined to prosecute reporter Josh Renaud over claims that he hacked into the state’s website.
Senators Reveal CIA Program That Collects American Data
According to two Democrats on the Senate Intelligence Committee, the CIA has an undisclosed repository of data collected from Americans.
IRS Will No Longer Require Facial Recognition for Taxes
Backpedaling among public backlash, the IRS won’t require citizens to use facial recognition for taxes, The New York Times reported.
Officials Accuse Apple of Lying About NDA Concealment Clauses
Eight state treasurers have accused Apple of lying about concealment clauses, in a letter to SEC Chairman Gary Gensler.
The EARN It Act is Back and Coming for Social Media Companies
Senators Lindsey Graham (R-SC) and Richard Blumenthal (D-CT) have reintroduced their EARN It Act. The bill aims to reform Section 230.
Treasury Considers ID.Me Alternatives Over Privacy Concerns
The Treasury Department is looking into ID.me alternatives for accessing the IRS website over privacy concerns.
CEO Blake Hall this week said that the company also used one-to-many technology, which compares selfies taken by users as part of the verification process against a larger database. The company said it maintained an internal database of selfies taken by users and compared new selfies against it using Amazon’s controversial Rekognition technology. As of January 25, 20.9 million users’ selfies had been verified against that database, the company said.
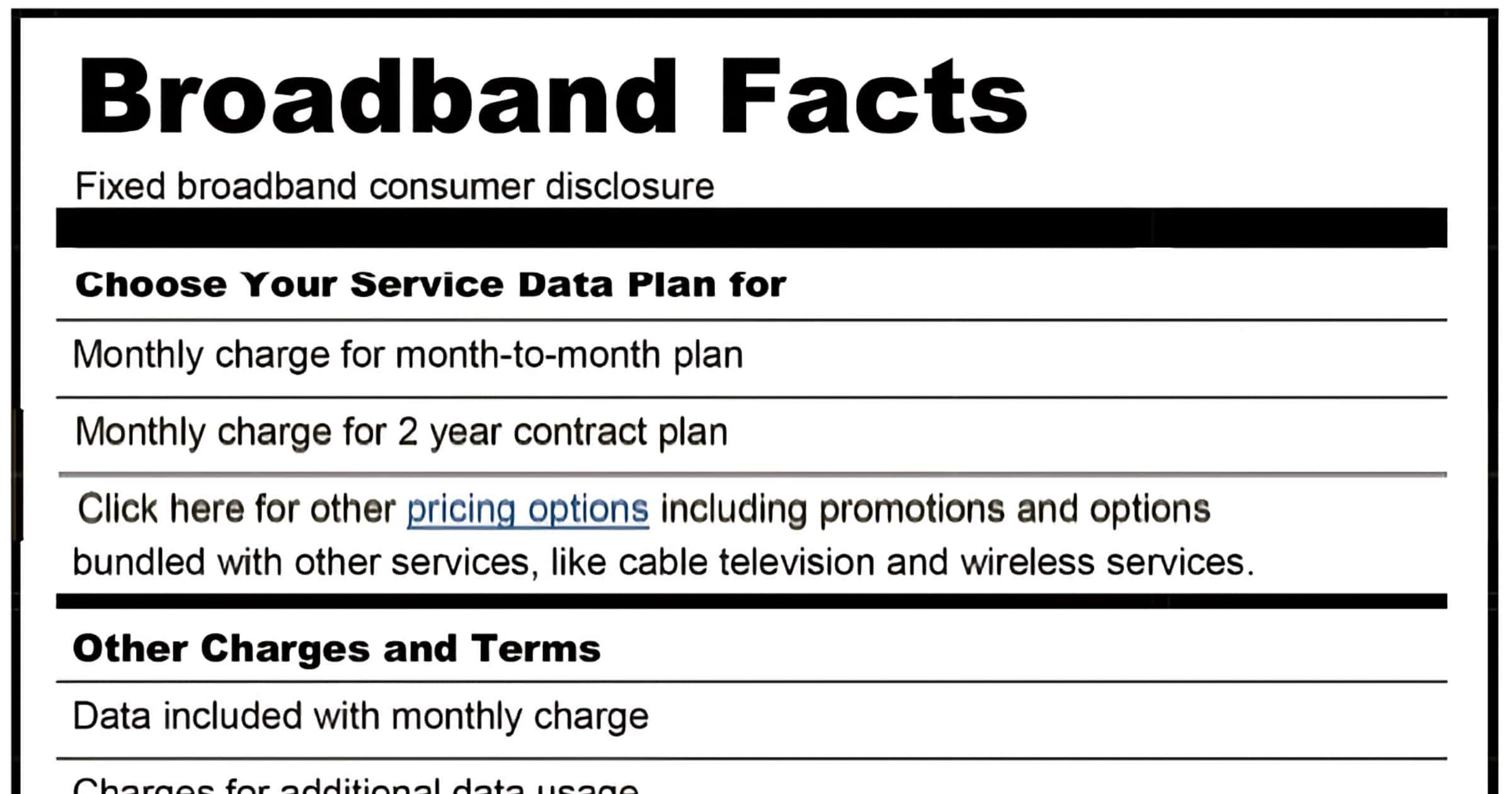
FCC Now Requires Broadband Nutrition Labels for Consumers
The FCC will force ISPs to disclose broadband “nutrition labels” to give information on prices, introductory rates, data allowances, broadband speeds, and management practices.
