The European Union (EU) has given Apple the green light to open up its mobile payments system and let competitors use the iPhone’s NFC.
NFC
NFC on iPhones and Apple Watches Likely To Expand Beyond Apple Pay
Contactless iPhone Payments May Be Just Around The Corner
Contactless iPhone payments could be enabled in a future iOS update, Mark Gurman wrote on Wednesday. It means that small business could accept credit card payments directly with an iPhone, without needing a terminal such as Square. Jeff Butts has more information here.
In order to accept payments on an iPhone today, merchants need to use payment terminals that plug in or communicate with the phone via Bluetooth. The upcoming feature will instead turn the iPhone into a payment terminal, letting users such as food trucks and hair stylists accept payments with the tap of a credit card or another iPhone onto the back of their device.
Understanding NFC, Apple Pay, and the EU’s Complaint
The EU is citing Cupertino for antitrust concerns related to its NFC Apple Pay exclusivity. Let’s look at what all that really means.
Reading AirTag NFC's: A Hidden Feature
Did you know Apple Support says you can read the NFC data in an AirTag just by holding it to the top of your iPhone? Learn more in Mac Geek Gab 885, and check out this week from Dave Mark too!
An iCloud Issue, Home Automation, NFC Tags, and a Smart Home Friction Point, with Jeff Gamet - ACM 545
Bryan Chaffin and Jeff Gamet dig deep into smart home tech and home automation, starting with an iCloud account issue Jeff had with a new HomePod mini. They also discuss NFC tags, a home automation friction point Bryan has experienced, and other aspects of smart homes.
Rolling With Wi-Fi — Mac Geek Gab 859
Sometimes you’ve gotta go… and sometimes — make that ALL the times — you need Wi-Fi. Never fear, John and Dave are here to help answer the tough (and fun) questions. Listen as your two favorite geeks pour through the mailbag, trying to answer as many of your questions as possible in the time we all have together each week. Don’t forget to send in your questions: [email protected] and they’ll answer yours, too!
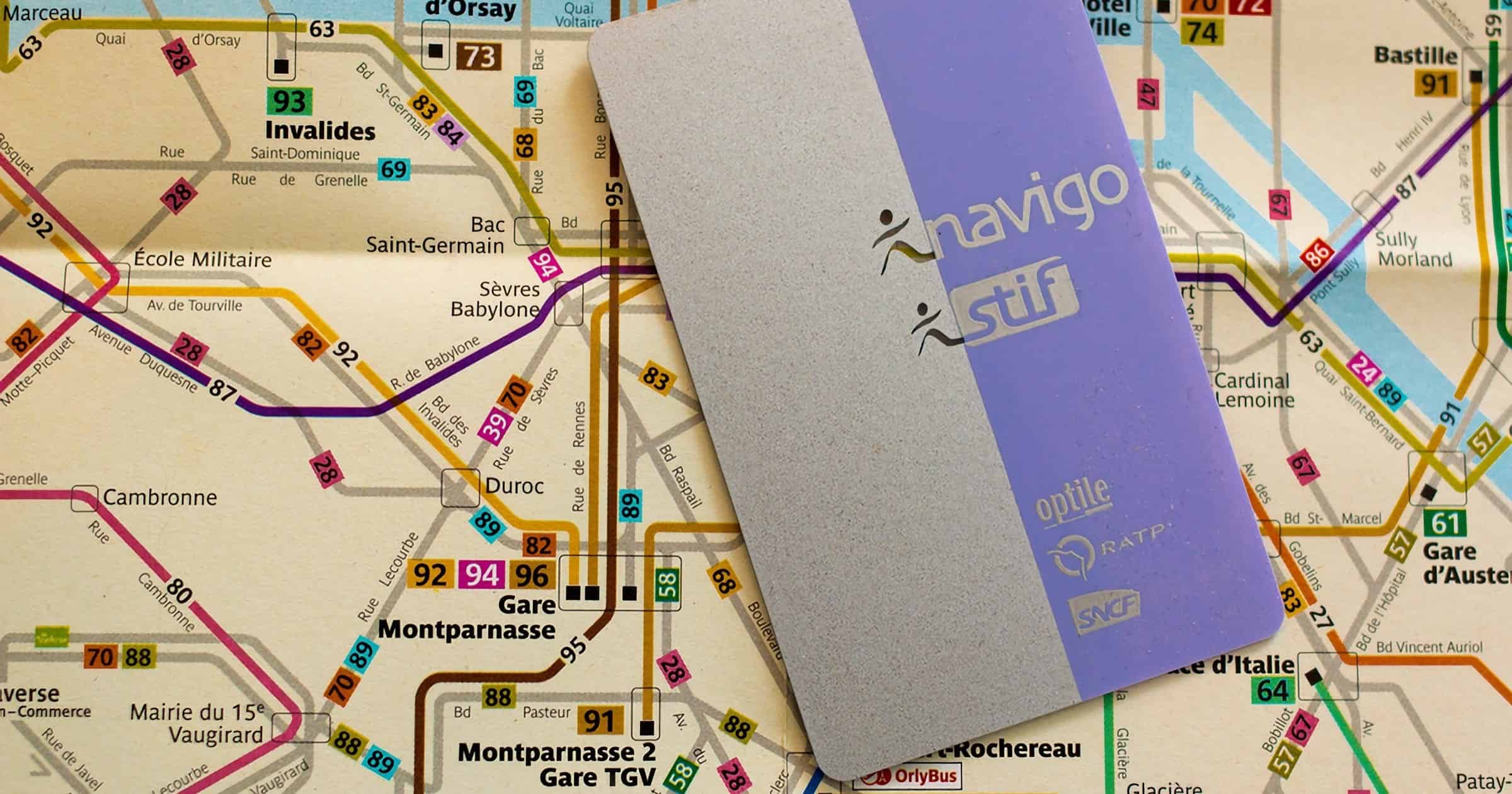
France’s Navigo Card Arrives on iPhone in February
Residents in the Île-de-France region will be able to add their Navigo pass on their iPhone in February and use them at train access terminals.