The law directs the Commission “to promulgate regulations to require the display of broadband consumer labels, as described in the Public Notice of the Commission issued on April 4, 2016 (DA 16–357), to disclose to consumers information regarding broadband Internet access service plans.” Id. See also Consumer and Governmental Affairs, Wireline Competition, and Wireless Telecommunications Bureaus Approve Open Internet Broadband Consumer Labels, GN Docket No. 14-28, Public Notice, 31 FCC Rcd 3358 (CGB/WCB/WTB 2016) (2016 Public Notice).
How the 'America COMPETES' Act Could Affect Cryptocurrency
A provision in the America COMPETES Act would give the Treasury unchecked power to ban cryptocurrencies, reports Coin Center.
'Open App Markets Act' Would Have Unintended Side Effects, Warns ITIF
The Information Technology and Innovation Foundation warns Congress about unintended consequences of the Open App Markets Act.
Congress Explores Blockchain Energy Usage From Mining
On January 20, the Oversight and Investigations subcommittee of the U.S. Congress House Energy and Commerce Committee discussed blockchain energy usage and other concepts related to mining and consensus.
Representatives then took to the floor with statements and questions. A few used their time for partisan attacks and political grandstanding, yet most made an honest effort to ask questions that either tackled the energy-related issues at the core of the hearing or sought broader context on the uses and potential applications of blockchain technology.
Federal Reserve Releases Paper on Digital Dollar, Seeks Public Comment
The Federal Reserve has released a 40-page paper [PDF] on its study of a digital dollar. It seeks public comment as it takes no position at this time.
Instead, it provides an exhaustive look at benefits such as speeding up the electronic payments system at a time when financial transactions around the world already are highly digitized. Some of the downside issues the report discusses are financial stability risks and privacy protection while guarding against fraud and other illegal issues.
Big Tech Nervous About 'American Innovation and Choice Online Act'
The Senate Judiciary Committee is set to deliberate on the American Innovation and Choice Online Act (AICO), a bill aimed at Big Tech.
IRS and ID.me Makes Video Selfies a Requirement in 2022
The IRS is requiring people create an account with ID.me to access and submit taxes. One of the verification methods is a video selfie
US Antitrust Enforcement Opens for Public Comment by Agencies
The U.S. Justice Department and Federal Trade Commission (FTC) want to improve the currently antitrust enforcement in the country.
Report Reveals UK Government Push to Attack Encrypted Messengers
The UK government plans an advertising campaign to attack messaging apps that use end-to-end encryption. The details were published recently.
Russian Authorities Arrest Members of REvil Ransomware Group
The Russian Federal Security Service (FSB) announced on Friday that it has arrested 14 members of the REvil ransomware group.
Congress Introduces 'TLDR' Bill to Combat Confusing Terms of Service
It wants to change the trope with Terms of Service conditions written in “legalese” language incomprehensible for many users
White House Meets With Software Companies Over 'Log4j' Cybersecurity Concerns
Officials at the White House are meeting with companies such as Apple, Apache, and others to talk about cybersecurity in the wake of Log4j.
Beware of Fake QR Codes on Parking Meters That Steal Your Money
Scammers are targeting unwary people with fake QR codes found on parking meters. The report centers on a couple of cities in Texas.