Should Apple Open its NFC Chip to Third Parties?
Karen Webster writes about Apple’s position in the payments industry and how Apple’s restriction of its NFC chip has hurt consumers.
Granted, it’s always hard to prove a negative, but not having access to the NFC chip has likely prevented innovators from investing time and money in developing the innovations that could have made the in-store POS experience better for iPhone users. And since iPhone users skew more to the affluent, it also denied those innovators the opportunity to monetize their spend.
Dutch Antitrust Probe Targets Contactless Payments Like Apple Pay
The Netherlands Authority for Consumers and Markets announced on Friday the start of an investigation into payment apps and NFC.
NFC Devices Could Soon Charge Smaller Devices With WLC Specification
Today The NFC Forum introduced a specification that would allow smartphones and tablets to charge smaller devices using NFC.
Yubico Authenticator iOS App Now Supports NFC
While Yubico has a security key that plugs into your iPhone via Lightning, the app also supports NFC YubiKeys now.
Instead of storing the time-based one-time passcodes on a mobile phone or computer, Yubico Authenticator generates and stores one-time codes on the YubiKey. A user must present their physical key in order to receive the code for login. This not only eliminates security vulnerabilities associated with a multi-purpose computing device, but also offers an added layer of convenience for users that work between various machines.
Germany Forces Apple to Open NFC to Third-Party Payment Apps
Germany has forced Apple to open its NFC capabilities on iPhones so that third-party payment apps can compete better with Apple Pay.
iCloud Keychain vs. Catalina Cage Match – Mac Geek Gab 786
Today, your two favorite geeks dig into your questions about recovering photo data, removing malware, resolving iCloud Keychain in macOS Catalina, and more. But that’s not all! You’ve got some great tips for automating those un-automatable Personal Reminders, fixing DNS, Mono Podcast Listening, and creating disk images. All of this and more from Dave Hamilton and John F. Braun, as soon as you press play. Do it now and don’t get caught!
A Cashless Society Could Affect Strippers and Other Sex Workers
I’ve written musings here and there about the cashless society, but sex work as an affected industry hadn’t crossed my mind. I think it’s an important conversation to have, though. I wonder what an alternative could be? Special jewelry with NFC chips that can accept peer-to-peer payments? Imagine tipping a stripper with Apple Pay. Sorry Tim Cook.
But without cash, the club I work at is free to exploit. Cash handed directly to a dancer gets pocketed, but credit card charges are skimmed—and because workers are more or less off the books, we have no recourse to contest absurdly high fees. When a customer pays several hundred dollars to spend time in a dark room alone with a dancer, the club takes a 70 percent cut.
iOS 13 NFC Enables More ID Scanning
Last week we reported that iOS 13 NFC will support Japanese identity cards. Now the German Federal Ministry of Interior announced support for its ID cards as well.
The Federal Ministry of the Interior, for construction and homeland welcomes this important step. This will soon allow users of Apple’s mobile devices to benefit from digital sovereign applications such as ID, ePass, and eVisum [including] in person checks at international airports.
This Fall, Japanese iPhone Users Will Use iOS 13 NFC
Japan plans to use iOS 13 NFC capabilities so that Japanese iPhone users can access Individual Number Cards from their iPhone.
New Apple Pay NFC Stickers Make it Faster to Pay
Jennifer Bailey, VP of Apple Pay, announced Apple Pay NFC stickers recently.. Once tapped they trigger Apple Pay purchases, so you don’t need to download a separate app.
With the new support, an iPhone will know how to read a specially-encoded NFC tag (that can be as inert as a sticker) and automatically show the Apple Pay purchase interface when a user holds their device near it. No third-party apps or other set up required.
At launch Apple is partnering with Bird scooters, Bonobos clothing store, and PayByPhone parking meters.
CES - Identify Your Stuff, and Help Others Return Your Lost Stuff with iTag
LAS VEGAS – Howe High Tech showed iTag, a system which uses small NFC tags to identify your stuff, and help others return your lost stuff.
Apple Store to Sell New L'Oréal UV Sensor
It works with an app to measure the wearer’s exposure to UV radiation.
Apple Pay Dominance, NFC in HomePod - TMO Daily Observations 2018-07-31
Dave Hamilton and Andrew Orr join Jeff Gamet to look at Apple Pay’s projected dominance in contactless payments, plus Andrew explains why he’d like to see NFC in Apple’s HomePod.
The Milan Metro System Added Apple Pay Support
New contactless terminals in the underground subway system work with Visa and MasterCard credit and debit cards.
Tech Chat with MGG's Dave Hamilton and John F Braun - TMO Daily Observations 2018-06-22
John F. Braun and Dave Hamilton from Mac Geek Gab join Jeff Gamet to talk tech about NFC, Apple Pay, digital keys, breathing new life into older Macs, and more.
Apple Wants Your iPhone to be Your Car Key
The Car Connectivity Consortium’s Digital Key 2.0 specification could turn your iPhone into your next car key.