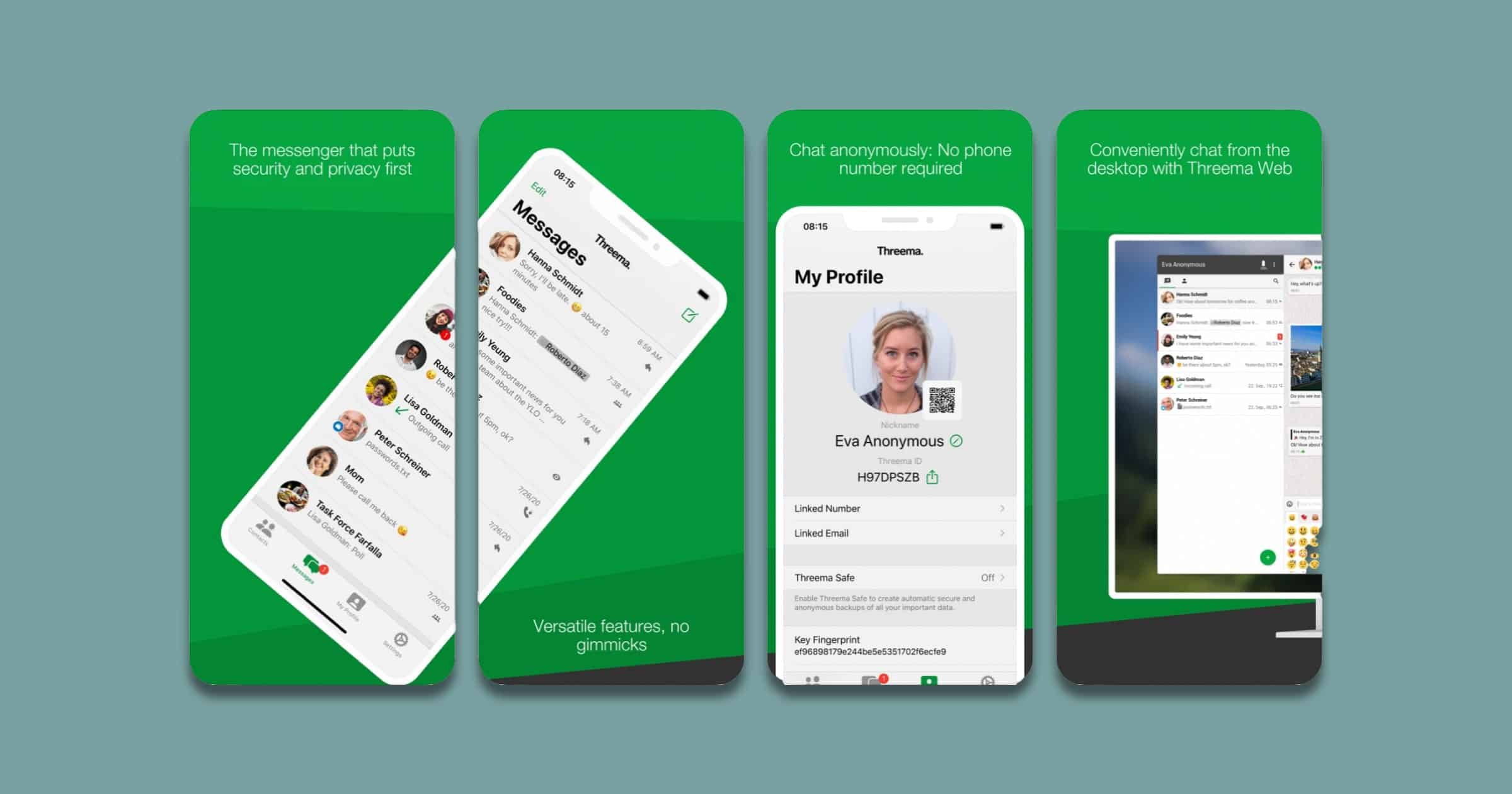
Swiss Army Seeks Private Messenger 'Threema' Over WhatsApp
Switzerland’s army told its soldiers not to use foreign messengers such as WhatsApp, due to privacy concerns. Instead, the recommendation is to use private messenger Threema, a Swiss app.
Army spokeswoman Delphine Schwab-Allemand, in an e-mail on Wednesday confirming reports on the issue in Swiss media, seemed to soften the army’s position, saying that there was a “recommendation” that troops use Threema. It took effect on Jan. 1. She added that the army cannot and does not want to tell troops to use a particular app on their private devices.
Dapper Labs First NFT Company to Register as Lobbyist for US Government
Vancouver-based Dapper Labs has recruited Crossroads Strategies as a lobbying firm. The NFT company is the first of its kind to do so.
The company reported that it would lobby for “Policy related to NFTs, blockchain and financial services.” Aside from recruiting a lobbying firm, Dapper Labs also recruited Alison Kutler as its new head of government affairs back in November 2021. Kutler is the former chief of the Consumer and Governmental Affairs Bureau and special advisor to the chairman of the FCC from June 2015 to Apr 2017.